IIA IIA-ACCA - ACCA CIA Challenge Exam
According to IIA guidance, which of the following would be the best first step to manage risk when a third party is overseeing the organization's network and data?
Which of the following is the most appropriate test to assess the privacy risks associated with an organization's workstations?
Refer to the exhibit.
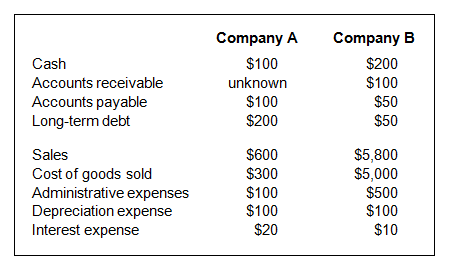
Presented below are partial year-end financial statement data (000 omitted from dollar amounts) for companies A and B:
If company A has a quick ratio of 2:1, then it has an accounts receivable balance of:
A software that translates hypertext markup language (HTML) documents and allows a user to view a remote web page is called:
A capital investment project will have a higher net present value, everything else being equal, if it has:
Which of the following are typical audit considerations for a review of authentication?
1. Authentication policies and evaluation of controls transactions.
2. Management of passwords, independent reconciliation, and audit trail.
3. Control self-assessment tools used by management.
4. Independent verification of data integrity and accuracy.
For a multinational organization, which of the following is a disadvantage of an ethnocentric staffing policy?
1. It significantly raises compensation and staffing costs.
2. It produces resentment among the organization's employees in host countries.
3. It limits career mobility for parent-country nationals.
4. It can lead to cultural myopia.
Which of the following is true regarding an organization's relationship with external stakeholders?
An organization with global headquarters in the United States has subsidiaries in eight other nations. If the organization operates with an ethnocentric attitude, which of the following statements is true?
Which of the following is a limiting factor for capacity expansion?
Providing knowledge, motivating organizational members, controlling and coordinating individual efforts, and expressing feelings and emotions are all functions of:
An internal auditor is investigating a potential fraudulent activity. What is the first test the auditor should perform on the transaction data under scrutiny?
Which of the following statements is false regarding the internal audit approach when a set of standards other than The IIA's Standards is applicable to a specific engagement?
How do data analysis technologies affect internal audit testing?
Organizations use matrix management to accomplish which of the following?



