Checkpoint 156-215.81 - Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20)
What Identity Agent allows packet tagging and computer authentication?
Consider the Global Properties following settings:
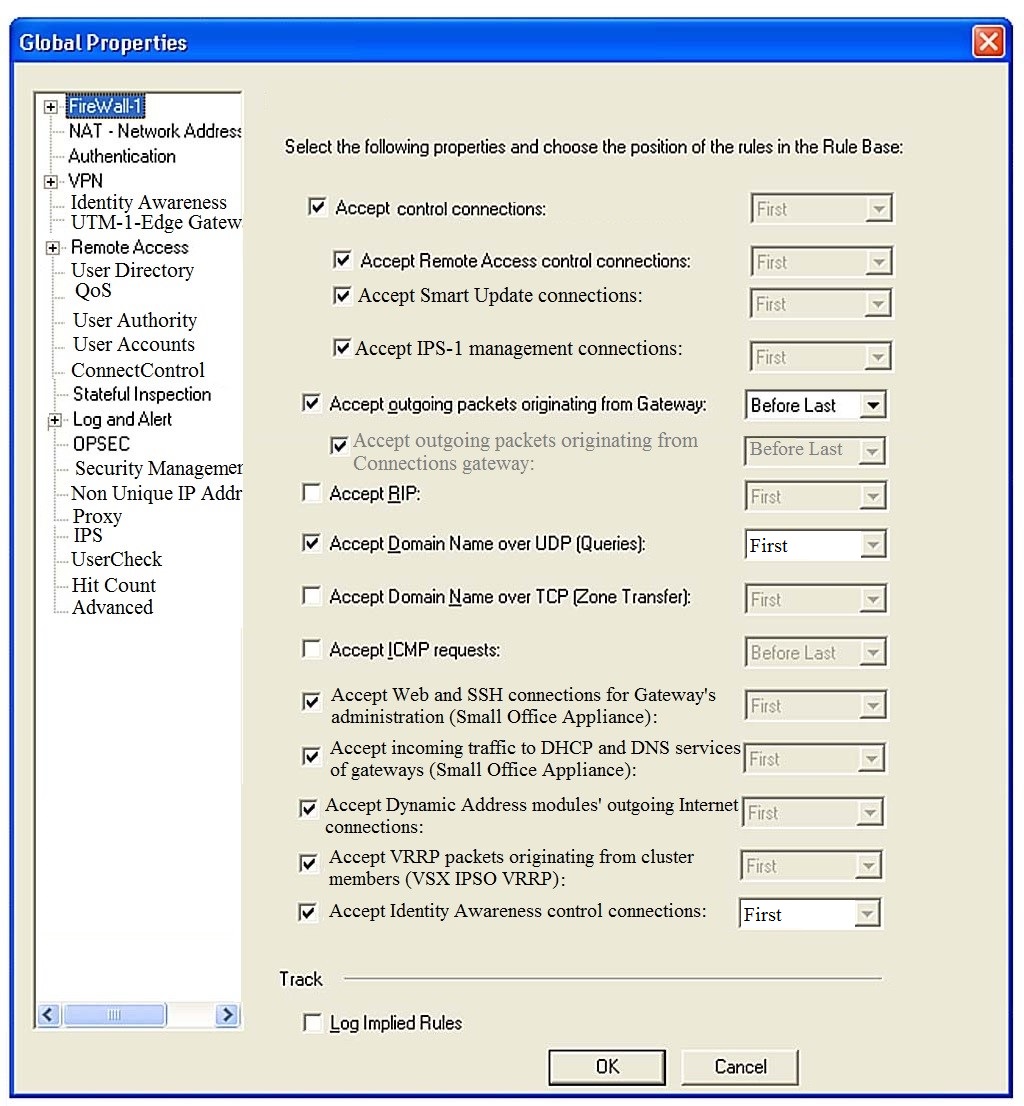
The selected option “Accept Domain Name over UDP (Queries)†means:
AdminA and AdminB are both logged in on SmartConsole What does it mean if AdmmB sees a lock icon on a rule? Choose the BEST answer.
Which command is used to add users to or from existing roles?
Which Check Point supported authentication scheme typically requires a user to possess a token?
What are the steps to configure the HTTPS Inspection Policy?
What object type would you use to grant network access to an LDAP user group?
Which is a main component of the Check Point security management architecture?
Fill in the blanks: The _______ collects logs and sends them to the _______.
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?



