CompTIA SY0-601 - CompTIA Security+ Exam 2023
Which of the following describes the reason root cause analysis should be conducted as part of incident response?
During an investigation, events from two affected servers in the same subnetwork occurred at the same time:
Server 1: 192.168.10.1 [01/Apr/2021:06:00:00 PST] SAN access denied for user 'admin' Server 2: 192.168.10.6 [01/Apr/2021:06:01:01 CST] SAN access successful for user 'admin
Which of the following should be consistently configured to prevent the issue seen in the logs?
A threat actor used a sophisticated attack to breach a well-known ride-sharing. company. The threat actor posted on social media that this action was in response to the company's treatment of its drivers Which of the following best describes tm type of throat actor?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following is the most likely reason for this compromise?
A company is working with a vendor to perform a penetration test. Which of the following includes an estimate about the number of hours required to complete the engagement?
Following a prolonged data center outage that affected web-based sales, a company has decided to move its operations to a private cloud solution The security team has received the following requirements
• There must be visibility into how teams are using cloud-based services
• The company must be able to identity when data related to payment cards is being sent to the cloud
• Data must be available regardless of the end user's geographic location
• Administrators need a single pane-of-glass view into traffic and trends
Which of the following should the security analyst recommend?
A new vulnerability enables a type of malware that allows the unauthorized movement of data from a system Which of the following would detect this behavior?
A security architect at a large, multinational organization is concerned about the complexities and overhead of managing multiple encryption keys securely in a multicioud provider
environment. The security architect is looking for a solution with reduced latency to allow the incorporation of the organization's existing keys and to maintain consistent, centralized control
and management regardless of the data location. Which of the following would best meet the architect's objectives?
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to coiled network traffic between workstations throughout the network The analysts review the following logs:
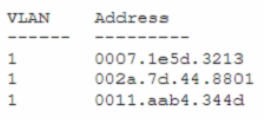
The Layer 2 address table has hundreds of entries similar to the ones above Which of the following attacks has most likely occurred?
A security analyst is reviewing logs on a server and observes the following output:
01/01/2020 03:33:23 admin attempted login with password sneak
01/01/2020 03:33:32 admin attempted login with password sneaked
01/01/2020 03:33:41 admin attempted login with password sneaker
01/01/2020 03:33:50 admin attempted login with password sneer
01/01/2020 03:33:59 admin attempted login with password sneeze
01/01/2020 03:34:08 admin attempted login with password sneezy
Which of the following is the security analyst observing?
A security analyst receives a SIEM alert that someone logged in to the app admin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
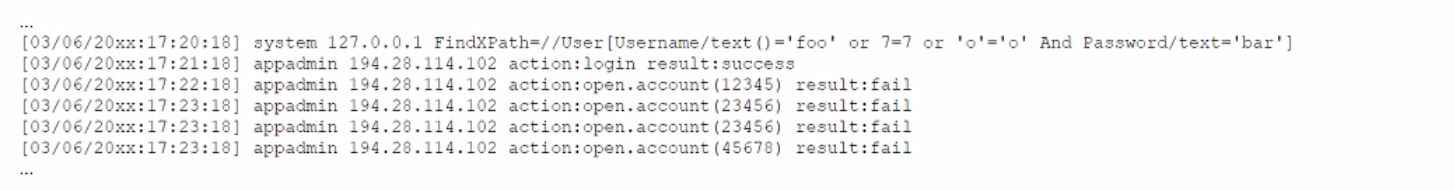
Which of the following can the security analyst conclude?
A dynamic application vulnerability scan identified that code injection could be performed using a web form. Which of the following will be the best remediation to prevent this vulnerability?
A host was infected with malware. During the incident response. Joe, a user, reported that he did not receive any emails with links, but he had been browsing the internet all day. Which of the following would most likely show where the malware originated?
A systems administrator is auditing all company servers to ensure they meet the minimum security baseline While auditing a Linux server the systems administrator observes the /etc/ahadow file has permissions beyond the baseline recommendation. Which of the following commands should the systems administrator use to resolve this issue?
A security analyst it investigating an incident to determine what an attacker was able to do on a compromised Laptop. The analyst reviews the following SIEM log:
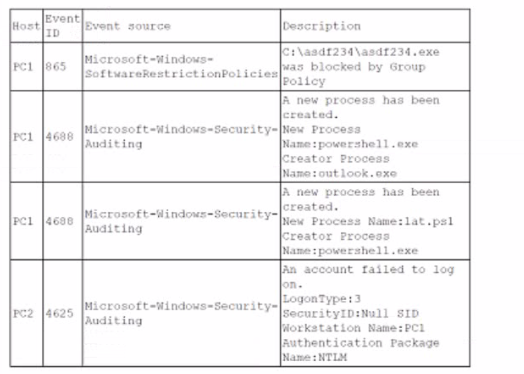
Which of the following describes the method that was used to compromise the laptop?
A security engineer must deploy two wireless routers in an office suite Other tenants in the office building should not be able to connect to this wireless network Which of the following protocols should the engineer implement to ensure the strongest encryption?
Which of the following is an algorithm performed to verify that data has not been modified?
Which of the following describes the ability of code to target a hypervisor from inside a guest OS?
Which of the following agreements defines response time, escalation points, and performance metrics?
Which of the following practices would be best to prevent an insider from introducing malicious code into a company’s development process?



