Fortinet NSE5_SSE_AD-7.6 - Fortinet NSE 5 - FortiSASE and SD-WAN 7.6 Core Administrator
Which three factors about SLA targets and SD-WAN rules should you consider when configuring SD-WAN rules? (Choose three answers)
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
An existing Fortinet SD-WAN customer who has recently deployed FortiSASE wants to have a comprehensive view of, and combined reports for, both SD-WAN branches and remote users. How can the customer achieve this?
An SD-WAN member is no longer used to steer SD-WAN traffic. You want to update the SD-WAN configuration and delete the unused member.
Which action should you take first? (Choose one answer)
You have a FortiGate configuration with three user-defined SD-WAN zones and one or two members in each of these zones. One SD-WAN member is no longer used in health-check and SD-WAN rules. This member is the only member of its zone. You want to delete it.
What happens if you delete the SD-WAN member from the FortiGate GUI?
Which secure internet access (SIA) use case minimizes individual endpoint configuration? (Choose one answer)
How does the FortiSASE security dashboard facilitate vulnerability management for FortiClient endpoints? (Choose one answer)
Refer to the exhibits.
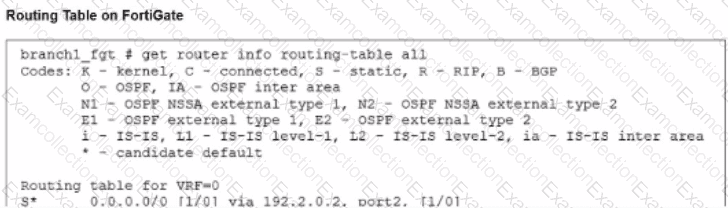
The administrator increases the member priority on port2 to 20. Upon configuration changes and the receipt of new packets, which two actions does FortiGate perform on existing sessions established over port2? (Choose two.)
A FortiGate device is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process? (Choose one answer)
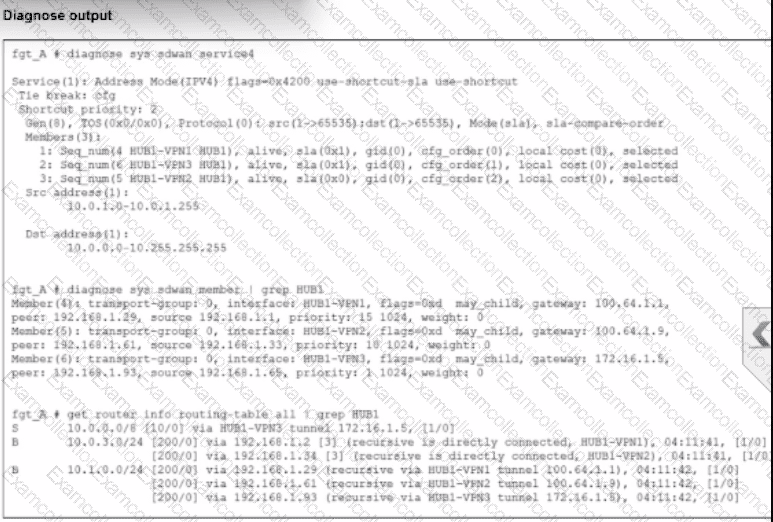
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)



