ISC SSCP - Systems Security Certified Practitioner
Which of the following is covered under Crime Insurance Policy Coverage?
Which of the following categories of hackers poses the greatest threat?
Which one of the following represents an ALE calculation?
Which of the following is an advantage of a qualitative over a quantitative risk analysis?
The IP header contains a protocol field. If this field contains the value of 51, what type of data is contained within the ip datagram?
When preparing a business continuity plan, who of the following is responsible for identifying and prioritizing time-critical systems?
When you update records in multiple locations or you make a copy of the whole database at a remote location as a way to achieve the proper level of fault-tolerance and redundancy, it is knows as?
When referring to a computer crime investigation, which of the following would be the MOST important step required in order to preserve and maintain a proper chain of custody of evidence:
Which of the following steps should be one of the first step performed in a Business Impact Analysis (BIA)?
Which of the following results in the most devastating business interruptions?
The deliberate planting of apparent flaws in a system for the purpose of detecting attempted penetrations or confusing an intruder about which flaws to exploit is called:
The MOST common threat that impacts a business's ability to function normally is:
Which of the following questions is less likely to help in assessing an organization's contingency planning controls?
To protect and/or restore lost, corrupted, or deleted information, thereby preserving the data integrity and availability is the purpose of:
What can be best defined as the examination of threat sources against system vulnerabilities to determine the threats for a particular system in a particular operational environment?
Which of the following would best describe secondary evidence?
If your property Insurance has Replacement Cost Valuation (RCV) clause your damaged property will be compensated:
Which of the following specifically addresses cyber attacks against an organization's IT systems?
In the UTP category rating, the tighter the wind:
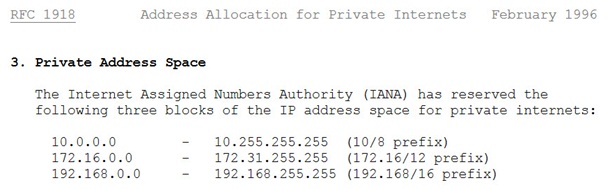
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use on the Internet)?