CIW 1D0-571 - CIW v5 Security Essentials
You want to create a certificate for use in a Secure Sockets Layer (SSL) session. Which of the following is responsible for verifying the identity of an individual and also issuing the certificate?
An application is creating hashes of each file on an attached storage device. Which of the following will typically occur during this process?
Which choice lists typical firewall functions?
Which of the following is the primary weakness of symmetric-key encryption?
You have determined that an attack is currently underway on your database server. An attacker is currently logged in, modifying data. You want to preserve logs, caching and other data on this affected server. Which of the following actions will best allow you to stop the attack and still preserve data?
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
Which of the following details should be included in documentation of an attack?
Consider the following diagram:
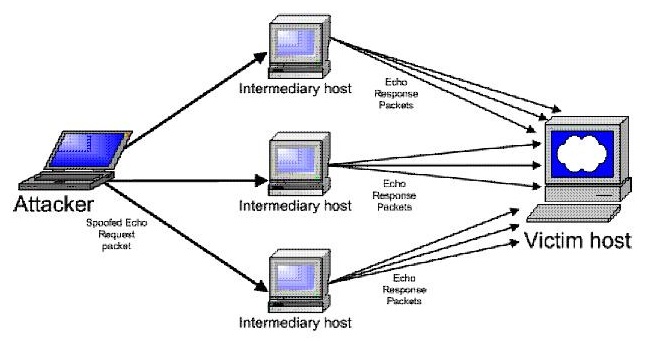
Which type of attack is occurring?
A CGI application on the company's Web server has a bug written into it. This particular bug allows the application to write data into an area of memory that has not been properly allocated to the application. An attacker has created an application that takes advantage of this bug to obtain credit card information. Which of the following security threats is the attacker exploiting, and what can be done to solve the problem?
Which of the following is a primary weakness of asymmetric-key encryption?



