Pegasystems PEGAPCLSA86V2 - Lead System Architect (LSA) Pega Architecture Exam 86V2
What two recommendations do you provide to the development team to ensure the performance of the Pega application does not degrade over time? (Choose Two)
BigCo receives complaints from existing customers and new prospects that BigCo representatives contact them with irrelevant offers and products.
Which two Pega solutions do you suggest to help solve this problem? (Choose Two)
An application consisting of a single case requires sending correspondence at a designated time with minimal delay. The existing solution uses an assignment to pause the case until an SLA invokes the escalation activity that sends the correspondence. Occasionally there is a delay in sending the correspondence.
Which two factors contribute to the delay? (Choose Two)
While configuring GetNextWork, overriding the System Settings rule
GetNextWork__WorkBasketUrgencyThreshold imposes a minimum cutoff value for assignment urgency.
Which statement accurately depicts the system behavior when the GetNextWork_WorkBaseketUrgencyThreshold setting is overridden?
your application connects to two REST services that list details about bank offices.
One REST service uses a postal code as a GET parameter and returns a detailed list of bank officers in that postal code.
the other REST service uses a city name as a GET parameter and returns a datailed list of back offices in cities with that name. The application uses data pages to cache details about bank offices.
select two options to configure a data page to accept either a postal code or a city name as a parameter and call the appropriate REST connector.(choose TWO)
set the three security tasks you perform when deploying an application to a production environment. (Choose Three)
What two features do activities and functions share? (Choose Two)
You add database connection information to prconfig.xml and want to encrypt the password in the connection information how do you encrypt the password?
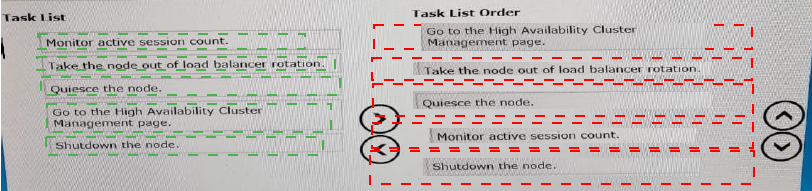
BigCo is planning an update to JVM settings on all production nodes at the of the month. The production application supports high availability.
To ensure that users can continue working without distribution while the JVM changes are in process, select and move all of the following tasks to the Task List Order column arrange then correct order.
A case can be withdrawn using a local action. You want to restrict the ability to withdraw a
case to the user who created the case or any work group manager of the user. Select three
rule types used in combination to achieve this functionality. (choose three)