Oracle 1z0-591 - Oracle Business Intelligence Foundation Suite 11g Essentials
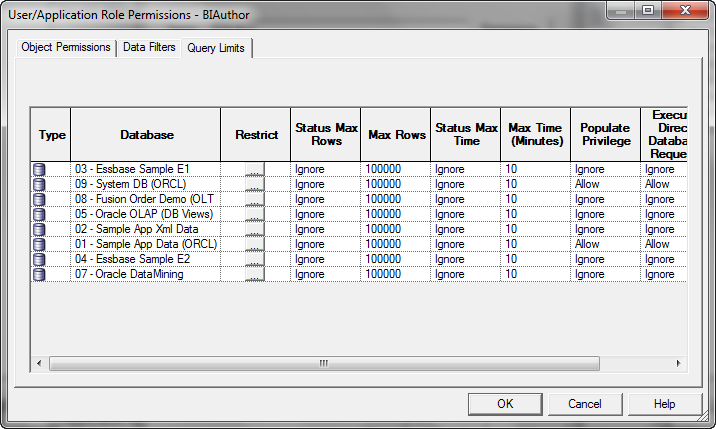
Query Limits are used to manage Query environment in the repository for users and roles and can_________.
The ODBC DSN is never used for _______.
How will you model a Type II Slowly-Changing Dimension?
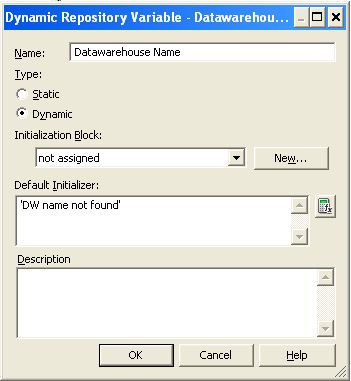
Which two options are valid Repository Variable names?
What is the process in which there is redundancy of data to improve performance?
A customer frequently queries multiple dimension tables without a measure. What needs to be defined in the presentation layer?
When a customer wants to get sales numbers by day, how is data stored in the Star Schema, if the data is loaded nightly?
Use of the Enterprise Install option is recommended for which three options?
An organization has its employees' names in an Employees table, and information about their jobs in a Jobs table.
However, an organization's employees can have multiple jobs, and the same job can be performed by multiple employees. This situation would result in a many to-many relationship between the Employees and Jobs tables. How can the many to-many relationship issue be resolved?
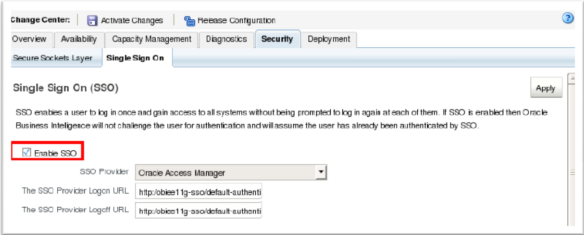
Which task can be performed after the Administrator link has been reached through logging into OBIEE?