Paloalto Networks PCNSA - Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)
Which path in PAN-OS 10.2 is used to schedule a content update to managed devices using Panorama?
What are the two main reasons a custom application is created? (Choose two.)
Which User Credential Detection method should be applied within a URL Filtering Security profile to check for the submission of a valid corporate username and the associated password?
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
An administrator would like to protect against inbound threats such as buffer overflows and illegal code execution.
Which Security profile should be used?
An administrator creates a new Security policy rule to allow DNS traffic from the LAN to the DMZ zones. The administrator does not change the rule type from its default value.
What type of Security policy rule is created?
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
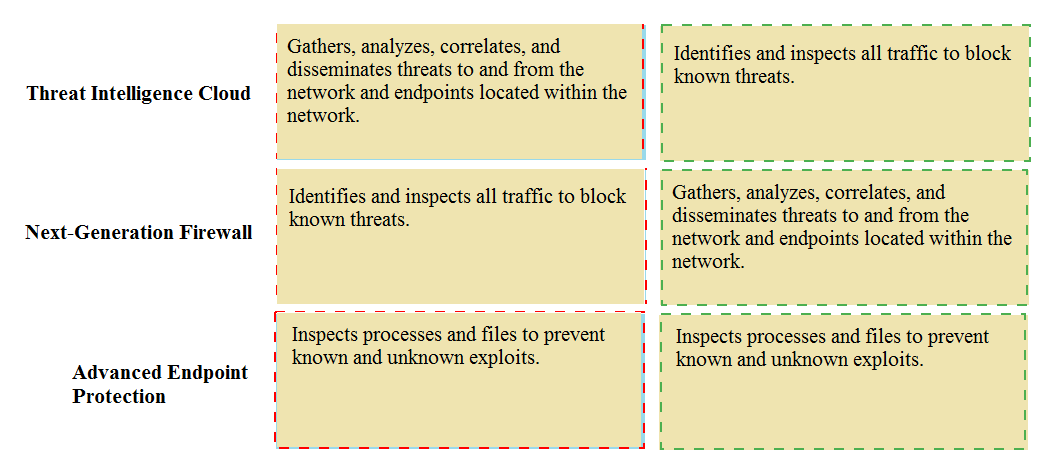
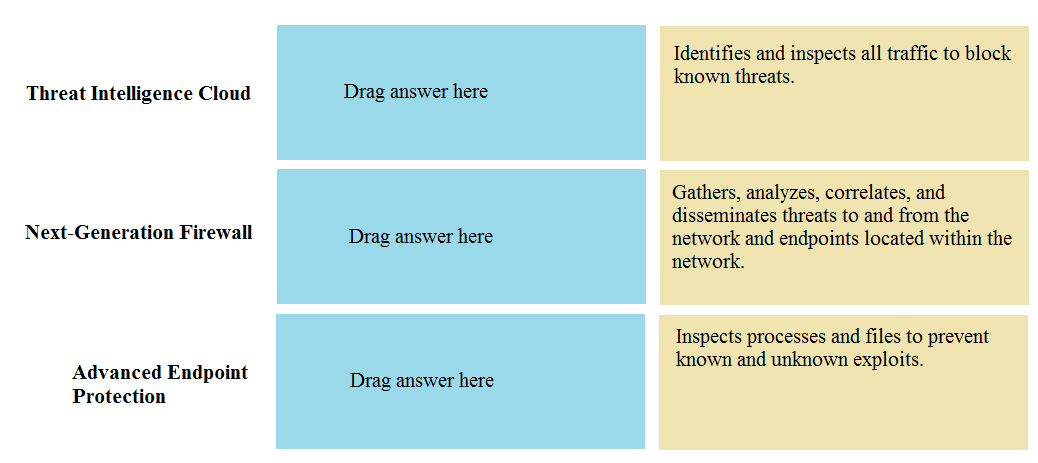
Match the Palo Alto Networks Security Operating Platform architecture to its description.
What are three factors that can be used in domain generation algorithms? (Choose three.)
Which prevention technique will prevent attacks based on packet count?