Oracle 1z0-134 - Oracle WebLogic Server 12c: Advanced Administrator II
You are analyzing the JMSDeliveryMode header field for all the messages for all the queues deployed to your JMSServer.
Which two values do you expect to find for this header? (Choose two.)
In order to leverage replication and high availability features of the underlying database, you have configured a JDBC TLOG to persist transaction logs in your database.
However, WebLogic Server cannot successfully connect to your database at start up.
Which outcome should you expect? (Choose the best answer.)
Examine the domain diagram:
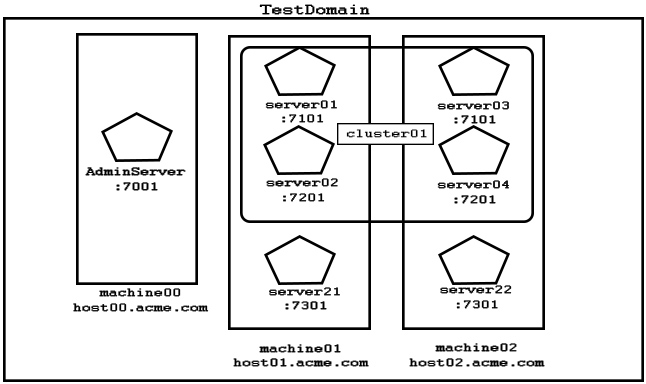
You are asked to write a WLST script that will print the current available heap size for server04.
Assuming:
all servers are running
you have just started an offline, interactive WLST session
a domain-scoped node manager is running on each machine, listening oт port :5556
the username/password “weblogic/Welcome1†maps to a valid domain administrator and Node Manager client
Which two code options will accomplish this task? (Choose two.)
You need to ensure that when a failed admin server instance is restarted on another machine with a different IP address, the managed server is able to establish connection with the newly started instance.
Which technique will ensure that the connection can be made? (Choose the best answer.)
In order to increase scalability and high availability you are configuring WebLogic clustering with JMS distributed destinations.
Which recommendation will ensure optimal load balancing of the message processing?
A hardware load-balancer (HWLB) is positioned as the primary entry point into your WebLogic Server domain. Aspects of your application use SSL to protect data on the network from your clients to your domain.
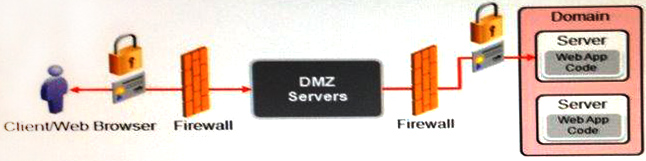
Which configuration provides the best performance for your domain? (Choose the best answer.)
You are tasked with doing a rolling upgrade of a production domain that will minimize service interruptions.
Which is a characteristic of a rolling update? (Choose the best answer.)
I am configuring the security policy for my JMS module. I am specifying some security conditions for the module.
Which two security conditions are valid in this context? (Choose two.)
You are configuring the principals needed to fulfill the security requirements of an application within a sandbox environment that uses the WebLogic Server-embedded LDAP server.
The given security requirements provided have outlined the following facts about some test principals:
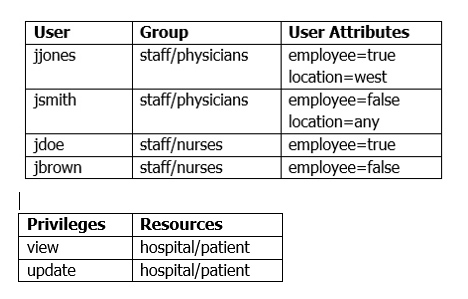
One security requirement states that internal patient data can be viewed only by physicians who are employees.
What is an appropriate way to fulfill this security requirement from a principal perspective using the provided information?
What is the file extension for a domain extension template? (Choose the best answer.)



