CompTIA N10-009 - CompTIA Network+ Certification Exam
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following connector types is most likely in use?
An attacker gained access to the hosts file on an endpoint and modified it. Now, a user is redirected from the company’s home page to a fraudulent website. Which of the following most likely happened?
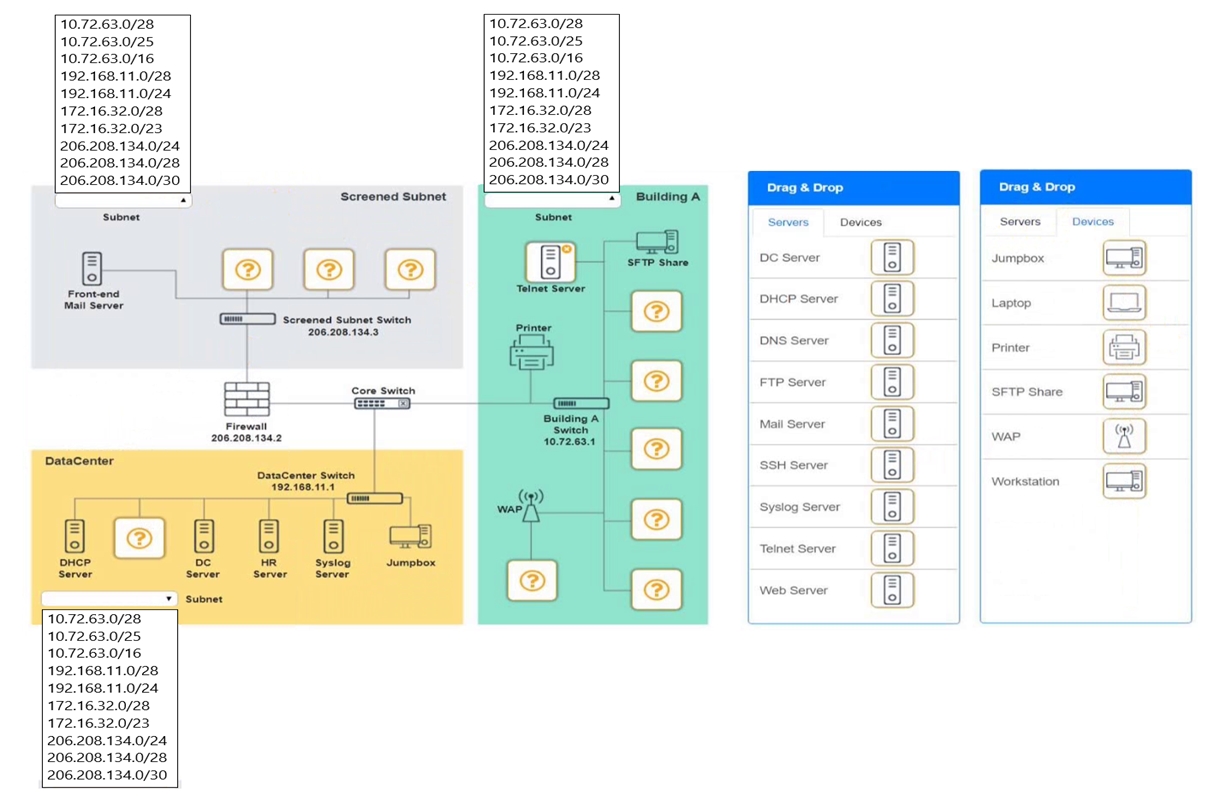
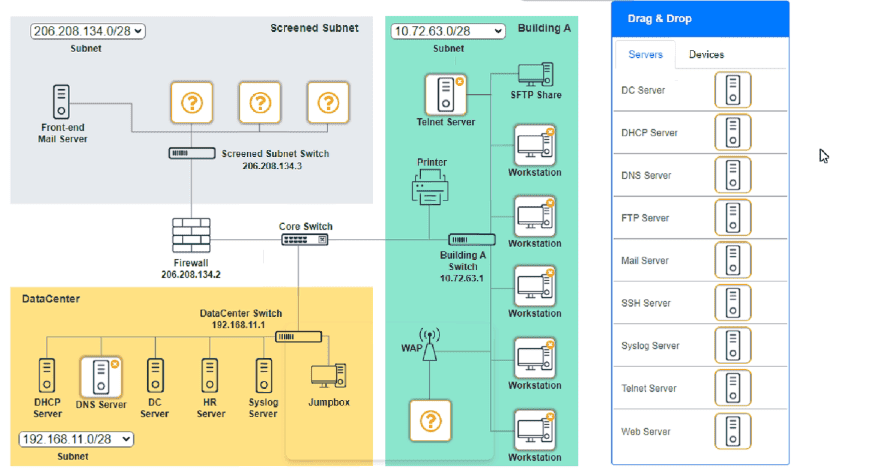
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Before using a guest network, an administrator requires users to accept the terms of use Which of the following is the best way to accomplish this goal?
Which of the following protocols provides remote access utilizing port 22?
Which of the following connection methods allows a network engineer to automate configuration deployment for network devices across the environment?
A secure communication link needs to be configured between data centers via the internet. The data centers are located in different regions. Which of the following is the best protocol for the network administrator to use?
Which of the following steps in the troubleshooting methodology comes after using a top-to-top buttom examination of the OSI model to determine cause?
A network technician is designing a LAN for a new facility. The company is expecting more than 300 devices to connect to the network. Which of the following masks will provide the most efficient subnet?



 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.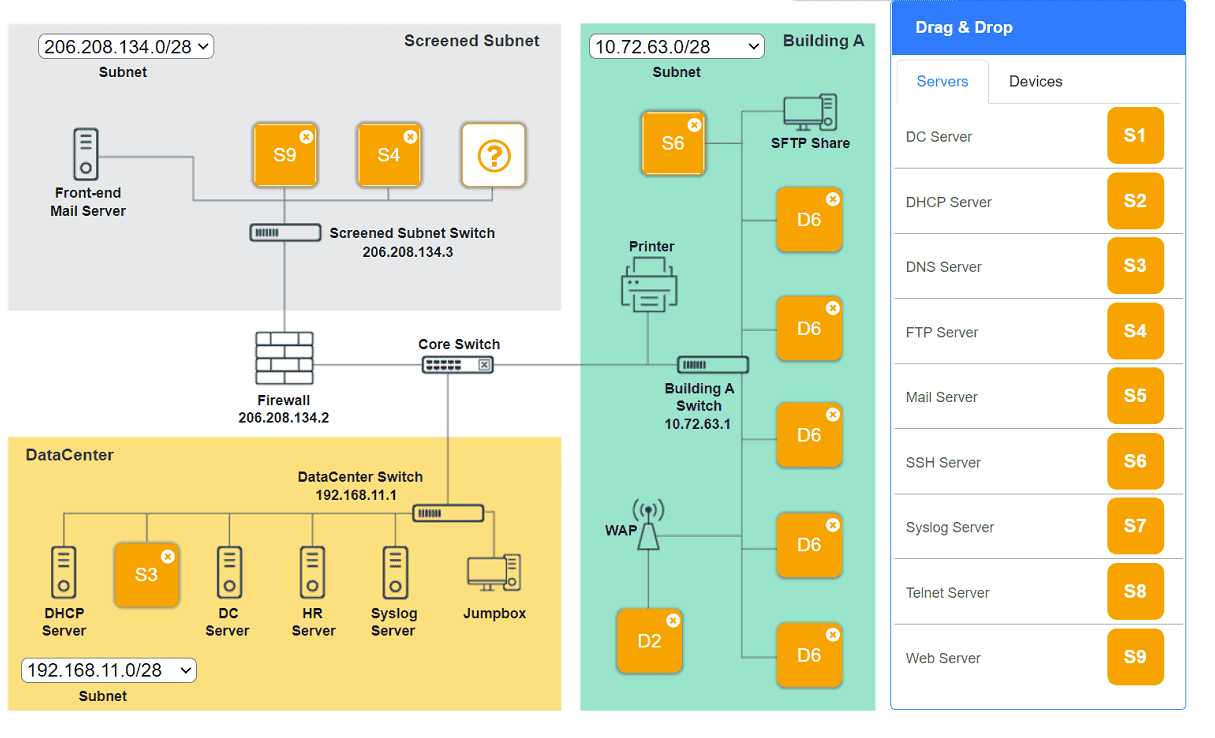 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.