Fortinet NSE8_812 - Network Security Expert 8 Written Exam
A FortiGate deployment contains the following configuration:
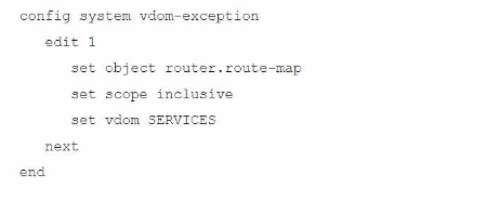
What is the result of this configuration?
Refer to the exhibit.
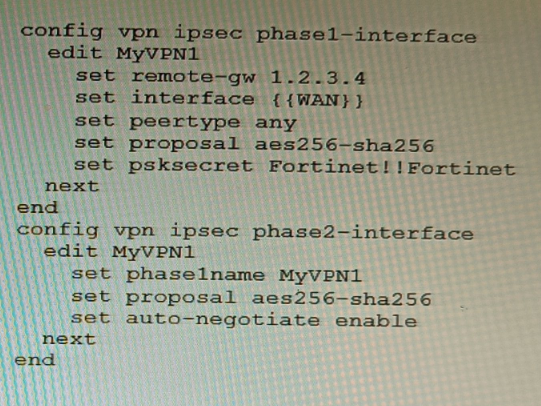
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
Refer to the exhibit.
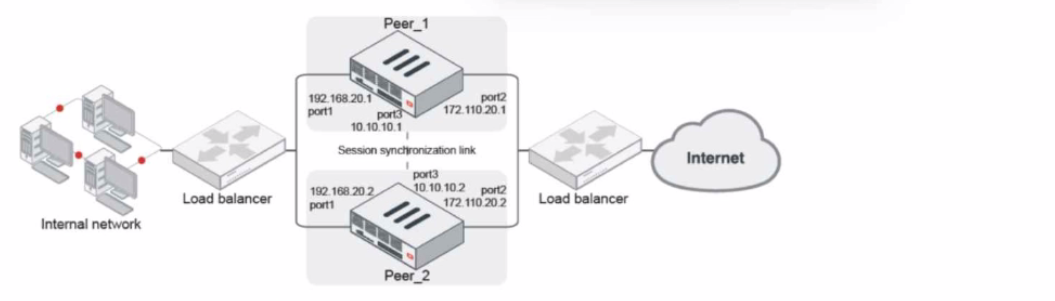
Given the exhibit, which two statements about FortiGate FGSP HA cluster behavior are correct? (Choose two.)
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
Refer to the exhibit showing a FortiSOAR playbook.
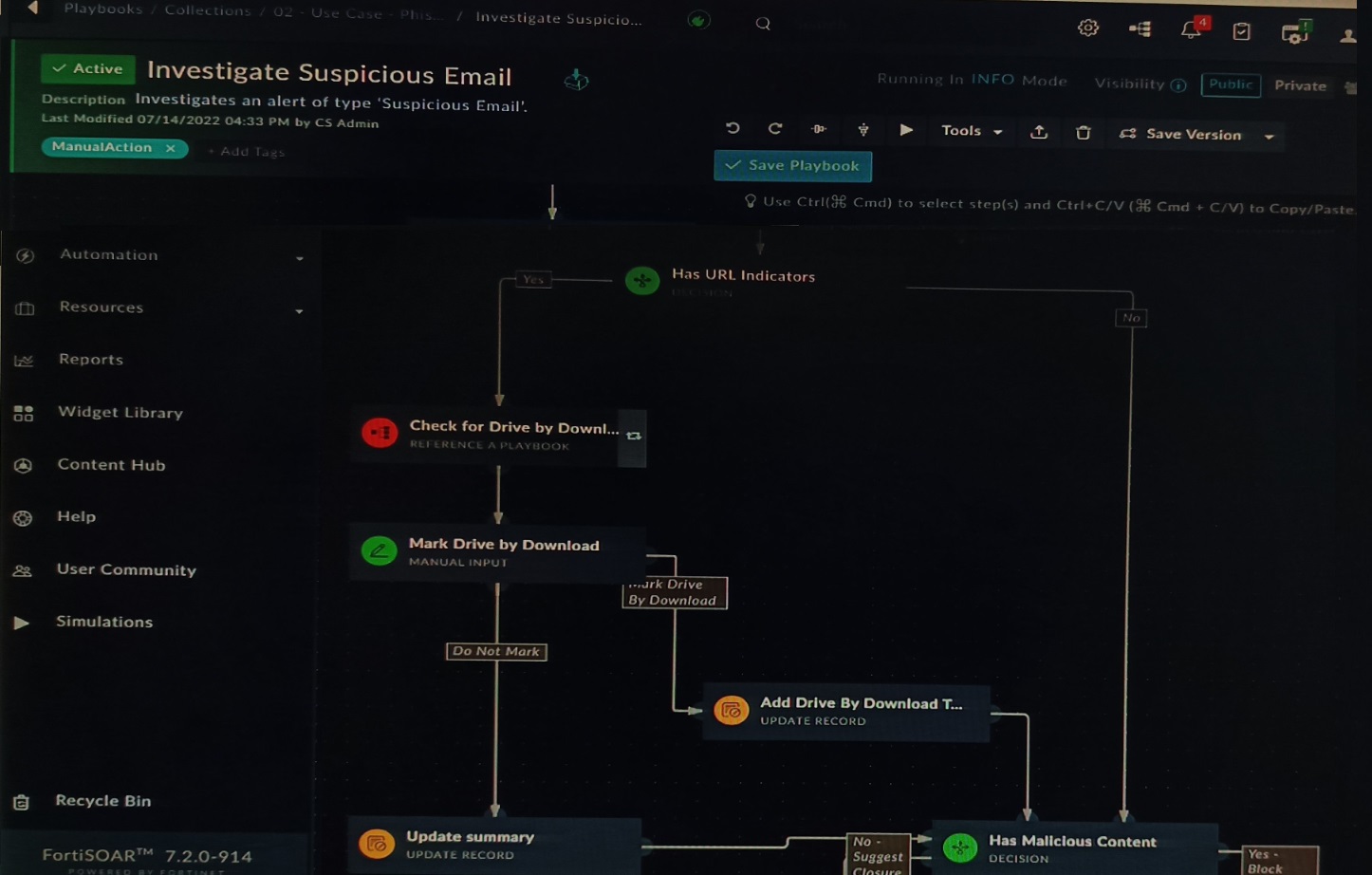
You are investigating a suspicious e-mail alert on FortiSOAR, and after reviewing the executed playbook, you can see that it requires intervention.
What should be your next step?
Refer to the exhibits.
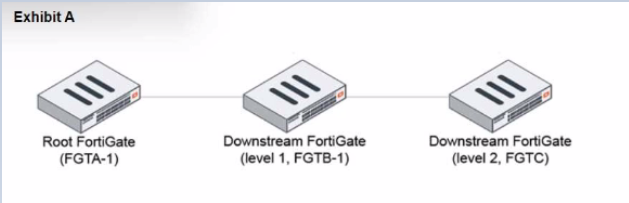
During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
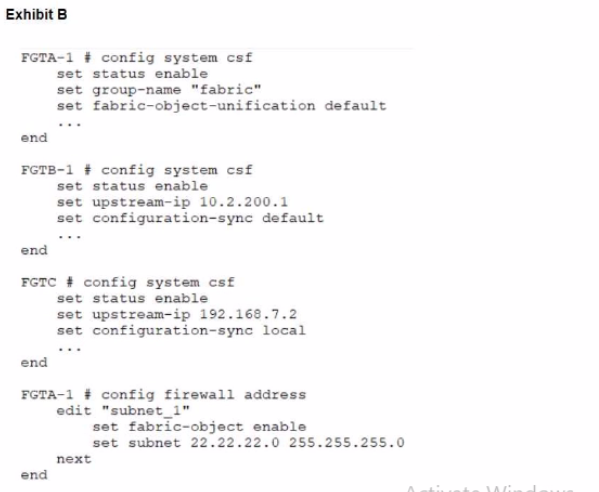
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
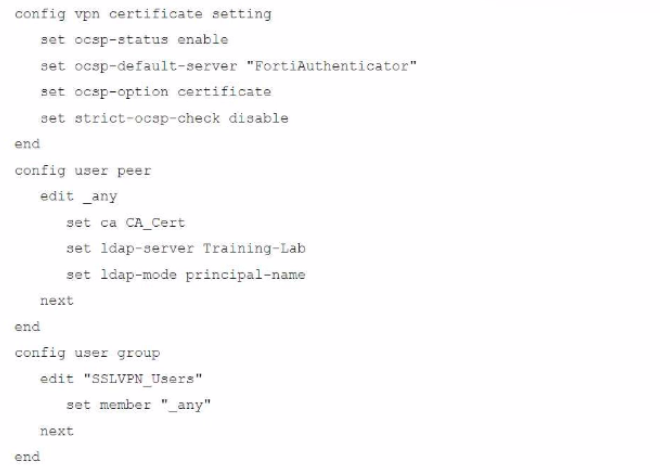
Based on this configuration, which authentication scenario will FortiGate deny?
Refer to the exhibit.
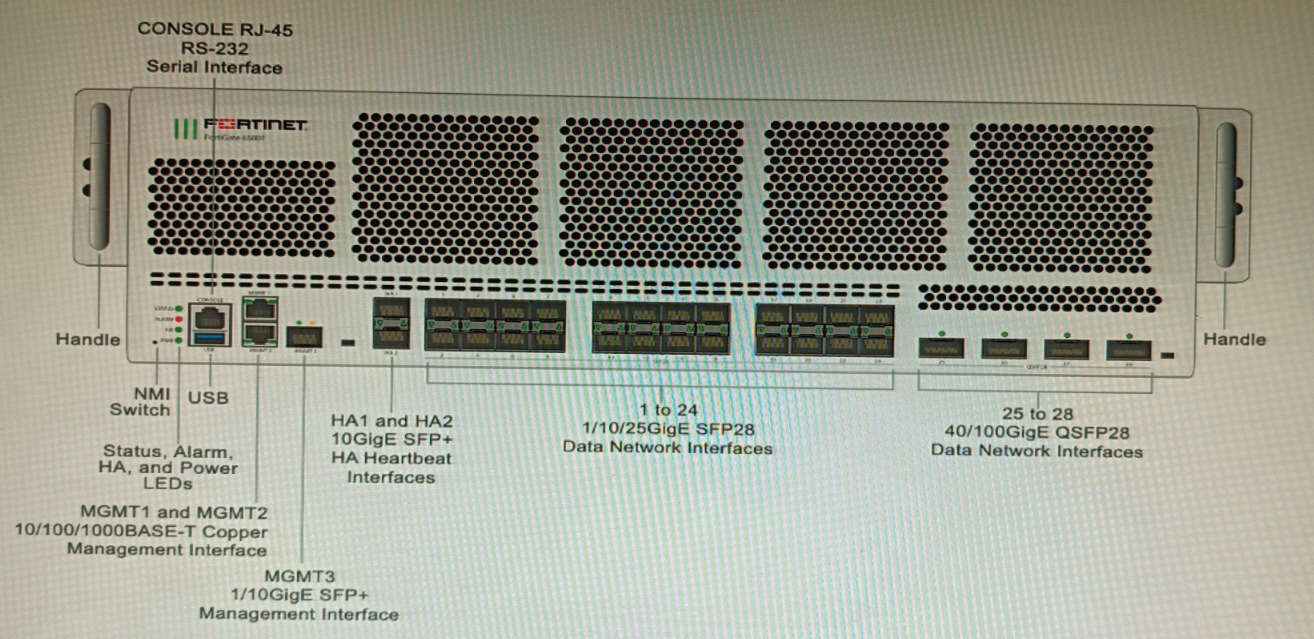
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?
You are designing a setup where the FortiGate device is connected to two upstream ISPs using BGP. Part of the requirement is that you must be able to refresh the route advertisements manually without disconnecting the BGP neighborships.
Which feature must you enable on the BGP neighbors to accomplish this goal?



