Amazon Web Services SOA-C01 - AWS Certified SysOps Administrator - Associate
A SysOps Administrator is configuring AWS SSO tor the first time. The Administrator has already created a directory in the master account using AWS Directory Service and enabled full access in AWS Organizations
What should the Administrator do next to configure the service?
A company has received a notification in its AWS Personal Health Dashboard that one of its Amazon EBS-backed Amazon EC2 instances is on hardware that is scheduled maintenance The instance runs a critical production workload that must be available during normal business hours
Which steps will ensure that the instance maintenance does not produce an outage?
An Applications team has successfully deployed an AWS CloudFormation stack consisting of 30 t2-medium Amazon EC2 instances in the us-west-2 Region. When using the same template to launch a stack in us-east-2, the launch failed and rolled back after launching only 10 EC2 instances.
What is a possible cause of this failure?
A company designed a specialized Amazon EC2 instance configuration for its Data Scientists. The Data Scientists want to create end delete EC2 instances on their own, but are not comfortable with configuring all the settings for EC2 instances without assistance. The configuration runs proprietary software that must be kept private within the company's AWS accounts and should be available to the Data Scientists, but no other users within the accounts.
Which solution should a SysOps Administrator use to allow the Data Scientists to deploy their workloads with MINIMAL effort?
A SysOps Administrator needs to monitor all the object upload and download activity of a single Amazon S3 bucket. Monitoring most include tracking the AWS account of the catier, the IAM user role of the caller, the time of the API call, and the IP address of the API.
Where can the administrator find this information?
A SysOps Administrator is notified that an automated failover of an Amazon RDS database has occurred.
What are possible causes for this? (Choose two.)
An existing data management application is running on a single Amazon EC2 instance and needs to be moved to a new AWS Region in another AWS account. How can a SysOps administrator achieve this while maintaining the security of the application?
Based on the AWS Shared Responsibility Model, which of the following actions are the responsibility of the customer for an Aurora database?
A SySOps Administrator has created a new Amazon S3 bucket named mybucket for the Operations team. Members of the team are part of an IAM group to which the following IAM policy has been assigned.
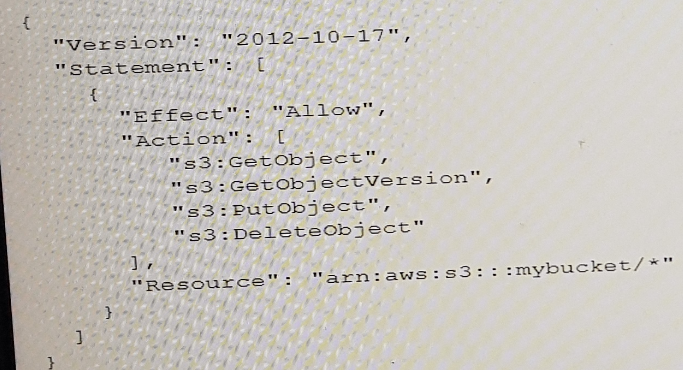
Which of the following actions will be allowed on the bucket? (Select TWO.)
A SysOps Administrator must secure AWS CloudTrail logs. The Security team is concerned that an employee may modify or attempt to delete CloudTrail log files from its Amazon S3 bucket.
Which practices ensure that the log files are available and unaltered? (Choose two.)



