CyberArk PAM-DEF - CyberArk Defender - PAM
A Simple Mail Transfer Protocol (SMTP) integration is critical for monitoring Vault activity and facilitating workflow processes, such as Dual Control.
What does the minvalidity parameter on a platform policy determine?
What are the minimum permissions to add multiple accounts from a file when using PVWA bulk-upload? (Choose three.)
What can you do to ensure each component server is operational?
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
Which service should NOT be running on the DR Vault when the primary Production Vault is up?
Your organization requires all passwords be rotated every 90Â days.
Where can you set this regulatory requirement?
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
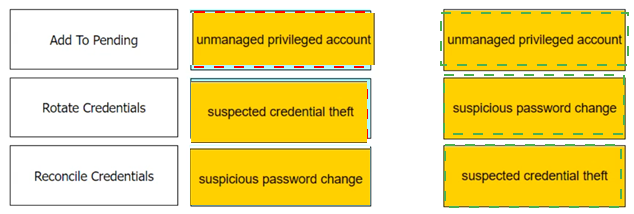
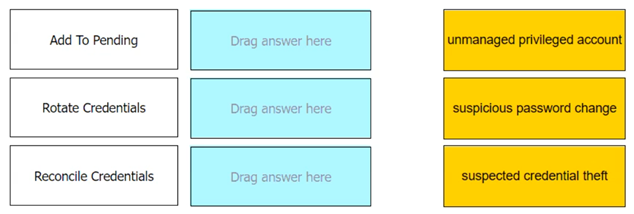
Match each automatic remediation to the correct PTA security event.
How does the Vault administrator apply a new license file?