Oracle 1z0-116 - Oracle Database Security Administration
Which two configurations can be used to protect sensitive data In a database?
Examine this output:
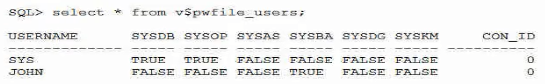
Which three are true?
Examine this parameter In sqinet.ora:
SQLNET.ADTHENTICATION_SEBVICES=(NONE)
For which two cases do you need a password file?
You must mask data consistently In three database copies such that data relations across the databases remain In place.
Which Data Masking Format allows this?
Which four products, features, or methods can help facilitate compliance with various privacy-related regulatory requirements such as PCI-DSS and the EU GDPR?
You configured Kerberos authentication for databases running on servers A and B.
However a database link connecting the database on server A to the database on server B fails with ORA-12638 Credential retrieval failed.
Where must you make a change to sqlnet.ora to allow the database link to use its stored credentials Instead of trying to use Kerberos?
You are Implementing a security policy that makes use of the USERENV namespace.
Which USERRENV value does not change for the duration of a session?
Which statement can be used to force password complexity in the password file?
Examine the statement:
CREATE BOLE hr_admin IDENTIFIED USING pac_mgr.hr_admin_rola_ch9ck;
Which three are true about the sec_mgr. hr_admin_role_check procedure?
You grant user JANE the SYSDBA administrative privilege. Which two are true?



