IIA IIA-ACCA - ACCA CIA Challenge Exam
Which of the following is an element of effective negotiating?
Which of the following best demonstrates an organization's ability to recover from a disaster?
An organization is projecting sales of 100,000 units, at a unit price of $12. Unit variable costs are $7. If fixed costs are $350,000, what is the projected total contribution margin?
When developing an effective risk-based plan to determine audit priorities, an internal audit activity should start by:
Which of the following statements about matrix organizations is false?
The economic order quantity can be calculated using the following formula:
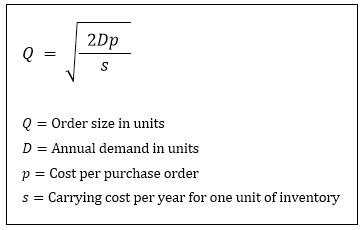
Which of the following describes how the optimal order size will change if the annual demand increases by 36 percent?
Which of the following should an organization consider when developing strategic objectives for its business processes?
1. Contribution to the success of the organization.
2. Reliability of operational information.
3. Behaviors and actions expected of employees.
4. How inputs combine with outputs to generate activities.
An employee frequently uses a personal smart device to send and receive work-related emails. Which of the following controls would be most effective to mitigate security risks related to these transmissions?
If legal or regulatory standards prohibit conformance with certain parts of The IIA's Standards, the auditor should do which of the following?
Which of the following statements accurately describes the responsibility of the internal audit activity (IAA) regarding IT governance?
1. The IAA does not have any responsibility because IT governance is the responsibility of the board and senior management of the organization.
2. The IAA must assess whether the IT governance of the organization supports the organization’s strategies and objectives.
3. The IAA may assess whether the IT governance of the organization supports the organization’s strategies and objectives.
4. The IAA may accept requests from management to perform advisory services regarding how the IT governance of the organization supports the organization’s strategies and objectives.
Which of the following application-based controls is an example of a programmed edit check?
Which of the following is not a method for implementing a new application system?
Which of the following costs would be incurred in an inventory stockout?
Which of the following is the most effective control to prevent unauthorized entrance of a former employee of the organization?
Which of the following characteristics is most important specifically for a global manager to possess in order to be successful?



