Nutanix NCP-5.15 - Nutanix Certified Professional - Multi cloud Infrastructure (NCP-MCI 5.15)
An administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors. What is the effect on live migration?
A Nutanix cluster is equipped with four nodes. Four VMs on this cluster have been configured with a VM-VM anti-affinity policy and are each being hosted by a different node.
What occurs to the cluster and these VMs during an AHV upgrade?
Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)
A customer has a 24-node cluster with all containers configured with RF3. Two different nodes have incurred a simultaneous HDD failure.
What is the result?
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
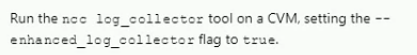
C)
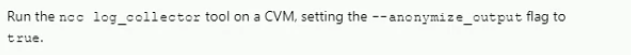
D)

CPU utilization climbs above 90% on several VMs. This causes performance degradation for a business-critical application.
How can alerts be configured to notify the administrator before VM CPU utilization hits 90%?
An administrator is implementing a VDI solution. The workload will be a series of persistent desktops in a dedicated storage container within a four-node cluster Storage optimizations should be set on the dedicated storage container to give optimal performance including during a node failure event
Which storage optimizations should the administrator set to meet the requirements?
Which data savings technique utilizes stripes and parity calculation in a Nutanix cluster?
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
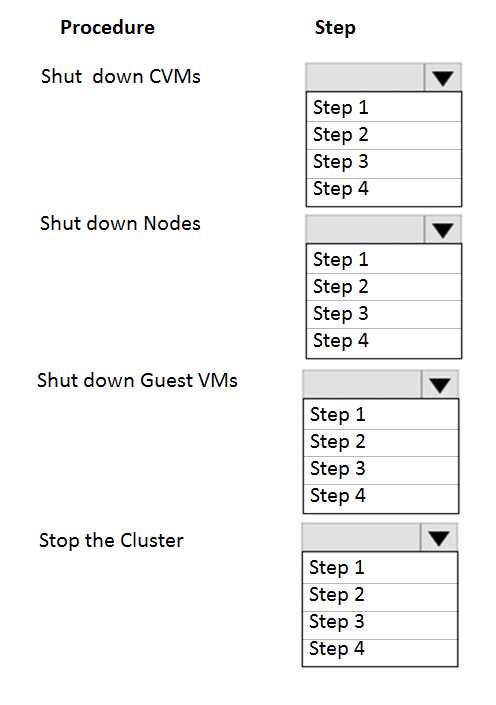
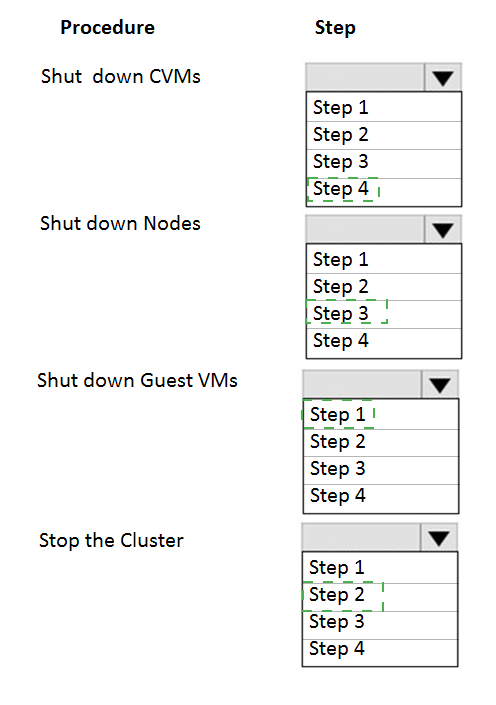
An administrator needs to shut down an AHV cluster to relocate hardware. The administrator upgrades NCC and runs health checks.
Which steps should the administrator perform next?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements.