Fortinet NSE6_FWF-6.4 - Fortinet NSE 6 - Secure Wireless LAN 6.4
Six APs are located in a remotely based branch office and are managed by a centrally hosted FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
When deploying a wireless network that is authenticated using EAP PEAP, which two configurations are required? (Choose two.)
A tunnel mode SSID is configured on a FortiGate wireless controller.
Which task must be completed before the SSID can be used?
Which statement is correct about security profiles on FortiAP devices?
Which two statements about background rogue scanning are correct? (Choose two.)
What is the first discovery method used by FortiAP to locate the FortiGate wireless controller in the default configuration?
As standard best practice, which configuration should be performed before configuring FortiAPs using a FortiGate wireless controller?
Refer to the exhibit.
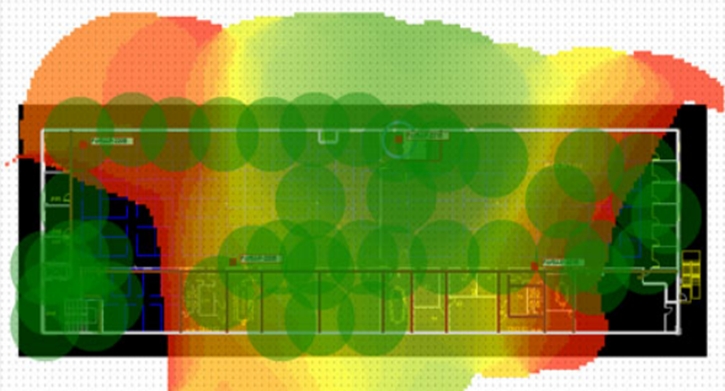
If the signal is set to -68 dB on the FortiPlanner site survey reading, which statement is correct regarding the coverage area?
Which of the following is a requirement to generate analytic reports using on-site FortiPresence deployment?
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)



