Huawei H12-821_V1.0 - HCIP-Datacom-Core Technology V1.0
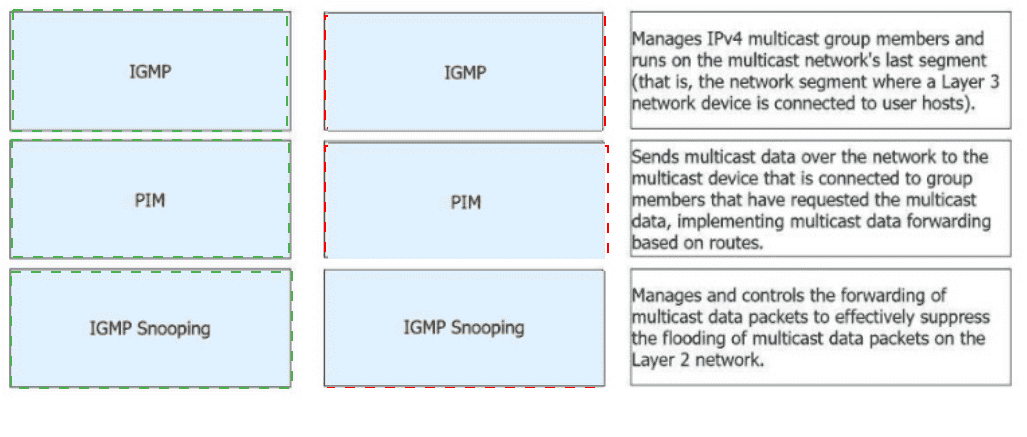
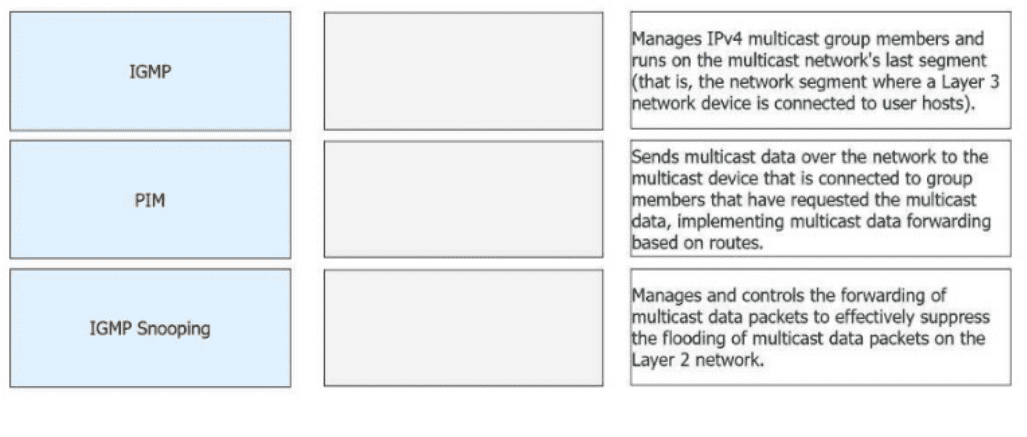
Match the following IPv4 multicast protocols with the corresponding functions.
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
A BGP device receives a route carrying an unknown attribute from a peer but does not know whether other devices need the attribute. In this case, the BGP device retains this attribute when advertising the route to other peers. Which of the following attributes is of this type?
In addition to numerous normal service packets, the CPUs of devices on a network may also receive large numbers of attack packets. To ensure that the CPUs can properly respond to normal services, the devices provide the local attack defense function.
Which of the following statements are true about this function?(Select all that apply)
Which of the following statements regarding the firewall zone security level is false?
In VRRP networking, if VRRP is not configured to track an uplink interface and the uplink interface or link of the master device in a VRRP group fails, no switchover will be triggered. As a result, a traffic blackhole occurs.
OSPF has several types of special areas, which are used to reduce the LSDB size and improve device performance.
Which of the following LSAs cannot be in a totally stub area?
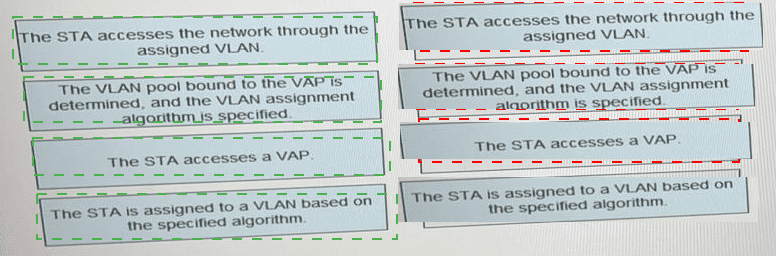
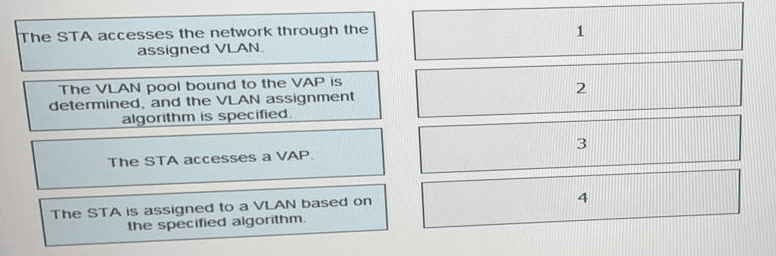
What is the correct procedure for a VLAN pool to assign terminals to VLANs.
On a network, some switches are enabled with RSTP and some switches are enabled with STP. What will happen?
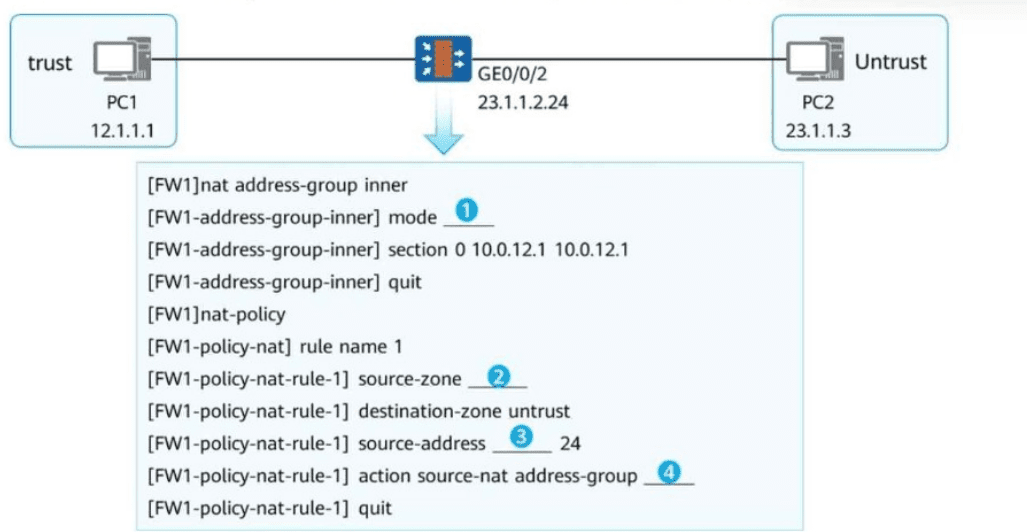
To enable PC1 to access PC2 using the IP address of the firewall's GE0/0/2, you need to configure NAPT for source address translation. In the following figure, fill in the blank to complete the command.