Paloalto Networks PSE-Strata - Palo Alto Networks System Engineer Professional - Strata
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
What are three key benefits of the Palo Alto Networks platform approach to security? (Choose three)
Access to a business site is blocked by URL Filtering inline machine learning (ML) and
considered as a false-positive.
How should the site be made available?
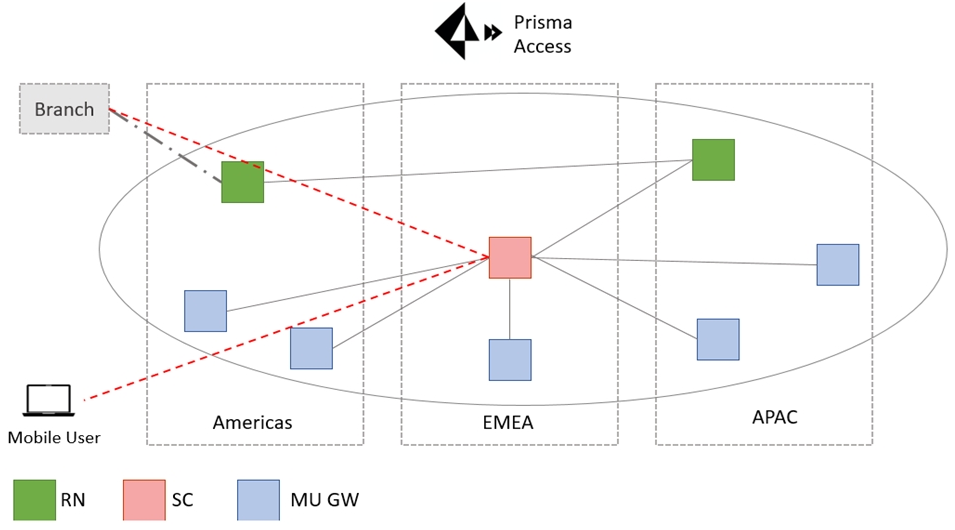
What action would address the sub-optimal traffic path shown in the figure?
Key:
RN - Remote Network
SC - Service Connection
MU GW - Mobile User Gateway
What is the default behavior in PAN-OS when a 12 MB portable executable (PE) fe is forwarded to the WildFire cloud service?
Which three categories are identified as best practices in the Best Practice Assessment tool? (Choose three.)
Which three considerations should be made prior to installing a decryption policy on the NGFW? (Choose three.)
A customer is concerned about zero-day targeted attacks against its intellectual property.
Which solution informs a customer whether an attack is specifically targeted at them?
Which two features are key in preventing unknown targeted attacks? (Choose two)
How do you configure the rate of file submissions to WildFire in the NGFW?



