Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
What is the role of a firewall in an enterprise network?
Refer to the exhibit.
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

What is the primary purpose of a First Hop Redundancy Protocol?
Which WAN access technology is preferred for a small office / home office architecture?
What does a router do when configured with the default DNS lookup settings, and a URL is entered on the CLI?
Refer to the exhibit.
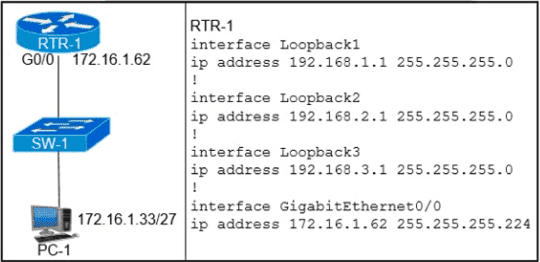
Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
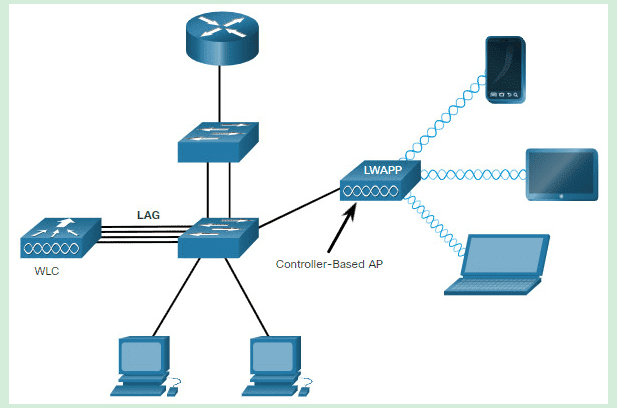
What is a benefit of using a Cisco Wireless LAN Controller?
What is a role of wireless controllers in an enterprise network?
Which level of severity must be set to get informational syslogs?
Which statement identifies the functionality of virtual machines?
Which command automatically generates an IPv6 address from a specified IPv6 prefix and MAC address of an interface?
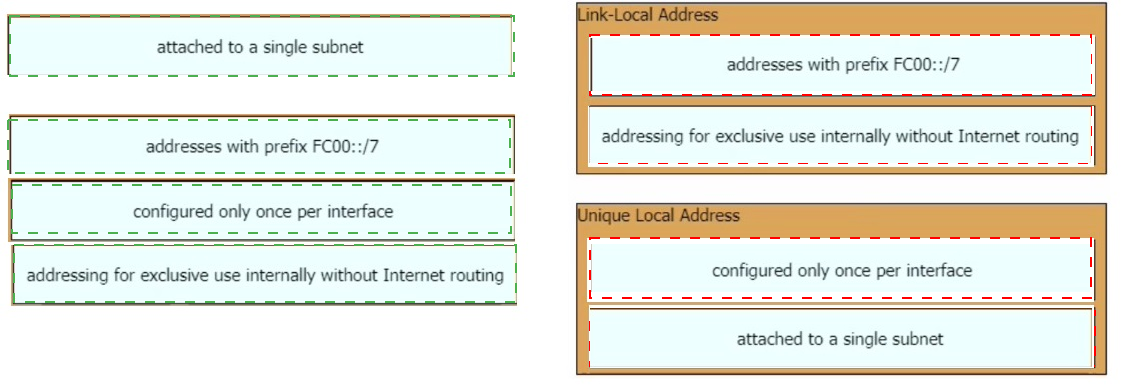
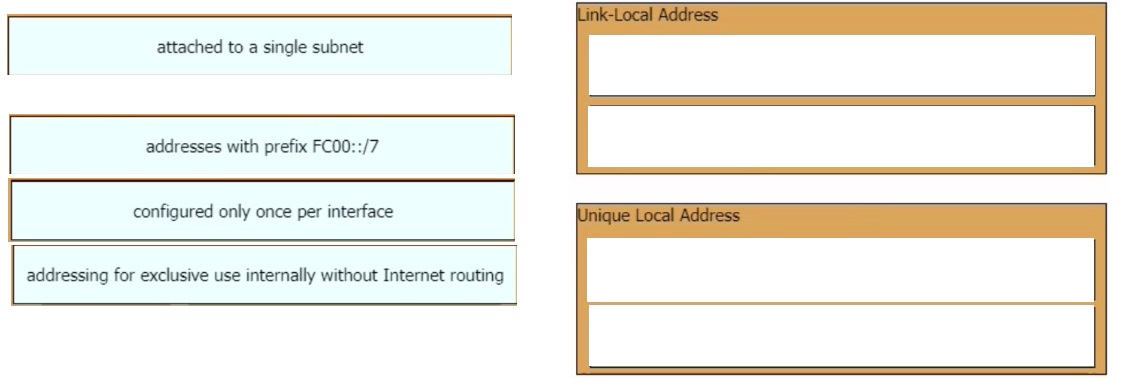
Drag and drop the IPv6 address type characteristics from the left to the right.
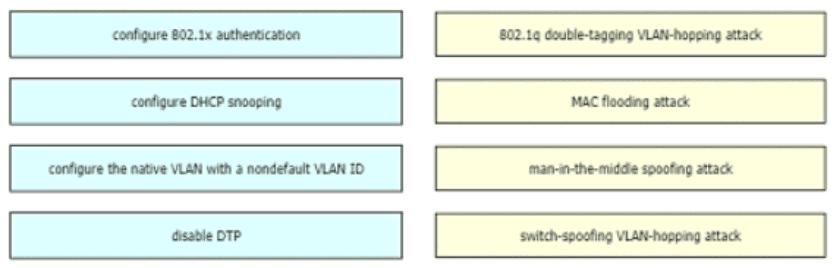
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
Which technology is appropriate for communication between an SDN controller and applications running over the network?
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
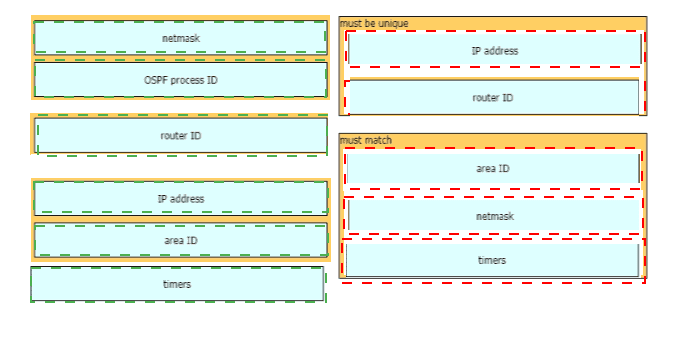
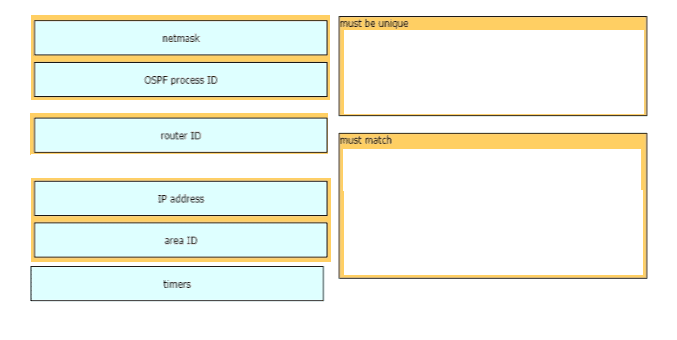
A network engineer is configuring an OSPFv2 neighbor adjacency Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used
What are two southbound APIs? (Choose two )
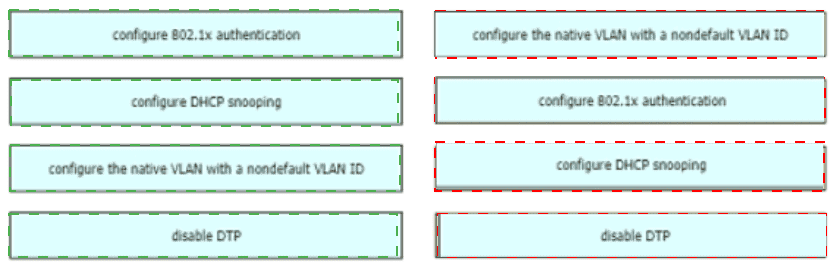
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch.
Which two steps will fulfill the request? (Choose two)
An engineering team asks an implementer to configure syslog for warning conditions and error conditions. Which command does the implementer configure to achieve the desired result?
Which network action occurs within the data plane?
What uses HTTP messages to transfer data to applications residing on different hosts?
What occurs to frames during the process of frame flooding?
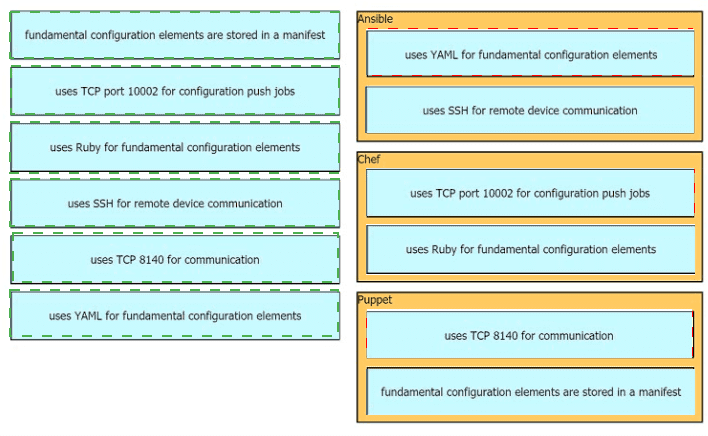
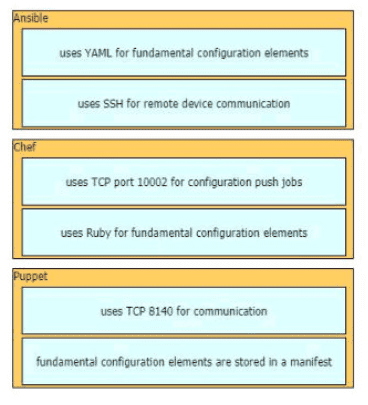
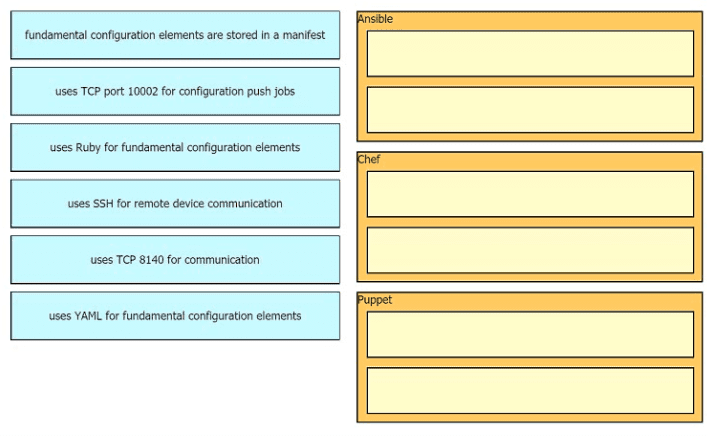
Drag drop the descriptions from the left onto the correct configuration-management technologies on the right.
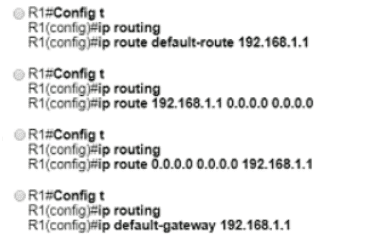
Router R1 must send all traffic without a matching routing-table entry to 192.168.1.1. Which configuration accomplishes this task?
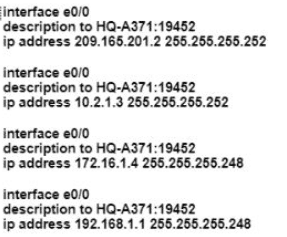
An engineer must configure a/30 subnet between two routers. Which usable IP address and subnet mask combination meets this criteria?
Which IPv6 address block sends packets to a group address rather than a single address?
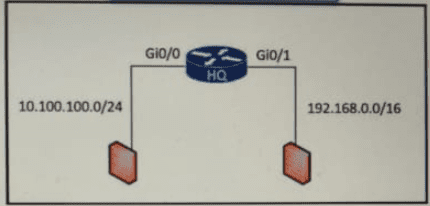
Refer to the exhibit.
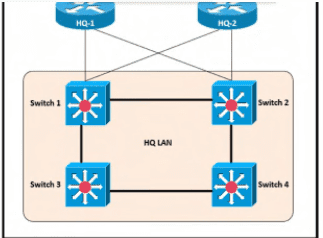
After the election process what is the root bridge in the HQ LAN?
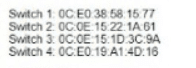
What is a characteristic of cloud-based network topology?
Which network allows devices to communicate without the need to access the Internet?
Which two WAN architecture options help a business scalability and reliability for the network? (Choose two)
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
What causes a port to be placed in the err-disabled state?
Refer to the exhibit.
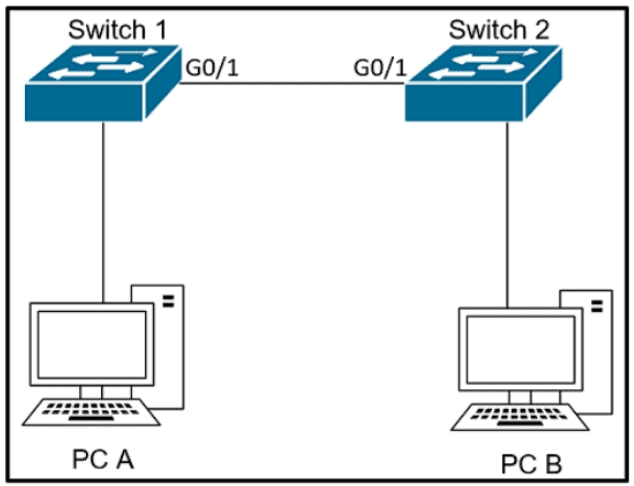
The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and Switch 2 while all other VLANs are to remain tagged.
Which command accomplishes this task?
Which device performs stateful inspection of traffic?
What is the purpose of a southbound API in a control based networking architecture?
What is a DHCP client?
What is recommended for the wireless infrastructure design of an organization?
Refer to the exhibit.
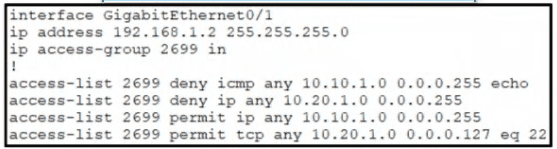
A network administrator must permit SSH access to remotely manage routers in a network. The operations team resides on the 10.20.1.0/25 network. Which command will accomplish this task?
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
Which two encoding methods are supported by REST APIs? (Choose two)
If a notice-level messaging is sent to a syslog server, which event has occurred?
Refer to the exhibit.
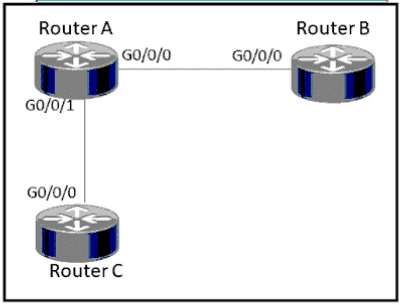
How must router A be configured so that it only sends Cisco Discovery Protocol Information to router C?
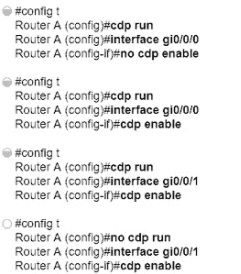
Refer to the exhibit.
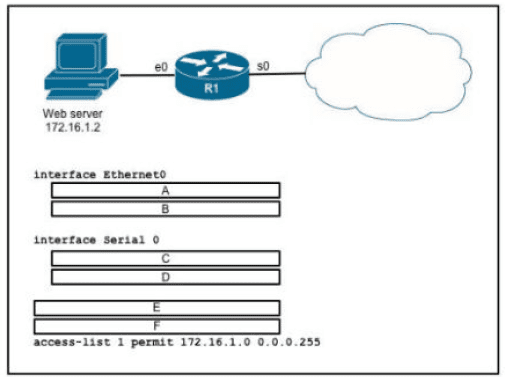
An engineer is configuring the router to provide static NAT for the webserver Drag and drop the configuration commands from the left onto the letters that correspond to its position in the configuration on the right.
What is a function of Wireless LAN Controller?
Refer to the exhibit.

R5 is the current DR on the network, and R4 is the BDR. Their interfaces are flapping, so a network engineer wants the OSPF network to elect a different DR and BDR. Which set of configurations must the engineer implement?
A)

B)

C)

D)

What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
What is the default behavior of a Layer 2 switch when a frame with an unknown destination MAC address is received?
Refer to the exhibit.
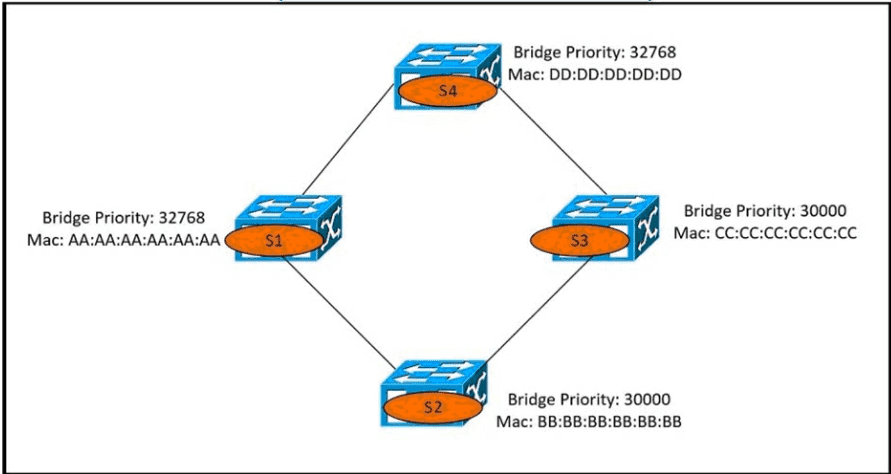
Which switch becomes the root bridge?
What is a recommended approach to avoid co-channel congestion while installing access points that use the 2.4 GHz frequency?