PECB ISO-IEC-27001-Lead-Auditor - PECB Certified ISO/IEC 27001 2022 Lead Auditor exam
Total 418 questions
As the Information Security Management System audit team leader, you are conducting a second-party audit of an international logistics company on behalf of an online retailer. During the audit, one of your team members reports a nonconformity relating to control 5.18 (Access rights) of Appendix A of ISO/IEC 27001:2022. She found evidence that removing the server access protocols of 20 people who left in the last 3 months took up to 1 week whereas the policy required removing access within 24 hours of their departure.
When the auditee was asked why there was a delay in removing access they replied, 'no one was available in the IT department during that period as a result of COVID-19. As soon as an IT officer became available the rights were removed.
You note that she intends to raise a minor non-conformity against Access rights control (5.18). How should you respond to this?
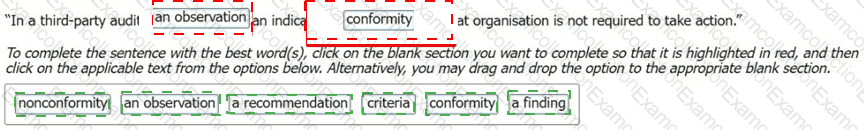
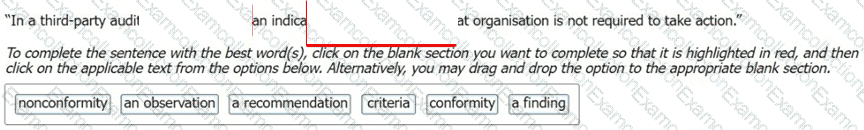
Select the words that best complete the sentence:
You are conducting an ISMS audit in the despatch department of an international logistics organisation that provides shipping services to large organisations including local hospitals and government offices. Parcels typically contain pharmaceutical products, biological samples, and documents such as passports and driving licences. You note that the company records show a very large number of returned items with causes including misaddressed labels and, in 15% of cases, two or more labels for different addresses for the one package. You are interviewing the Shipping Manager (SM).
You: Are items checked before being dispatched?
SM: Any obviously damaged items are removed by the duty staff before being dispatched, but the small profit margin makes it uneconomic to
implement a formal checking process.
You: What action is taken when items are returned?
SM: Most of these contracts are relatively low value, therefore it has been decided that it is easier and more convenient to simply reprint the label and re-send individual parcels than it is to implement an investigation.
You raise a nonconformity. Referencing the scenario, which three of the following Annex A controls would you expect the auditee to have implemented when you conduct the follow-up audit?
5.11 Return of assets
Which is the glue that ties the triad together
Scenario 9
CloudFort, a small networking company, provides network security, cloud computing, and virtualization solutions. The company has recently been certified in an information security management system (ISMS) based on the ISO/IEC 27001 standard, which has resulted in a spike in its recognition, confirming the maturity of CloudFort’s operation.
CloudFort continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. Due to its size and desire for greater objectivity, the top management decided to outsource the internal audit function to ensure the internal audit is independent of the audited activities and holds an advisory role in the continual improvement of the ISMS.
After the initial certification audit, the company created a new department specializing in data storage solutions. It offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. Because of the new department, CloudFort initiated a risk assessment process and an internal audit. Following the internal audit results, the company confirmed the effectiveness and efficiency of the new processes and controls.
After determining that the new department fully complies with ISO/IEC 27001 requirements, top management decided to include it in the certification scope. They submitted a request to the certification body for an extension of the certification scope to ensure that the department’s processes and security measures fully align with the overall ISMS.
One year after the initial certification audit, the certification body conducted another audit of CloudFort's ISMS. This audit aimed to determine CloudFort’s ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS fulfills the standard requirements. Nonetheless, the new department introduced changes that significantly affected how the overall management system was governed, requiring updates to existing processes and controls.
Moreover, although CloudFort requested an extension of the certification scope, they failed to provide timely updates on the impact of the new department on the ISMS to the certification body. Thus, CloudFort’s certification was suspended.
Question
CloudFort requested an extension of the certification scope to include the new department. How would you classify this situation? Refer to Scenario 9.
Scenario 1
Fintive is a distinguished security provider specializing in online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive offers services to companies operating online that seek to improve their information security, prevent fraud, and protect user information such as personally identifiable information (PII).
Fintive bases its decision-making and operational processes on previous cases, gathering customer data, classifying them according to the case, and analyzing them.
Initially, Fintive required a large number of employees to be able to conduct such complex analyses. However, as technology advanced, the company recognized an opportunity to implement a modern tool — a chatbot — to achieve pattern analyses aimed at preventing fraud in real time. This tool would also assist in improving customer service.
The initial idea was communicated to the software development team, who supported the initiative and were assigned to work on the project. They began integrating the chatbot into the existing system and set an objective regarding the chatbot, which was to answer 85% of all chat queries.
After successfully integrating the chatbot, the company released it for customer use. However, the chatbot exhibited several issues. Due to insufficient testing and a lack of sample data provided during the training phase — when it was supposed to learn the query patterns — the chatbot failed to effectively address user queries. Additionally, it sent random files to users when it encountered invalid inputs, such as unusual patterns of dots and special characters.
Consequently, the chatbot could not effectively answer customer queries, overwhelming traditional customer support and preventing them from assisting customers with their requests.
Recognizing the potential risks, Fintive decided to implement a set of new controls. The measures included enabling comprehensive audit logging, configuring automated alert systems to flag unusual activities, performing periodic access reviews, and monitoring system behavior for anomalies. The objective was to identify unauthorized access, errors, or suspicious activities in a timely manner, ensuring that any potential issues could be quickly recognized and investigated before causing significant harm.
Question
Based on the scenario above, to ensure the protection of information privacy, Fintive decided to implement security controls. Is this acceptable?
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
Is the internal auditor responsible for following up on action plans resulting from external audits?
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
According to Scenario 9, the auditor decided to conduct the extension audit during the surveillance audit. How do you define this situation?
You are an ISMS audit team leader preparing to chair a closing meeting following a third-party surveillance audit. You are drafting a closing meeting agenda setting out the topics you wish to discuss with your auditee.
Which one of the following would be appropriate for inclusion?
Question
During a certification audit at Company X, the audit team leader noticed that some HR processes are excluded from the audit scope. However, these processes are included in the company's ISMS scope.
Is this acceptable?