Veritas VCS-256 - Administration of Veritas InfoScale Availability 7.1 for UNIX/Linux
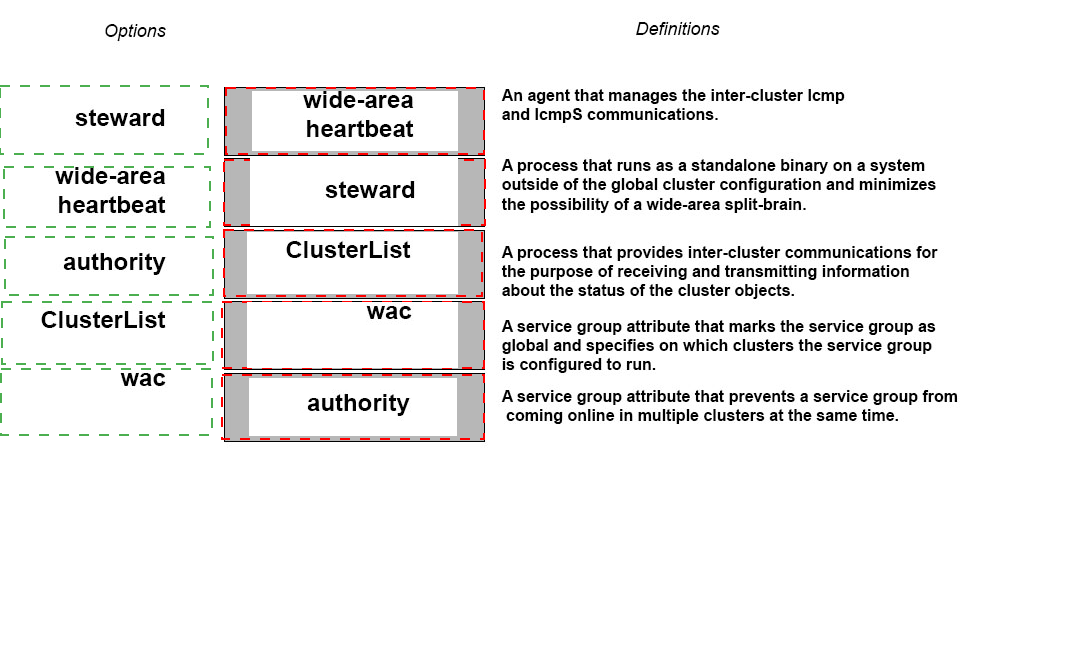
Match all five Veritas Cluster Server global cluster options on the left to the corresponding definitions on the right.
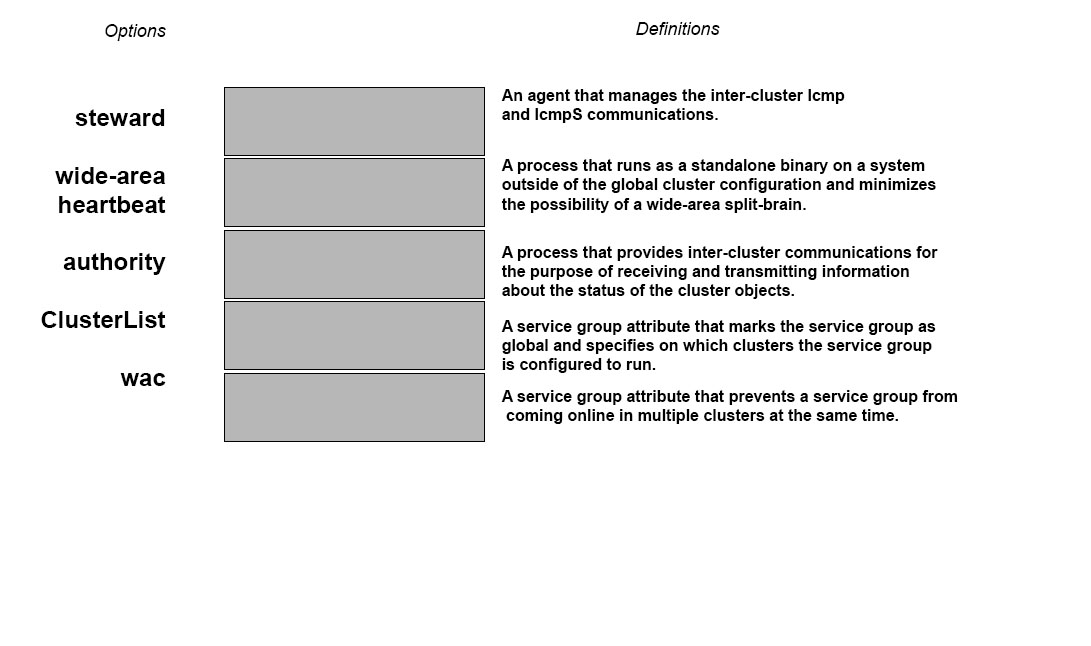
An administrator adds a new Mount resource using the command line. After running the hastatus-sum command, the administrator notices the state of the resource is RESOURCES NOT PROBED.
Which command should the administrator run to allow the resource to be probed?
An administrator is testing a network interface under Veritas Cluster Server (VCS) control and wants to minimize the time for VCS to detect the fault. How can this be accomplished without affecting any other network interfaces under VCS control?
What is the purpose of the AutoClearLimit attribute?
Which resource type can an administrator use to mirror the state of another persistent resource?
Which two capabilities can an administrator use to ensure availability within Docker Containers? (Select two.)
A cluster administrator wants to deploy a complex cluster configuration that will include over six nodes, I/O fencing, and multiple private cluster interconnections. The administrator has a week to prepare before the actual cluster nodes become available for software installation.
Which method will help the administrator to implement rapid cluster deployment?
What are two resource types that Proxy resources can reference? (Select two.)
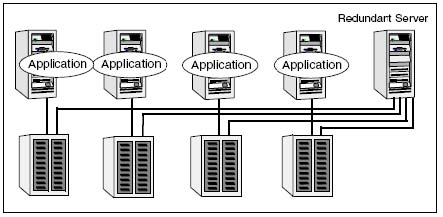
Refer to the exhibit.
The exhibit shows an N-to-1 cluster configuration, in which nodes are connected to storage devices via dual-hosted SCSI cables.
Why is this an inefficient configuration?
An administrator is responsible for a stretched cluster between two data centers in different locations. The data is mirrored between sites. How should the configuration be deployed to maximize resilience if the administrator wants to set up I/O fencing?