Huawei H12-724 - HCIP-Security (Fast track) V1.0
Regarding the 3 abnormal situations of the file type recognition result, which of the following option descriptions is wrong?
Due to differences in network environment and system security strategies, intrusion detection systems are also different in specific implementation. From the perspective of system composition, the main
Which four major components are included?
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.
Regarding the enhanced mode in HTTP Flood source authentication, which of the following descriptions are correct? Multiple choices
In the security protection system of the cloud era, reforms need to be carried out in the three stages before, during and after the event, and a closed-loop continuous improvement should be formed.
And development. Which of the following key points should be done in "things"? (multiple choice)
In the Policy Center strategy configuration, how many violations rating of definition are there?
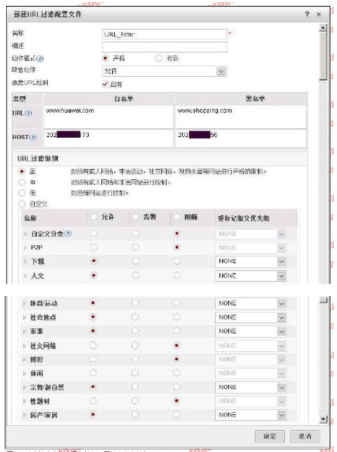
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
Which of the following options are correct for the configuration description of the management center ATIC? (multiple choice)
Which of the following signature attributes cannot be configured for IP custom signature?
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.



