CompTIA PT0-002 - CompTIA PenTest+ Certification Exam
A penetration tester discovered a vulnerability that has the following CVEs:
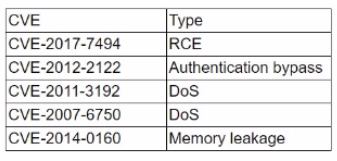
Which of the following CVEs should be remediated first?
A penetration tester uses Hashcat to crack hashes discovered during a penetration test and obtains the following output:
ad09cd16529b5f5a40a3e15344e57649f4a43a267a97f008af01af803603c4c8 : Summer2023 !!
7945bb2bb08731fc8d57680ffa4aefec91c784d231de029c610b778eda5ef48b:p@ssWord123
ea88ceab69cb2fb8bdcf9ef4df884af219fffbffab473ec13f20326dc6f84d13: Love-You999
Which of the following is the best way to remediate the penetration tester's discovery?
During a security assessment, a penetration tester decides to write the following Python script: import requests
x= ['OPTIONS', 'TRACE', 'TEST'l
for y in x;
z - requests.request(y, 'http://server.net ')
print(y, z.status_code, z.reason)
Which of the following is the penetration tester trying to accomplish? (Select two).
A penetration tester is preparing a credential stuffing attack against a company's website. Which of the following can be used to passively get the most relevant information?
A penetration tester would like to know if any web servers or mail servers are running on the in-scope network segment. Which of the following is the best to use in this scenario?
During the execution of a cloud penetration test, a tester was able to gain an initial footprint on the customer cloud infrastructure. Now the tester wants to scan the cloud resources, possible misconfigurations, and other relevant data that could be exploited. Which of the following tools should the tester most likely use?
A penetration tester is performing a vulnerability scan on a large ATM network. One of the organization's requirements is that the scan does not affect legitimate clients' usage of the ATMs. Which of the following should the tester do to best meet the company's vulnerability scan requirements?
A penetration tester runs the following command:
l.comptia.local axfr comptia.local
which of the following types of information would be provided?
Which of the following documents describes activities that are prohibited during a scheduled penetration test?
A penetration tester wrote the following Bash script to brute force a local service password:
..ting as expected. Which of the following changes should the penetration tester make to get the script to work?



