Cisco 200-301 - Cisco Certified Network Associate
Which command configures the Cisco WLC to prevent a serial session with the WLC CLI from being automatical togged out?
How does network automation help reduce network downtime?
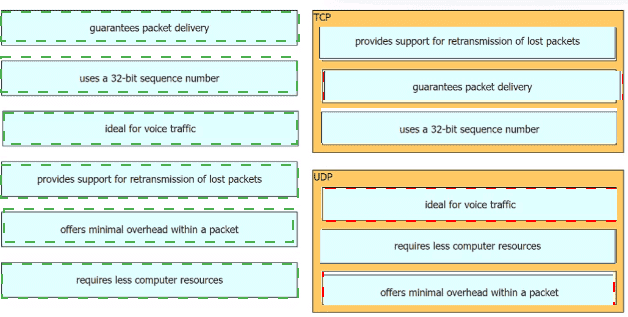
Drag and drop the characteristics of transport layer protocols from the left onto the corresponding protocols on the right.
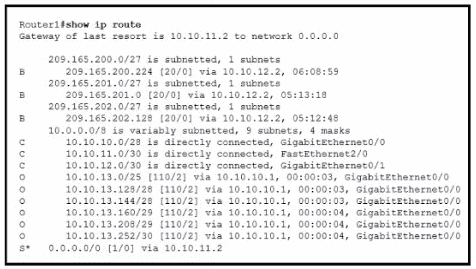
Refer to the exhibit. Drag and drop the subnet masks from the left onto the corresponding subnets on the right. Not all subnet masks used.
How does authentication differ from authorization?
Refer the exhibit.
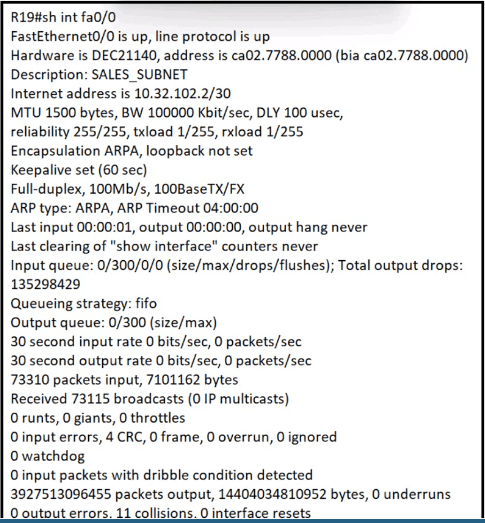
What is the cause of poor performance on router R19?
What is the role of syslog level 7 in network device health monitoring?
Refer to the exhibit.
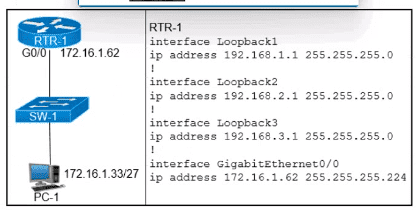
Which configuration for RTR-1 deniess SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
A)
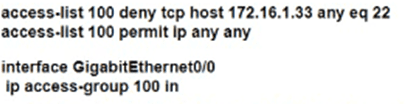
B)
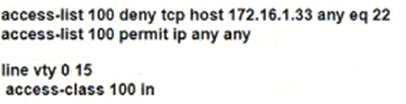
C)
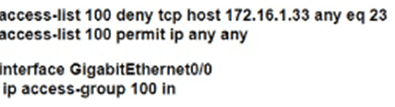
D)
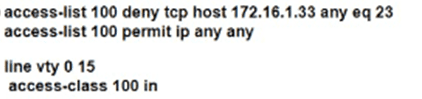
Refer to the exhibit.
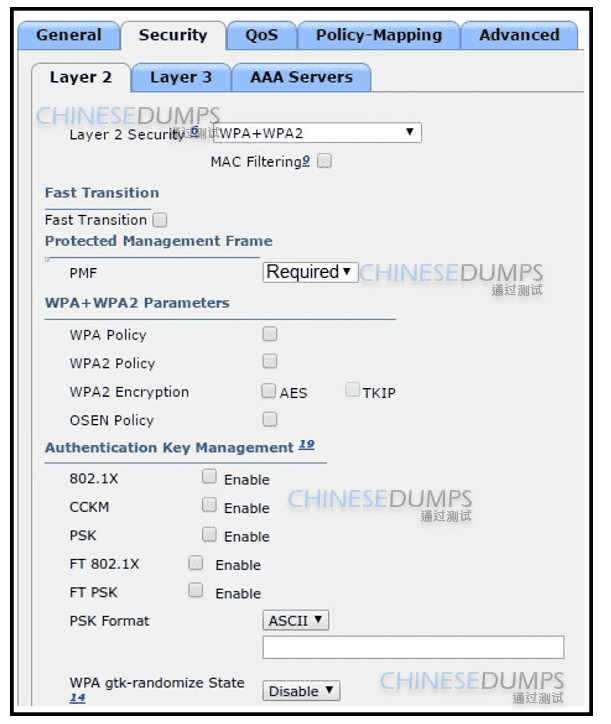
The network engineer is configuring a new WLAN and is told to use a setup password for authentication instead of the RADIUS servers. Which additional set of tasks must the engineer perform to complete the configuration?
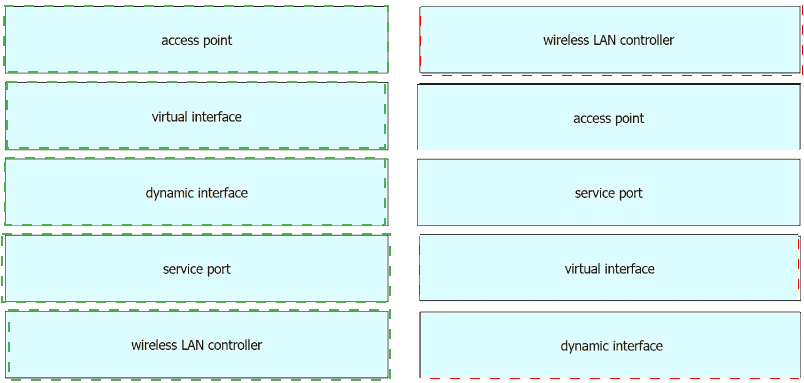
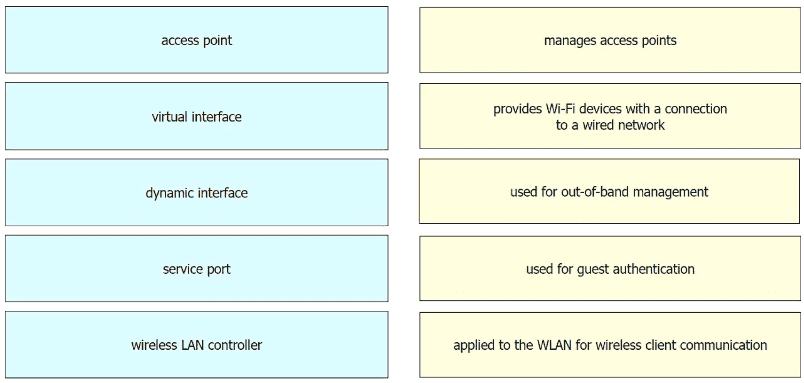
Drag and drop the WLAN components from the left onto the component details on the right.
NO: 105
What is the MAC address used with VRRP as a virtual address?
What differentiates the Cisco OfficeExtend AP mode from FlexConnect AP mode?
What are two characteristics of a small office / home office connection environment? (Choose two.)
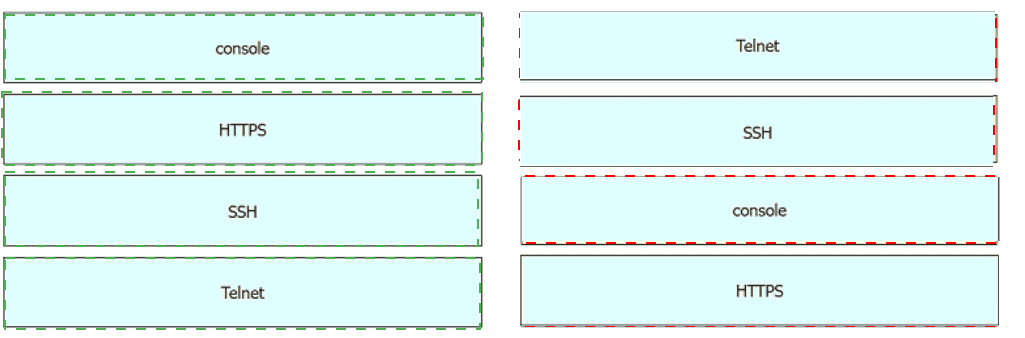
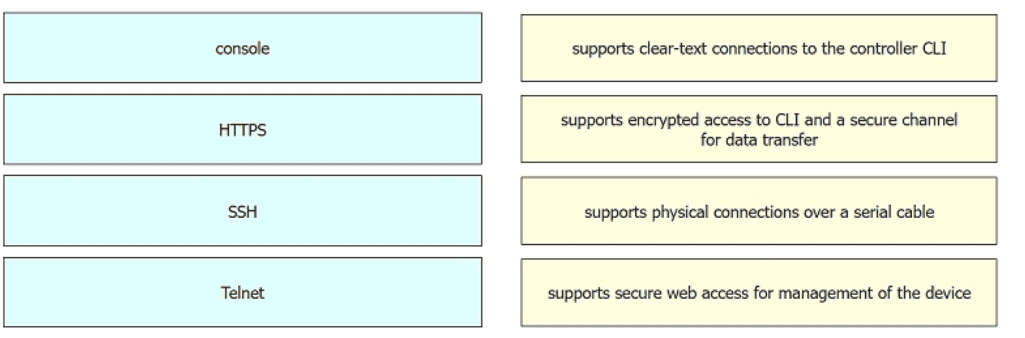
Drag and drop the management connection types from the left onto the definitions on the right.
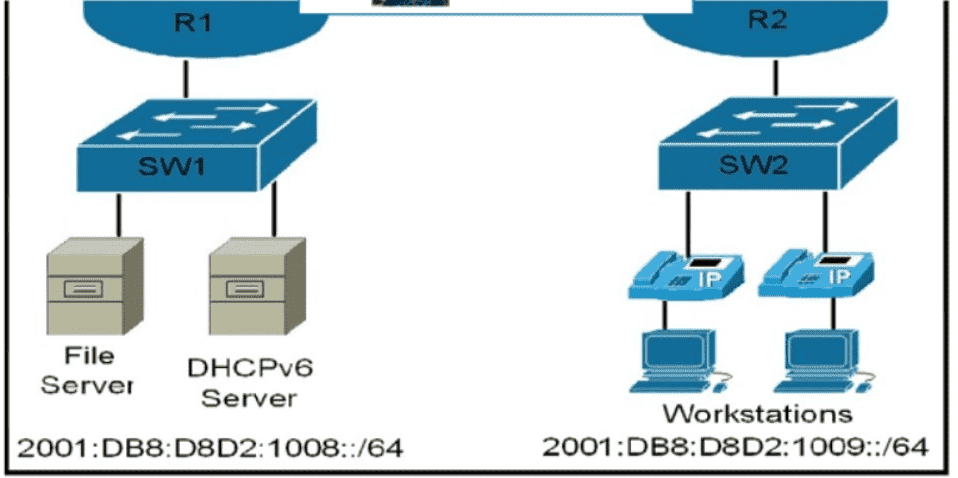
Refer to the exhibit An IPv6 address must be obtained automatically on the LAN interface on R1 Which command must be implemented to accomplish the task?
Refer to the exhibit.
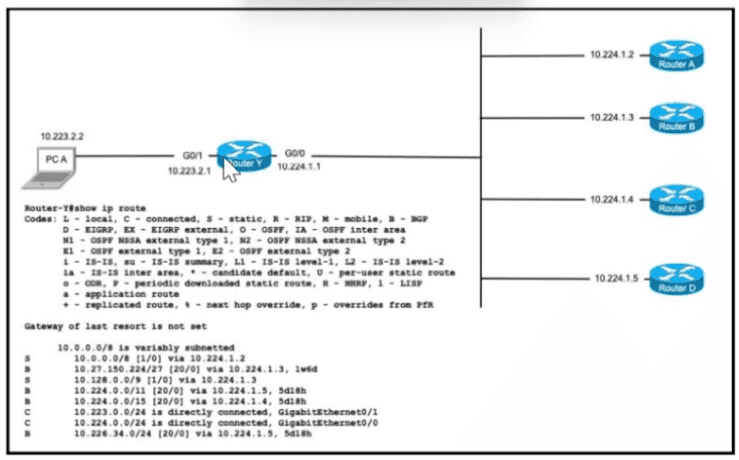
PC A is communicating with another device at IP address 10.227.225.255. Through which router does router Y route the traffic?
What should a network administrator consider when deciding to implement automation?
Refer to the exhibit.
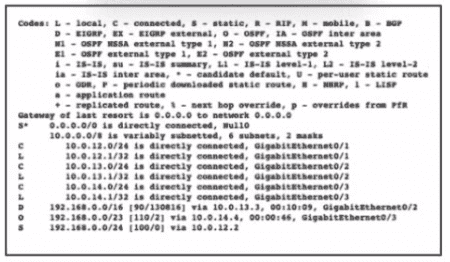
Which interface is chosen to forward traffic to the host at 192.168.0.55?
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the next-hop devices are different?
Refer to the exhibit.
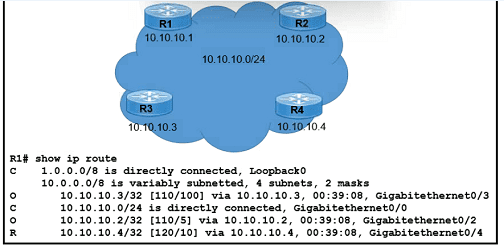
Which next-hop IP address has the least desirable metric when sourced from R1?