Huawei H12-921_V1.0 - HCIE-Data Center Network (Written) V1.0
Which of the following features can be used in the Cloudfabric centralized storage NoF+ solution to manage the connected hosts and storage nodes?
IN THE CLOUDFABRIC SOLUTION, WHEN USING MDC TO ROW AWS HAS A CLOUD NETWORK, IGWS IN THE AWS TYPE WILL BE PROJECTED AS WHICH OF THE FOLLOWING OPTIONS? ?
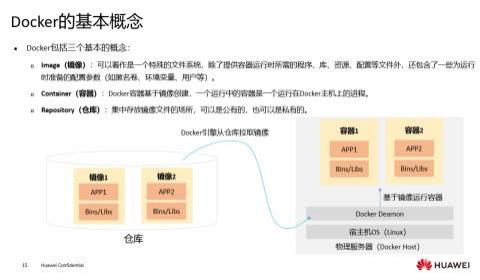
What is correct about the following description of Docker?
In the Huawei CloudFabric solution, the network controller uses the NETCONF device to deliver configurations. Which of the following encodings does NETCONF information use?
When service packets are connected to a VXLAN network through a Layer 2 sub-interface, different flow encapsulation types need to be configured on different Layer 2 sub-interfaces
The same physical interface can access different data packets. Which of the following is NOT a stream encapsulation type that is supported by a Layer 2 sub-interface?
Which of the following Linux namespaces implements process IDs that can be duplicated but do not affect each other?
Which of the following components of the CloudFabric Intelligent Lossless Network Solution for Multi-Computing Scenarios needs to support lossless features such as AI ECN to improve network performance?
Which of the following descriptions of CloudFabric component deployments is correct?
Which of the following descriptions of VNI in a VXLAN network is correct?
What are the correct items in the following description of lossless network architecture design in multivariate computing scenarios?