Fortinet NSE6_FML-7.2 - Fortinet NSE 6 - FortiMail 7.2
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
Refer to the exhibits, which display a topology diagram (Topology) and two FortiMail device configurations (FML1 Configuration and FML2 Configuration).
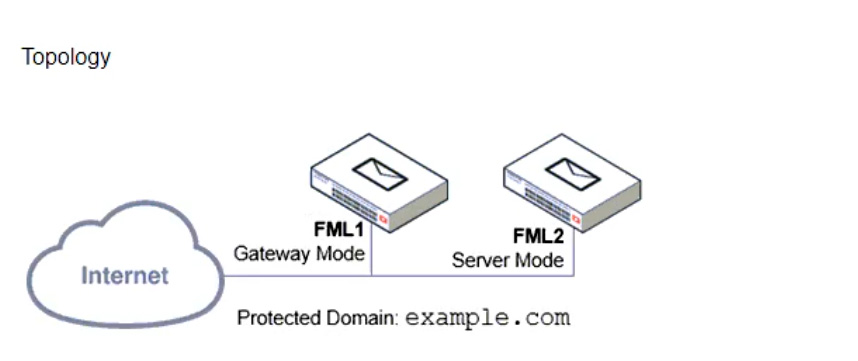
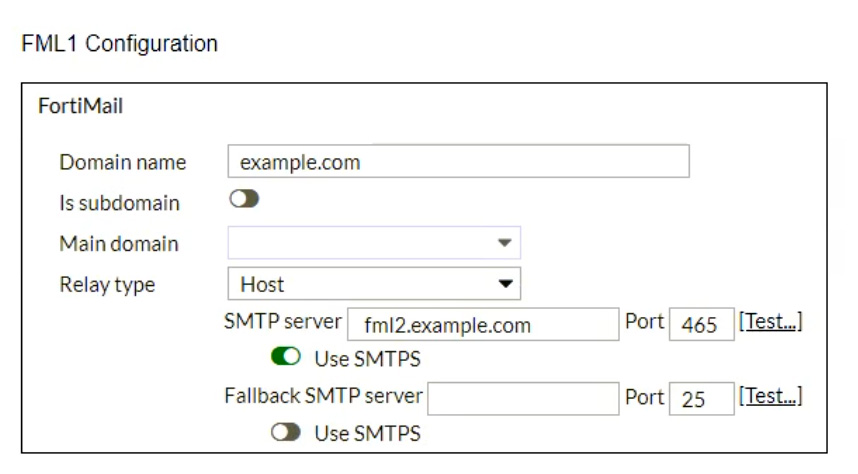
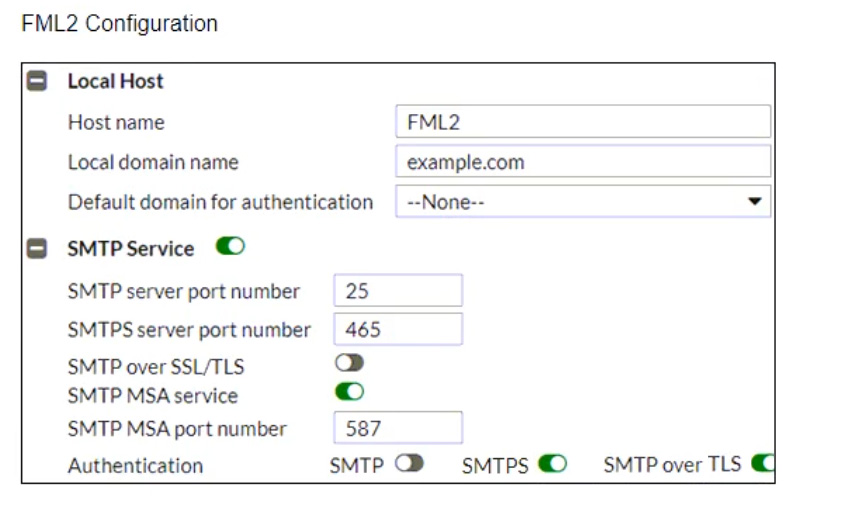
What is the expected outcome of SMTP sessions sourced from FML1 and destined for FML2?
Refer to the exhibits which show a topology diagram (Topology) and a configuration element (Access Control Rule).
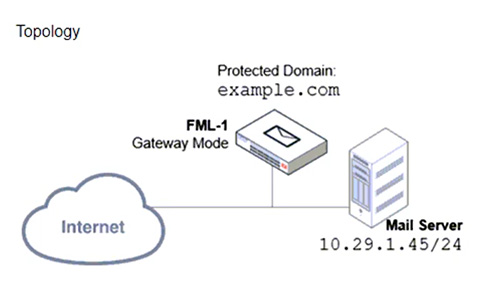
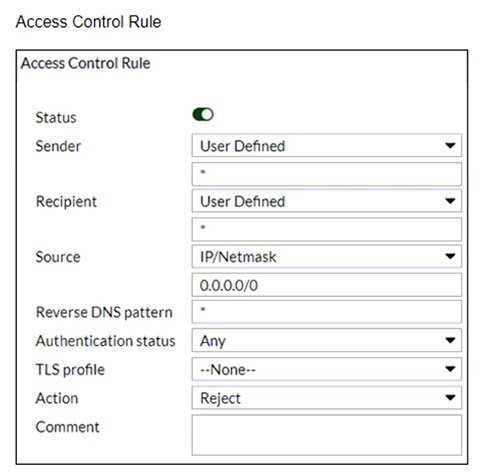
Which three access control settings are recommended to allow outbound email from the example.com domain on FML-1? (Choose three.)
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
Which two FortiMail antispam techniques can you use to combat zero-day spam? (Choose two.)
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Refer to the exhibit which shows an nslookup output of MX records of the example.com domain.
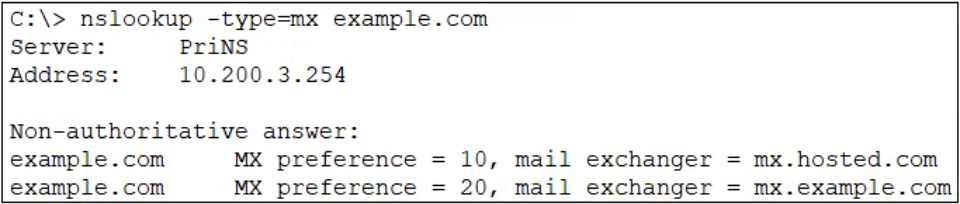
Which two MTA selection behaviors for the example.com domain are correct? (Choose two.)
Refer to the exhibits which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
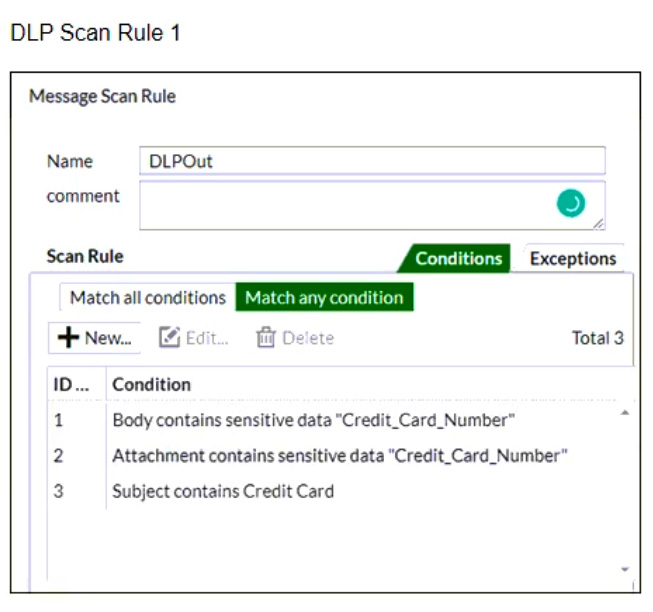
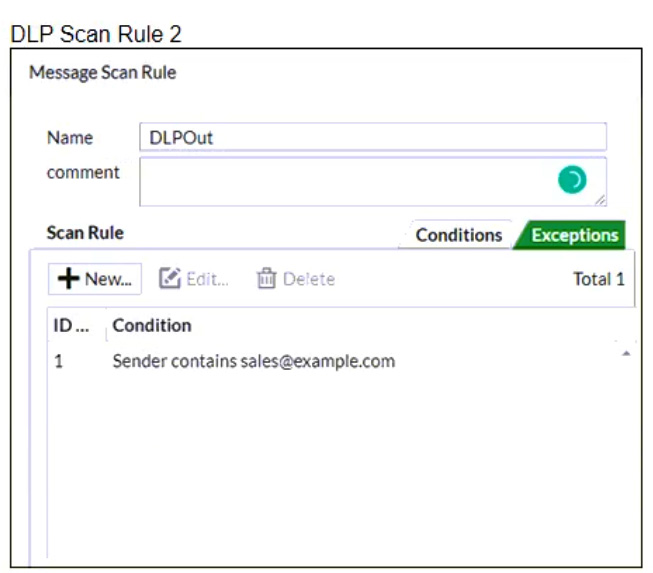
Which two message types will trigger this DLP scan rule? (Choose two.)



