Paloalto Networks PCCSE - Prisma Certified Cloud Security Engineer
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
The security team wants to enable the “block†option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
Which three actions are required in order to use the automated method within Azure Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose three.)
Which two statements apply to the Defender type Container Defender - Linux?
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
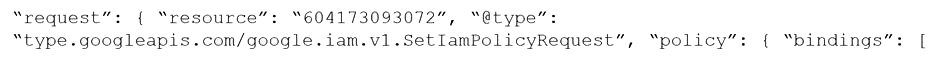
B)
C)
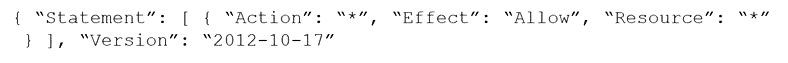
D)

Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
A customer wants to monitor its Amazon Web Services (AWS) accounts via Prisma Cloud, but only needs the resource configuration to be monitored at present.
Which two pieces of information are needed to onboard this account? (Choose two.)
What are the subtypes of configuration policies in Prisma Cloud?
The exclamation mark on the resource explorer page would represent?



