Splunk SPLK-1005 - Splunk Cloud Certified Admin
A customer has worked with their LDAP administrator to configure an LDAP strategy in Splunk. The configuration works, and user Mia can log into Splunk using her LDAP Account. After some time, the Splunk Cloud administrator needs to move Mia from the user role to the power role. How should they accomplish this?
Which of the following app installation scenarios can be achieved without involving Splunk Support?
Which of the following files is used for both search-time and index-time configuration?
Li was asked to create a Splunk configuration to monitor syslog files stored on Linux servers at their organization. This configuration will be pushed out to multiple systems via a Splunk app using the on-prem deployment server.
The system administrators have provided Li with a directory listing for the logging locations on three syslog hosts, which are representative of the file structure for all systems collecting this data. An example from each system is shown below:
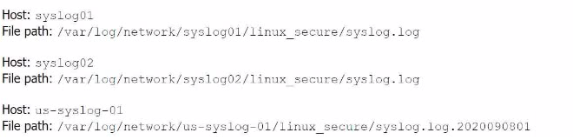
A)

B)

C)
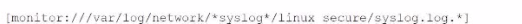
D)

How is it possible to test a script from the Splunk perspective before using it within a scripted input?
How are HTTP Event Collector (HEC) tokens configured in a managed Splunk Cloud environment?
Which of the following is not considered a best practice for the deployment server?
When creating a new index, which of the following is true about archiving expired events?
For the following data, what would be the correct attribute/value oair to use to successfully extract the correct timestamp from all the events?
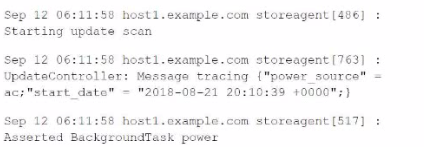
Given the following set of files, which of the monitor stanzas below will result in Splunk monitoring all of the files ending with .log?
Files:
/var/log/www1/secure.log
/var/log/www1/access.log
/var/log/www2/logs/secure.log
/var/log/www2/access.log
/var/log/www2/access.log.1



