Oracle 1z0-116 - Oracle Database Security Administration
Which two are true about auditing in an Oracle Database?
Which two statements are true about the Secure External Password Store (SEPS)?
Which two statements are true about column-level transparent data encryption?
Which two statements are true about Database Vault factors?
Which two statements are true about Valid Node Checking for Registration (VNCR)?
Examine these commands and responses:
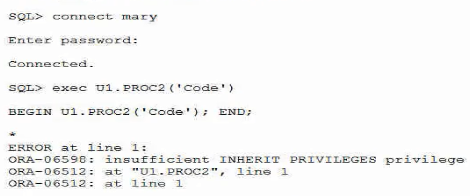
Which object privilege must be granted to allow execution of the stored procedure?
You check the Risk Matrix of the latest Critical Patch Update (CPU).
One of the " Common Vulnerability and Exposure’’ reports (CVEs) has Base Score that is above 9 in the Risk Matrix.
Which one is not a supported method to address this CVE?
While upgrading your Oracle database server from 10g to 19c, you want to ensure that the users can still connect with their current passwords after the upgrade.
What do you need to set explicitly for this purpose?
Which type of masking directly masks and subsets data In a nonproduction database with minimal or no Impact on production environments?
Which three are true concerning command rules?



