Microsoft MS-203 - Microsoft 365 Messaging
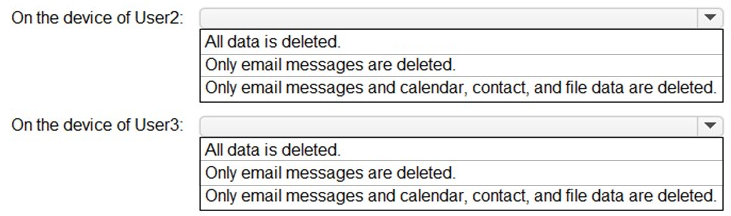
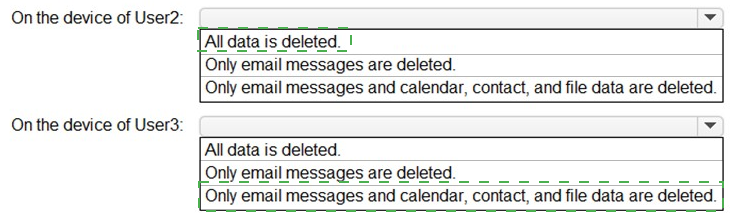
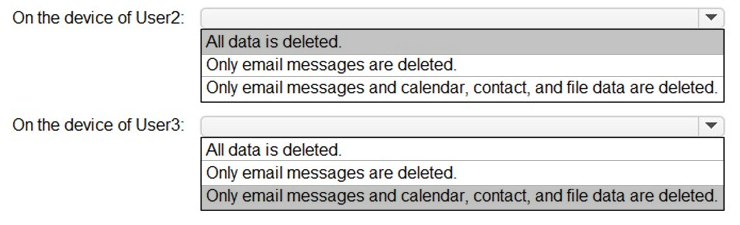
You need to perform a remote wipe of the devices of User2 and User3.
You run the following commands.
Clear-MobileDevice -id User2-Device
-NotificationEmailAddress "admin@Fabrikam.com"
Clear-MobileDevice -id User3-Device
-NotificationEmailAddress "admin@Fabrikam.com"
What occurs on each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to identify which users clicked the links in the phishing emails.
What should you do?
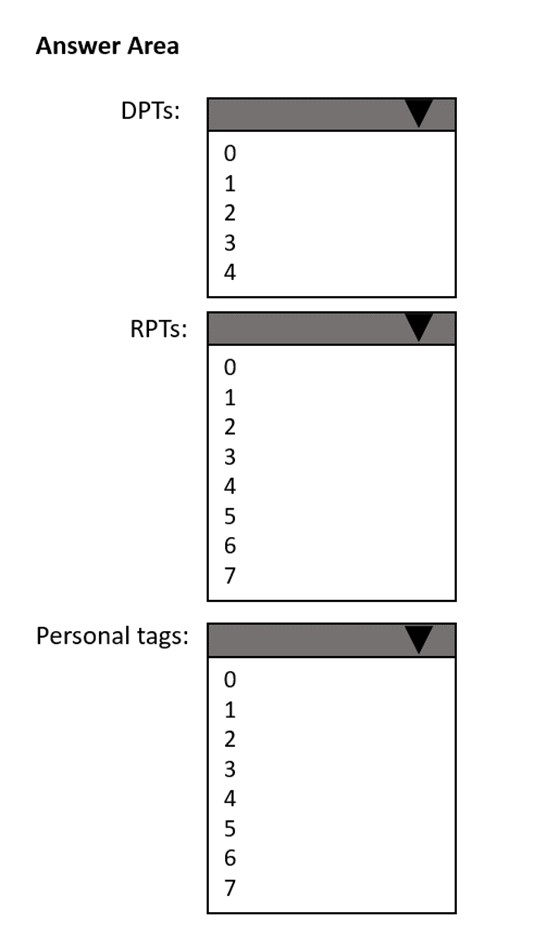
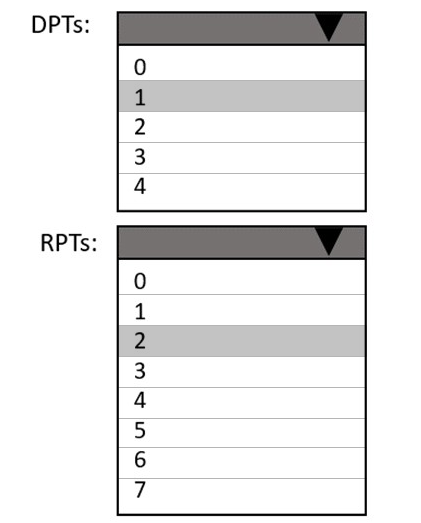
How many default policy tags (DPTs), retention policy tags (RPTs), and personal tags should you create to meet the retention requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
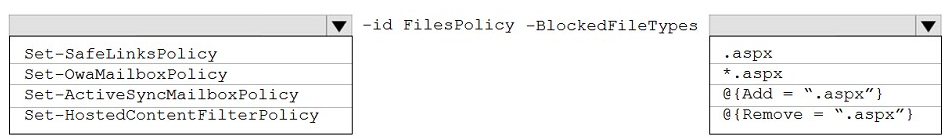
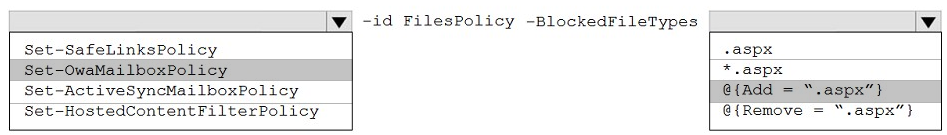
You need to modify FilesPolicy to prevent users from downloading ASPX files. The solution must meet the technical requirements.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which contacts can sign in to and access resources in the adatum.com tenant?
You discover that email messages sent to contoso.com are NOT delivered through Contoso Connector.
You need to ensure that all email sent to contoso.com is delivered through Contoso Connector.
Which connector setting should you modify?
You need to email a list of configuration changes to the Exchange Online environment that were recently performed by Allan Deyoung.
What should you do?
Lynne Robbins and the users in the sales department plan to collaborate on a project with a partner company named Contoso, Ltd. that has an email domain named contoso.com.
You need to ensure that only the sales department users can share all their calendar free/busy
information with the users in contoso.com.
How should you configure the organization relationship?
You need to ensure that Allan Deyoung can create a new public folder for the sales department.
Which two actions should you perform first? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.



 Text
Description automatically generated
Text
Description automatically generated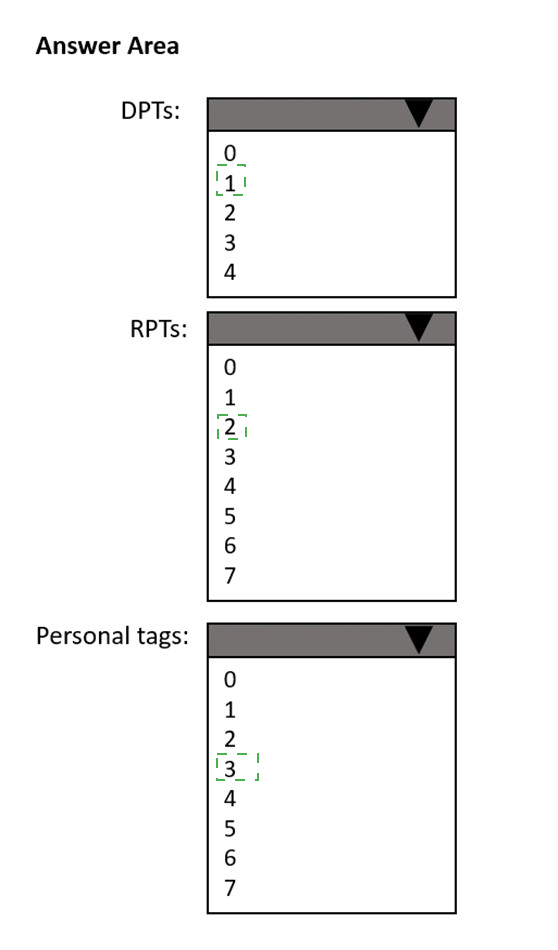
 Table
Description automatically generated
Table
Description automatically generated Table
Description automatically generated
Table
Description automatically generated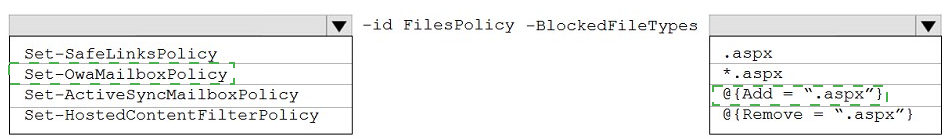
 Text
Description automatically generated
Text
Description automatically generated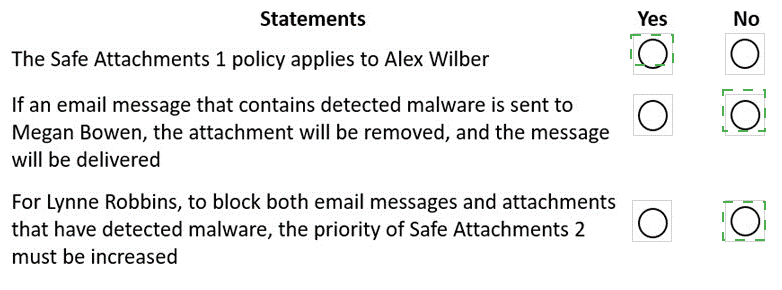
 Graphical user interface, text, application, letter, email
Description automatically generated
Graphical user interface, text, application, letter, email
Description automatically generated