Netskope NSK101 - Netskope Certified Cloud Security Administrator (NCCSA)
An administrator wants to determine to which data plane a user is traversing. In this scenario, what are two ways to accomplish this task? (Choose two.)
Click the Exhibit button.
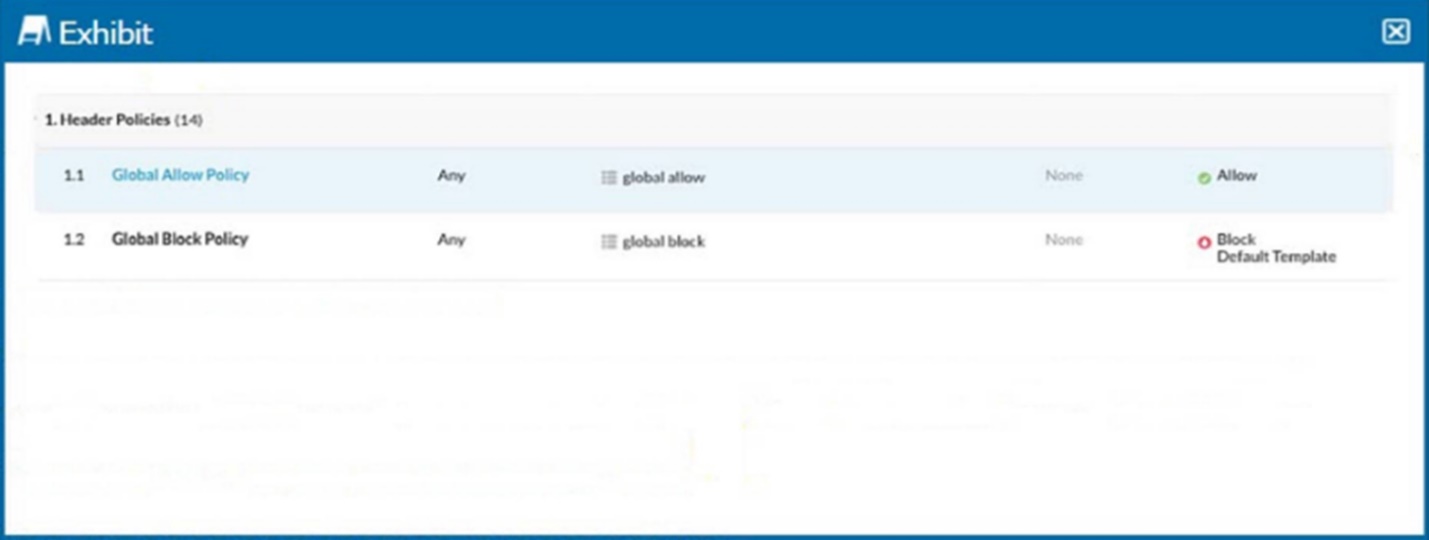
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
Which networking function does a SASE solution provide above and beyond an SSE solution?
Your organization has implemented Netskope Private Access (NPA) for all users. Users from the European region are reporting that they are unable to access many of their applications. You suspect that the publishers for the European data center may be disconnected and you want to verify the Publishers' status.
Which two methods describe how you would accomplish this task? (Choose two.)
You are adding a new tenant administrator in the Admins page. Which additional security measure would you be able to enable for only this new account?
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors potential risky users for a malicious activity that would cause data loss?
You are required to provide an additional pop-up warning to users before allowing them to proceed to Web applications categorized as "low" or "poor" by Netskope's Cloud Confidence Index. Which action would allow you to accomplish this task?
Your customer asks you to secure all Web traffic as part of the initial configuration. In the Netskope platform, which statement is correct in this scenario?
Which two statements are correct about Netskope’s NewEdge Security Cloud Network Infrastructure? (Choose two.)



