HashiCorp HCVA0-003 - HashiCorp Certified: Vault Associate (003)Exam
You’ve hit the URL for the Vault UI, but you’re presented with this screen. Why doesn’t Vault present you with a way to log in?
How can Vault be used to programmatically obtain a generated code for MFA, somewhat similar to Google Authenticator?
Which scenario most strongly indicates a need to run a self-hosted Vault cluster instead of using HCP Vault Dedicated?
You want to encrypt a credit card number using the Transit secrets engine. You enter the following command and receive an error. What can you do to ensure that the credit card number is properly encrypted and the ciphertext is returned?
$ vault write -format=json transit/encrypt/creditcards plaintext="1234 5678 9101 1121"
Error: * illegal base64 data at input byte 4
Given the following policy, which command below would not result in a permission denied error (select two)?
path "secret/*" { capabilities = ["create", "update"] allowed_parameters = { "student" = ["steve", "frank", "jamie", "susan", "gerry", "damien"] } }
path "secret/apps/*" { capabilities = ["read"] }
path "secret/apps/results" { capabilities = ["deny"] }
Which of the following secrets engines does NOT issue a lease upon a read request?
During a service outage, you must ensure all current tokens and leases are copied to another Vault cluster for failover so applications don’t need to authenticate. How can you accomplish this?
A Jenkins server is using the following token to access Vault. Based on the lookup shown below, what type of token is this?$Â vault token lookup hvs.FGP1A77Hxa1Sp6Pkp1yURcZB
Â
Key Value
--- -----
accessor RnH8jtgrxBrYanizlyJ7Y8R
creation_time 1604604512
creation_ttl 24h
display_name token
entity_id n/a
expire_time 2025-11-06T14:28:32.8891566-05:00
explicit_max_ttl 0s
id hvs.FGP1A77Hxa1Sp6KRau5eNB
issue_time 2025-11-06T14:28:32.8891566-05:00
meta
num_uses 0
orphan false
path auth/token/create
period 24h
policies [admin default]
renewable true
ttl 23h59m50s
type service
How long does the Transit secrets engine store the resulting ciphertext by default?
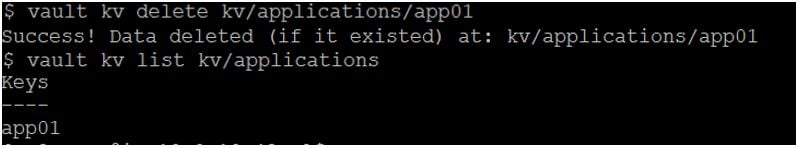
After issuing the command to delete a secret, you run a vault kv list command, but the path to the secret still seems to exist. What command would permanently delete the path from Vault?