Oracle 1z0-888 - MySQL 5.7 Database Administrator
What is the order of tables shown in an EXPLAIN output?
You are contacted by a user who does not have permission to access a database table. You determine after investigation that this user should be permitted to have access and so you execute a GRANT statement to enable the user to access the table.
Which statement describes the activation of that access for the user?
You created a backup of the world database with this command:
shell> mysqldump --opt world > dump.sql
Which two will import the data from dump.sql? (Choose two.)
Which two methods accurately monitor the size of your total database size over time? (Choose two.)
These details are shown when logged in to an account:
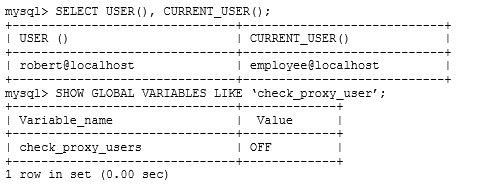
Which set of statements would match the accounts shown?
You have installed the validate_password plug-in and set the validate_password_policy variable.
Which validation is affected by the validate_password_policy setting?
An admin attempts to enforce stronger security by using these commands:
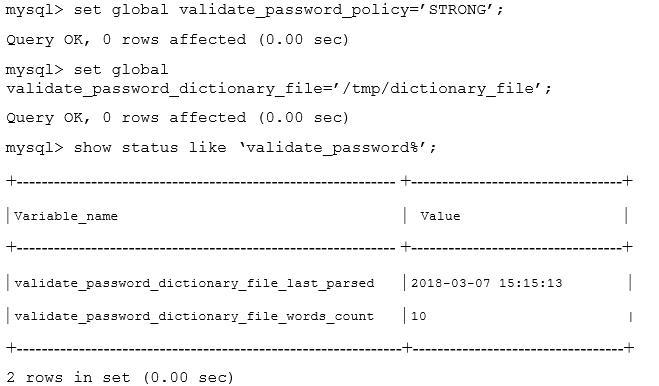
The admin then leaves the system running with the specified changes. What are two remaining security concerns? (Choose two.)



