CyberArk PAM-CDE-RECERT - CyberArk CDE Recertification
What is the purpose of the Interval setting in a CPM policy?
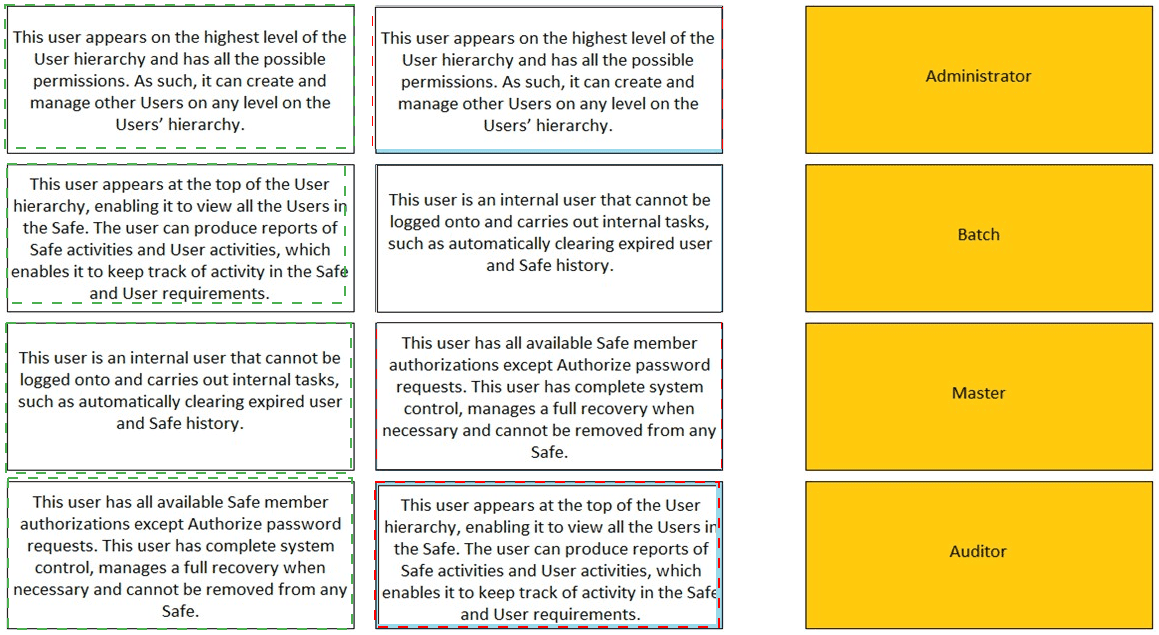
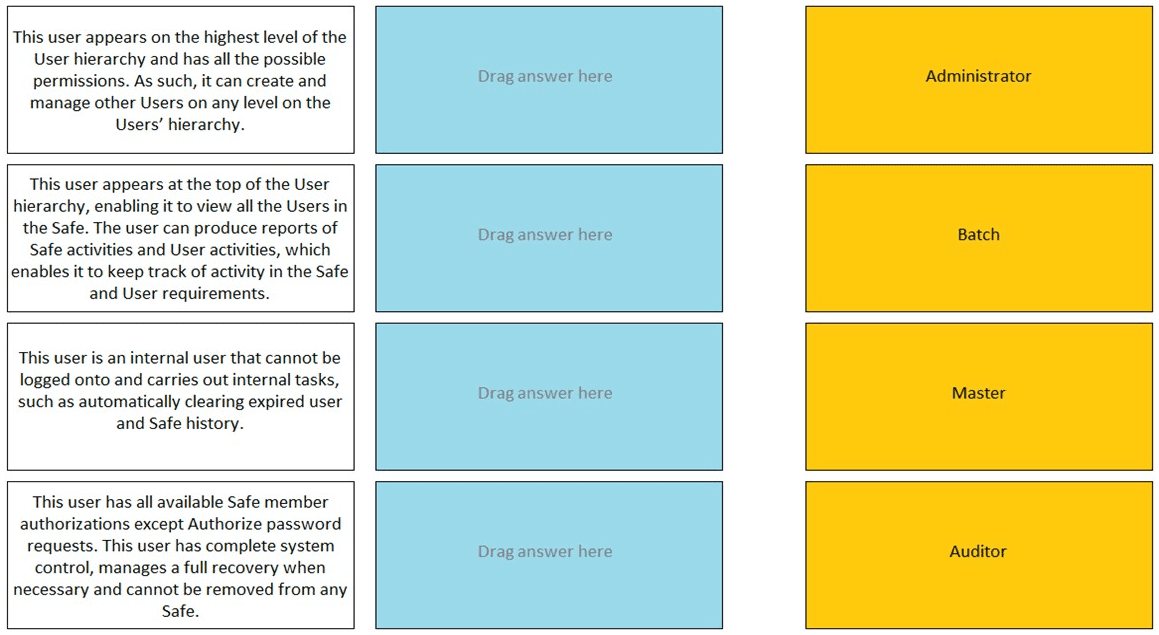
Match the built-in Vault User with the correct definition.
To enable the Automatic response “Add to Pending†within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
What is the easiest way to duplicate an existing platform?
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
You are responsible for installing a CPM.
Which Vault authorizations will your CyberArk user need to install the CPM?
You receive this error:
“Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.â€
Which root cause should you investigate?
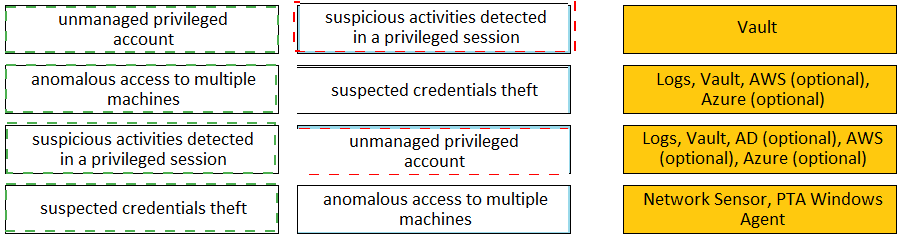
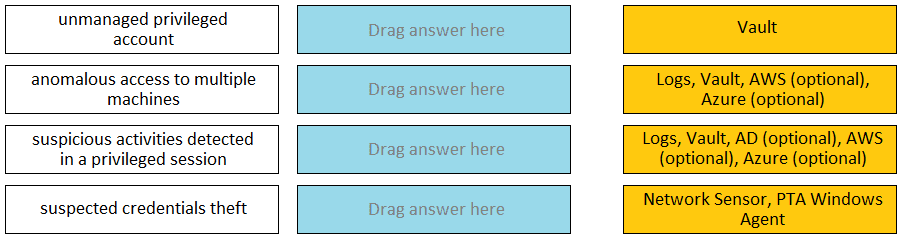
Match each PTA alert category with the PTA sensors that collect the data for it.
What is a requirement for setting fault tolerance for PSMs?
A customer is moving from an on-premises to a public cloud deployment. What is the best and most cost-effective option to secure the server key?