Microsoft SC-400 - Microsoft Information Protection Administrator
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label1 and publish Label1 to all users and groups.
You have the following files on a computer:
• File1.doc
• File2.docx
• File3.xlsx
• File4.txt
You need to identify which files can have Label1 applied. Which files should you identify?
You have a Microsoft 365 tenant that is opt-in for trainable classifiers.
You need to ensure that a user named User1 can create custom trainable classifiers. The solution must use the principle of least privilege.
Which role should you assign to User1?
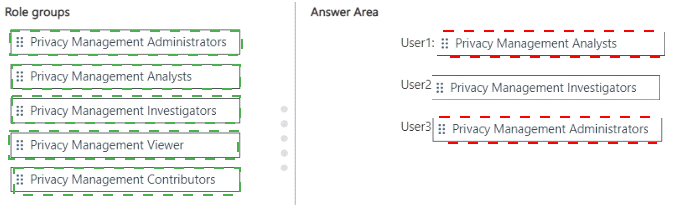
You have a Microsoft 365 E5 subscription and use Microsoft Purview.
The subscription contains the following users:
• User1: Must be able to investigate policy matches, but unable to view the file content related to the match.
• User2: Must be able to investigate policy matches and view the file content related to the match.
• User3: Must be able to create, update, and delete Microsoft Priva Privacy Risk Management policies.
You need to add each user to a role group. The solution must follow the principle of least privilege.
To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
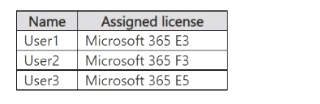
You have a Microsoft 365 subscription that contains the users shown in the following table.
You review the audit retention period of each user. Which users' audit logs are retained for nine months?
You have a Microsoft 365 E5 subscription.
You are implementing insider risk management
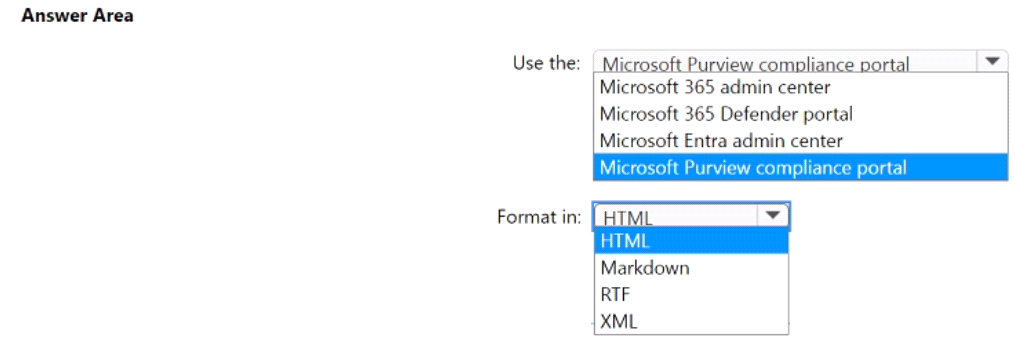
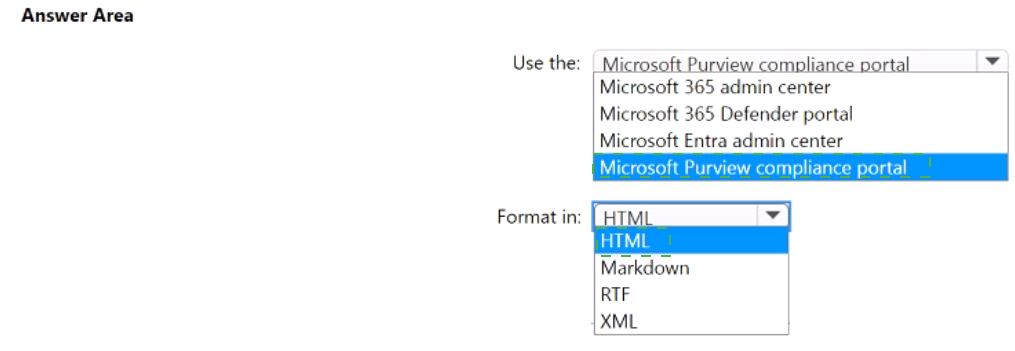
You need to create an insider risk management notice template and format the message body of the notice template.
How should you configure the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement a solution that meets the compliance requirements for the Windows 10 computers.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each coned selection is worth one point.
You need to recommend a solution that meets the compliance requirements for Dropbox.
What should you recommend?
You need to recommend a solution that meets the compliance requirements for viewing DLP tooltip
justifications.
What should you recommend?
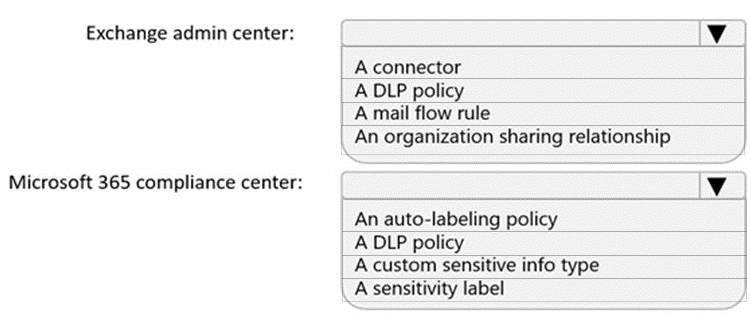
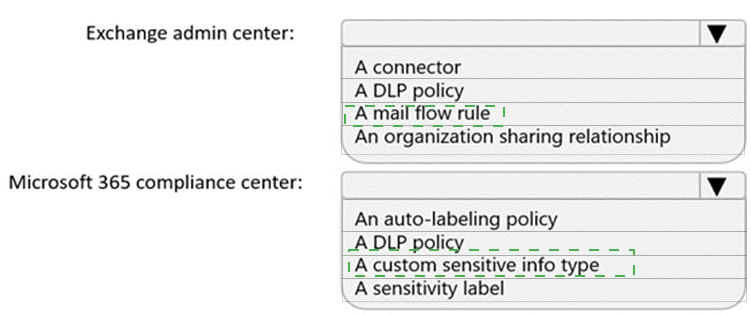
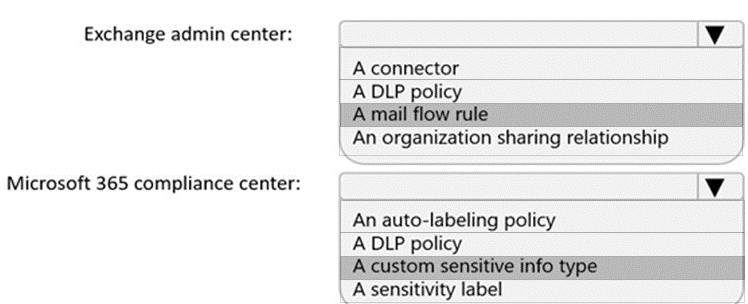
You need to implement a solution to encrypt email. The solution must meet the compliance requirements.
What should you create in the Exchange admin center and the Microsoft 36.S compliance center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to configuration the Microsoft 365 Records management settings by using the CSV file must meet the compliance requirements.
What should you recommend?