Paloalto Networks PCNSA - Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)
An address object of type IP Wildcard Mask can be referenced in which part of the configuration?
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
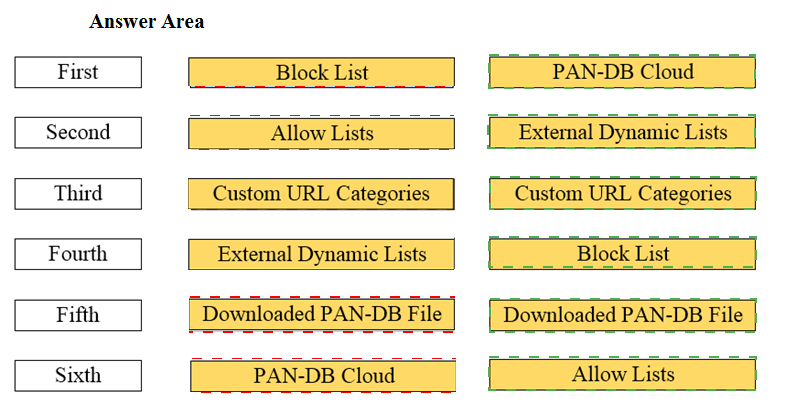
Arrange the correct order that the URL classifications are processed within the system.
The CFO found a malware infected USB drive in the parking lot, which when inserted infected their corporate laptop the malware contacted a known command-and-control server which exfiltrating corporate data.
Which Security profile feature could have been used to prevent the communications with the command-and-control server?
In a File Blocking profile, which two actions should be taken to allow file types that support critical apps? (Choose two.)
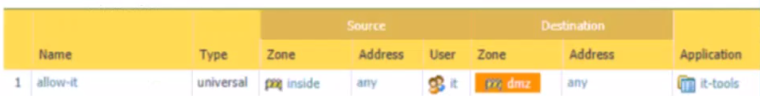
Based on the screenshot what is the purpose of the group in User labelled ''it"?
In order to attach an Antivirus, Anti-Spyware and Vulnerability Protection security profile to your Security Policy rules, which setting must be selected?
Which statement is true regarding a Prevention Posture Assessment?
What are three configurable interface types for a data-plane ethernet interface? (Choose three.)
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?