CompTIA SY0-601 - CompTIA Security+ Exam 2023
A web server log contains two million lines. A security analyst wants to obtain the next 500 lines starting from line 4,600. Which of the following commands will help the security analyst to achieve this objective?
A security manager is attempting to meet multiple security objectives in the next fiscal year. The security manager has proposed the purchase of the following four items:
Vendor A:
1- Firewall
1-12 switch
Vendor B:
1- Firewall
1-12 switch
Which of the following security objectives is the security manager attempting to meet? (Select two).
A systems analyst is responsible for generating a new digital forensics chain -of- custody form Which of the following should the analyst include in this documentation? (Select two).
A security administrator is compiling information from all devices on the local network in order to gain better visibility into user activities. Which of the following is the best solution to meet
this objective?
Which of the following social engineering attacks best describes an email that is primarily intended to mislead recipients into forwarding the email to others?
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be best to help the organization's executives determine their next course of action?
A security administrator is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used for administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
" Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements? (Give Explanation and References from CompTIA Security+ SY0-601 Official Text Book and Resources)
An email security vendor recently added a retroactive alert after discovering a phishing email had already been delivered to an inbox. Which of the following would be the best way for the security administrator to address this type of alert in the future?
A user's laptop constantly disconnects from the Wi-Fi network. Once the laptop reconnects, the user can reach the internet but cannot access shared folders or other network resources. Which of the following types of attacks is the user MOST likely experiencing?
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
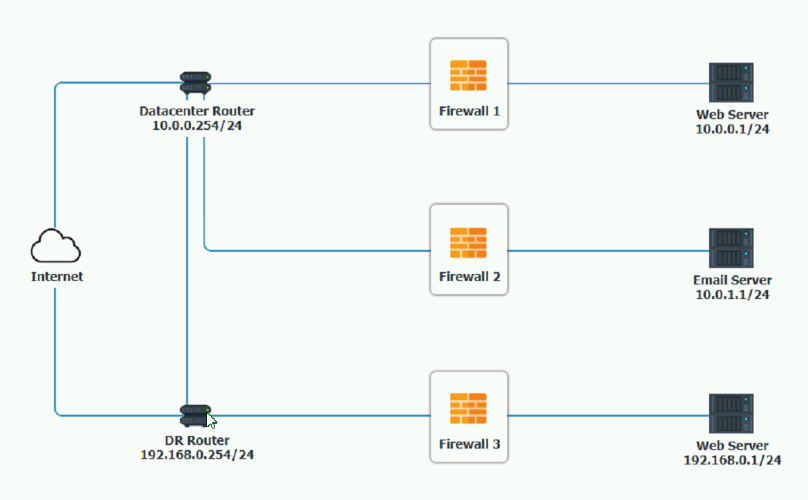
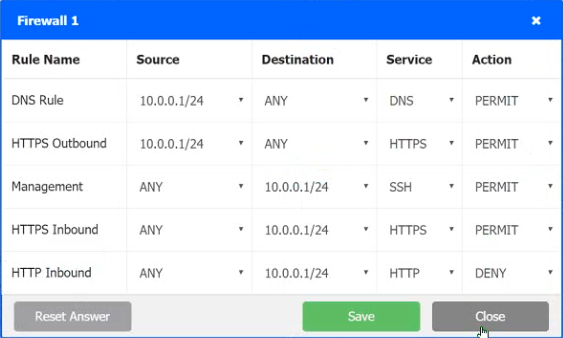
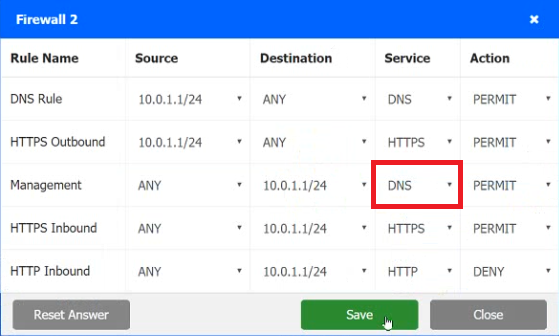
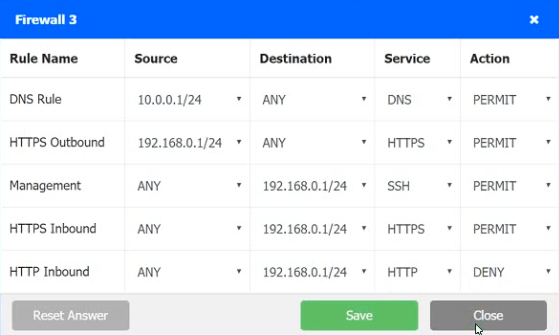
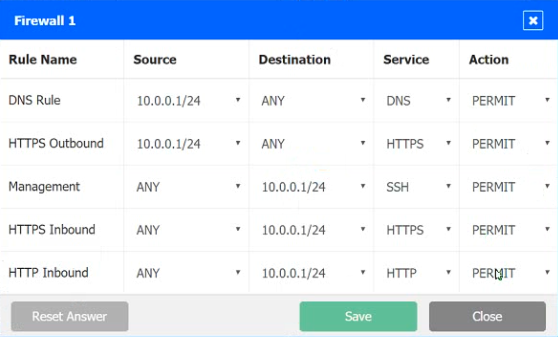
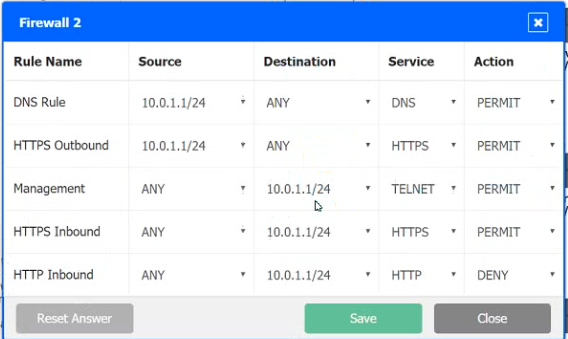
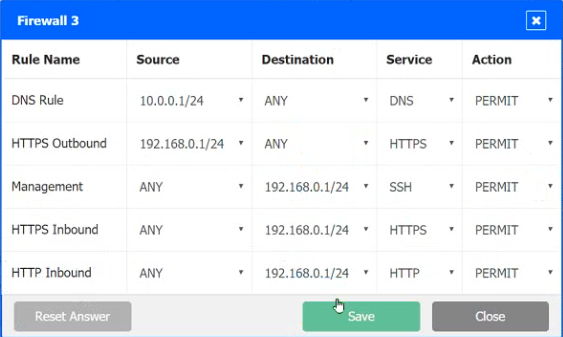
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
A security team is engaging a third-party vendor to do a penetration test of a new proprietary application prior to its release. Which of the following documents would the third-party vendor
most likely be required to review and sign?
A security practitioner is performing due diligence on a vendor that is being considered for cloud services. Which of the following should the practitioner consult for the best insight into the
current security posture of the vendor?
Which of the following describes business units that purchase and implement scripting software without approval from an organization's technology Support staff?
Which of the following best describes a tool used by an organization to identi-fy, log, and track any potential risks and corresponding risk information?
A network engineer receives a call regarding multiple LAN-connected devices that are on the same switch. The devices have suddenly been experiencing speed and latency issues while connecting to network resources. The engineer enters the command show mac address-table and reviews the following output
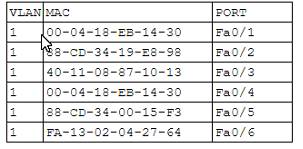
Which of the following best describes the attack that is currently in progress?
A security analyst is using OSINT to gather information to verify whether company data is available publicly. Which of the following is the BEST application for the analyst to use?
An engineer is using scripting to deploy a network in a cloud environment. Which the following describes this scenario?
Audit logs indicate an administrative account that belongs to a security engineer has been locked out multiple times during the day. The security engineer has been on vacation (or a few days. Which of the following attacks can the account lockout be attributed to?
An engineer recently deployed a group of 100 web servers in a cloud environment. Per the security policy, all web-server ports except 443 should be disabled. Which of the following can be
used to accomplish this task?
A user is trying to upload a tax document, which the corporate finance department requested, but a security program IS prohibiting the upload A security analyst determines the file contains Pll, Which of
the following steps can the analyst take to correct this issue?