HRCI aPHRi - Associate Professional in Human Resources - International
Which of the following should HR do to prepare to interview a candidate?
What initiative aims to create a workforce that reflects the local population and an organization’s customers?
The stage during which an employee’s suitability for the job is determined is known as:
Stalking text messages and threatening emails are examples of:
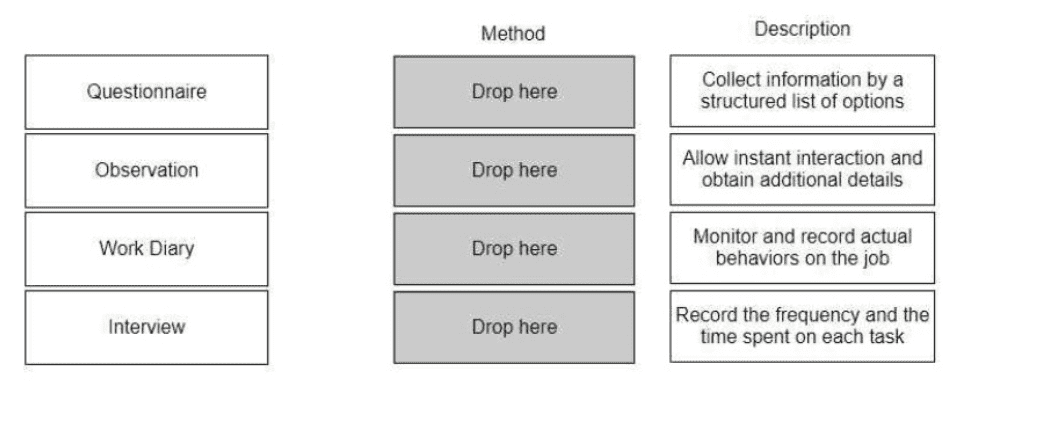
Match the job analysis method to the correct description.
Employees are most likely to experience a high level of job satisfaction when their jobs include:
Which of the following is the best option for measuring the monetary value of a training program?
A key indicator of an engaged employee is:
Which of the following best defines the process of promoting an organization as desirable in the labor market?
To help protect the internal network, an organization should:




