ISC SSCP - Systems Security Certified Practitioner
Which of the following rules appearing in an Internet firewall policy is inappropriate?
Each data packet is assigned the IP address of the sender and the IP address of the:
Which of the following is NOT an advantage that TACACS+ has over TACACS?
A proxy is considered a:
Why is Network File System (NFS) used?
Which of the following NAT firewall translation modes offers no protection from hacking attacks to an internal host using this functionality?
Which OSI/ISO layer is the Media Access Control (MAC) sublayer part of?
Domain Name Service is a distributed database system that is used to map:
Which of the following can prevent hijacking of a web session?
Secure Shell (SSH-2) provides all the following services except:
The IP header contains a protocol field. If this field contains the value of 17, what type of data is contained within the ip datagram?
What is called an attack in which an attacker floods a system with connection requests but does not respond when the target system replies to those requests?
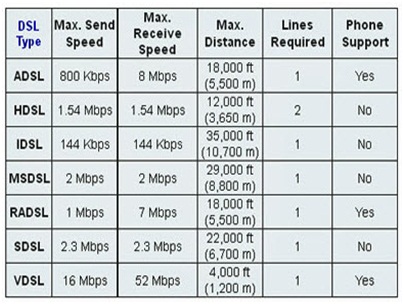
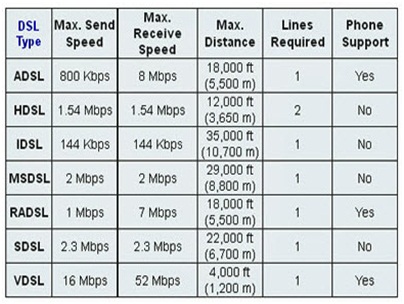
Which xDSL flavour can deliver up to 52 Mbps downstream over a single copper twisted pair?
Which xDSL flavour, appropriate for home or small offices, delivers more bandwidth downstream than upstream and over longer distance?
Which of the following is TRUE regarding Transmission Control Protocol (TCP) and User Datagram Protocol (UDP)?
Which of the following protocols is designed to send individual messages securely?
Secure Shell (SSH) is a strong method of performing:
Which of the following best defines source routing?
Which of the following is a token-passing scheme like token ring that also has a second ring that remains dormant until an error condition is detected on the primary ring?
What can best be defined as a strongly protected computer that is in a network protected by a firewall (or is part of a firewall) and is the only host (or one of only a few hosts) in the network that can be directly accessed from networks on the other side of the firewall?