Checkpoint 156-215.81 - Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20)
Why is a Central License the preferred and recommended method of licensing?
Examine the sample Rule Base.
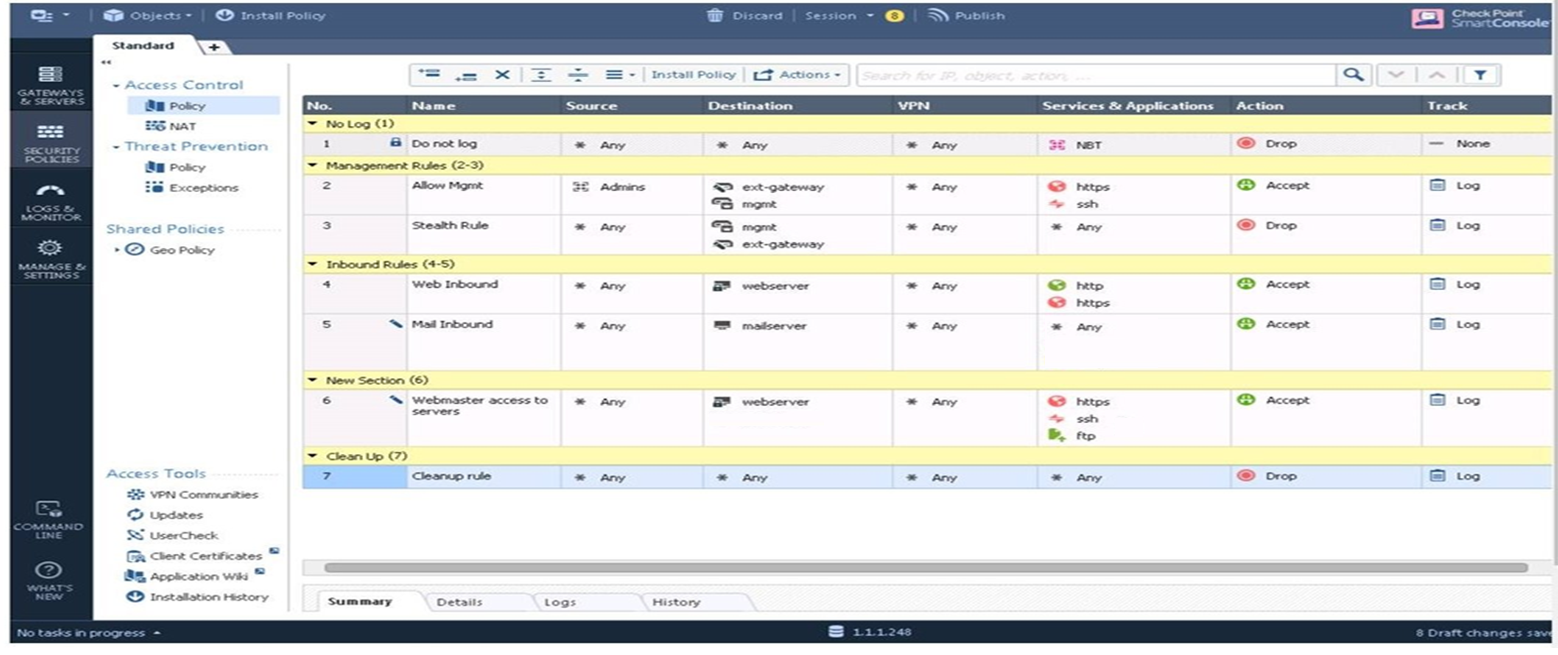
What will be the result of a verification of the policy from SmartConsole?
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
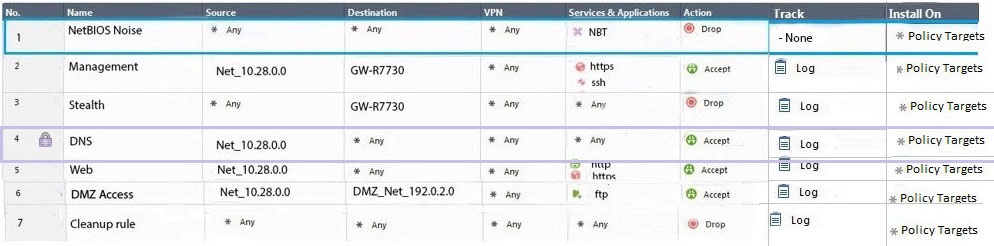
What is the possible explanation for this?
Which of the following is NOT a component of Check Point Capsule?
Fill in the blank: Authentication rules are defined for ____________.
Which encryption algorithm is the least secured?
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
Which GUI tool can be used to view and apply Check Point licenses?
When enabling tracking on a rule, what is the default option?
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?



