Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
A wireless access point is needed and must meet these requirements:
• "zero-touch" deployed and managed by a WLC
• process only real-time MAC functionality
• used in a split-MAC architecture. Which access point type must be used?
A switch is a forwarding a frame out of an interfaces except the interface that received the frame. What is the technical term for this process?
A)
B)
C)
D)
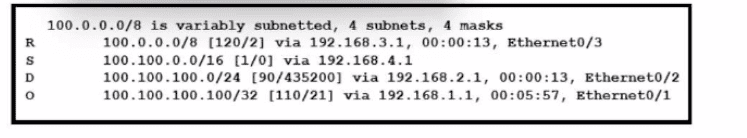
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
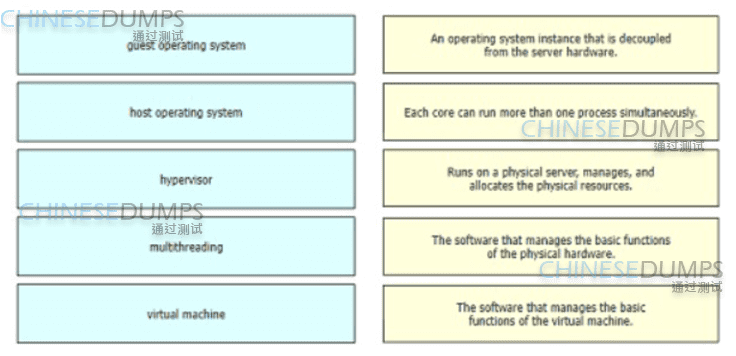
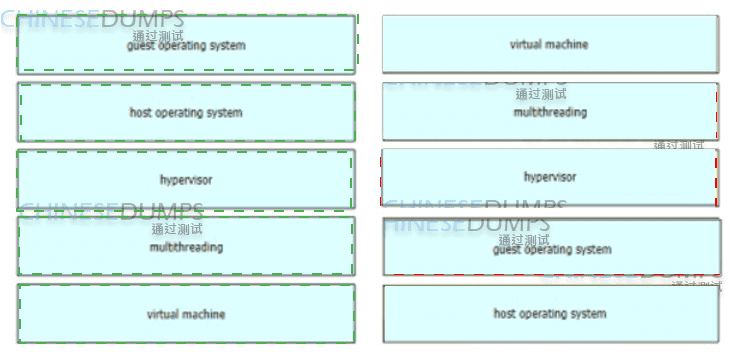
Drag and drop the virtualization concepts from the left onto the matching statements on the right.
Refer to the exhibit.
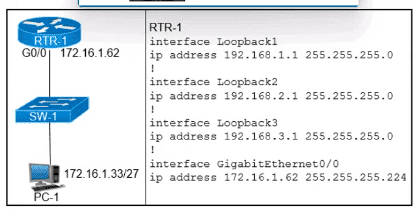
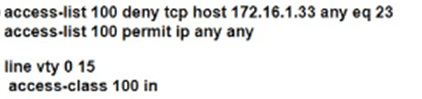
Which configuration for RTR-1 deniess SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
A)
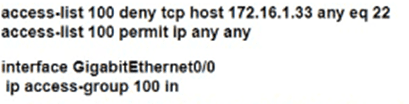
B)
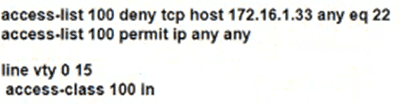
C)
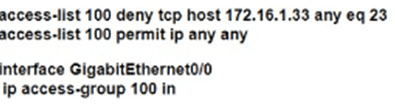
D)
Which type of IPv4 address must be assigned to a server to protect it from external access and allow only internal users access while restricting internet access?
What is the purpose of using First Hop Redundancy Protocol on a specific subnet?
What are two descriptions of three-tier network topologies? (Choose two)
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
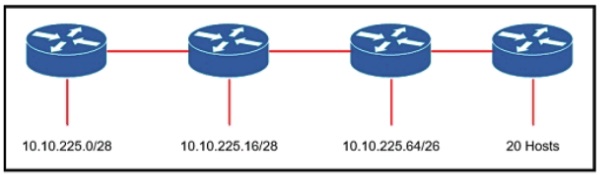
Refer to the exhibit. An engineer must add a subnet for a new office that will add 20 users to the network. Which IPv4 network and subnet mask combination does the engineer assign to minimize wasting addresses?
A network engineer must create a diagram of a multivendor network. Which command must be configured on the Cisco devices so that the topology of the network can be mapped?
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
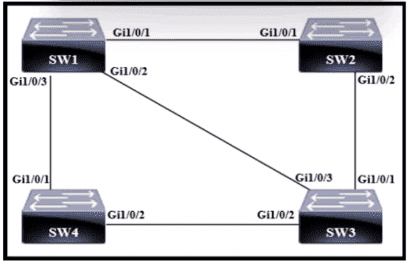
Refer to the exhibit.
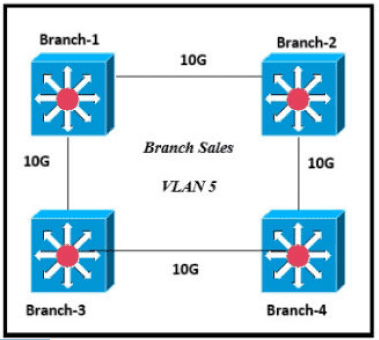
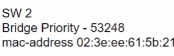
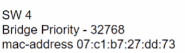
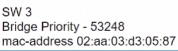
Only four switches are participating in the VLAN spanning-tree process.
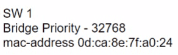
Branch-1 priority 614440
Branch-2: priority 39082416
Branch-3: priority 0
Branch-4: root primary
Which switch becomes the permanent root bridge for VLAN 5?
Refer to the exhibit.
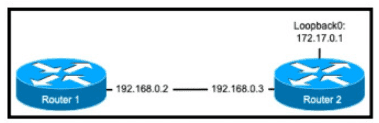
The nip server 192.168.0.3 command has been configured on router 1 to make it an NTP client of router 2. Which command must be configured on router 2 so that it operates in server-only mode and relies only on its internal clock?
which IPv6 address block forwards packets to a multicast address rather than a unicast address?
What is the effect when loopback interfaces and the configured router ID are absent during the OSPF Process configuration?
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
When the active router in an HSRP group fails, what router assumes the role and forwards packets?
Which statement correctly compares traditional networks and controller-based networks?
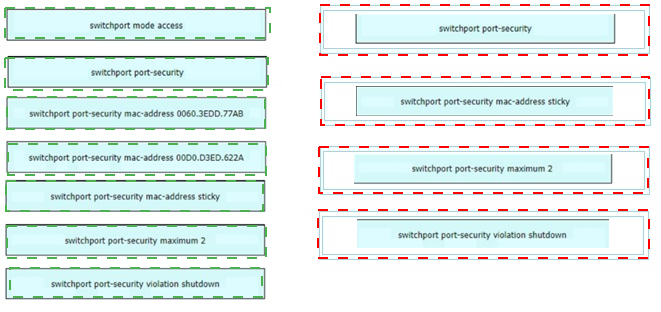
An engineer is tasked to configure a switch with port security to ensure devices that forward unicasts multicasts and broadcasts are unable to flood the port The port must be configured to permit only two random MAC addresses at a time Drag and drop the required configuration commands from the left onto the sequence on the right Not all commands are used.

Refer to the exhibit.
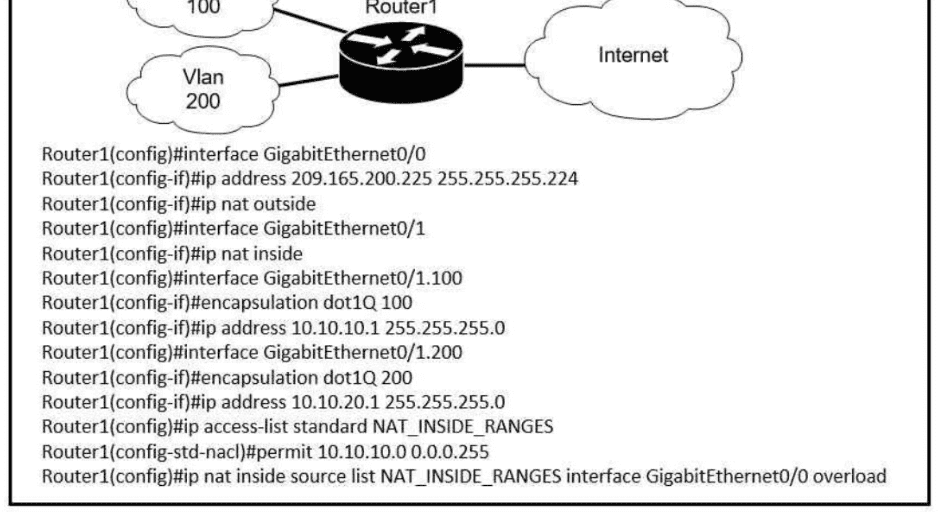
Users on existing VLAN 100 can reach sites on the Internet. Which action must the administrator take to establish connectivity to the Internet for users in VLAN 200?
What is a function of a Next-Generation IPS?
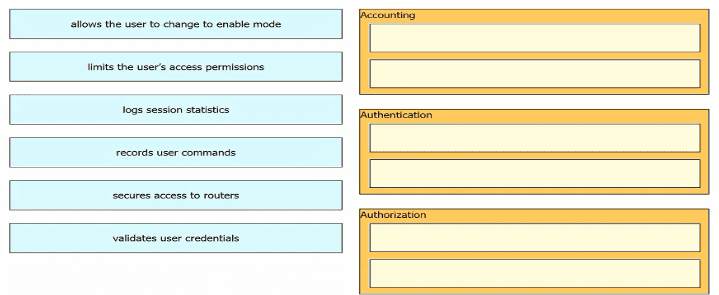
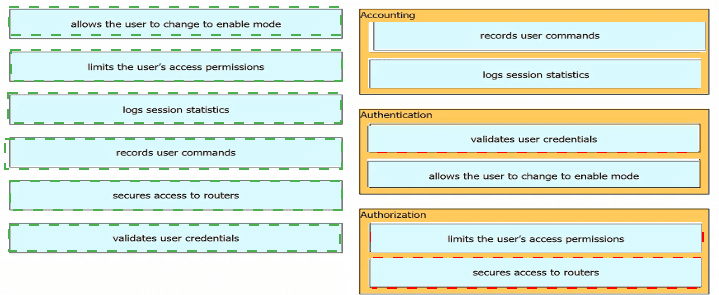
Drag and drop the descriptions of AAA services from the left onto the corresponding services on the right.
What is the purpose of the ip address dhcp command?
Refer to the exhibit.

Packets received by the router from BGP enter via a serial interface at 209.165.201.10. Each route is present within the routing table. Which interface is used to forward traffic with a destination IP of 10.10.10.24?
Refer to the exhibit.
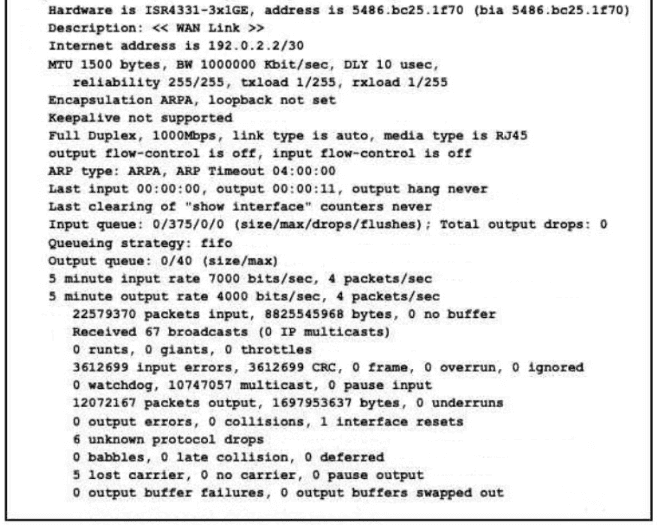
What is a reason for poor performance on the network interface?
Refer to the exhibit.
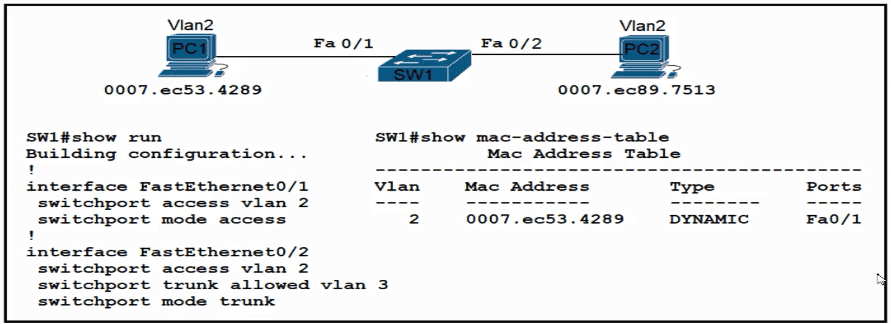
An engineer has started to configure replacement switch SW1. To verify part of the configuration, the engineer issued the commands as shown and noticed that the entry for PC2 is missing. Which change must be applied to SW1 so that PC1 and PC2 communicate normally?
A)
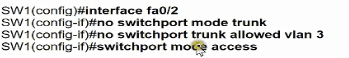
B)

C)
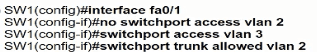
D)
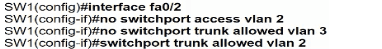
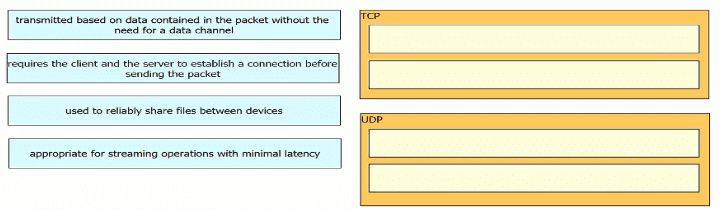
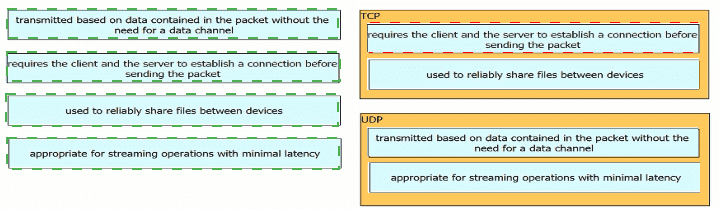
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
A network engineer is installing an IPv6-only capable device. The client has requested that the device IP address be reachable only from the internal network. Which type of IPv6 address must the engineer assign?
Which value is the unique identifier that an access point uses to establish and maintain wireless connectivity to wireless network devices?
Refer to the exhibit.
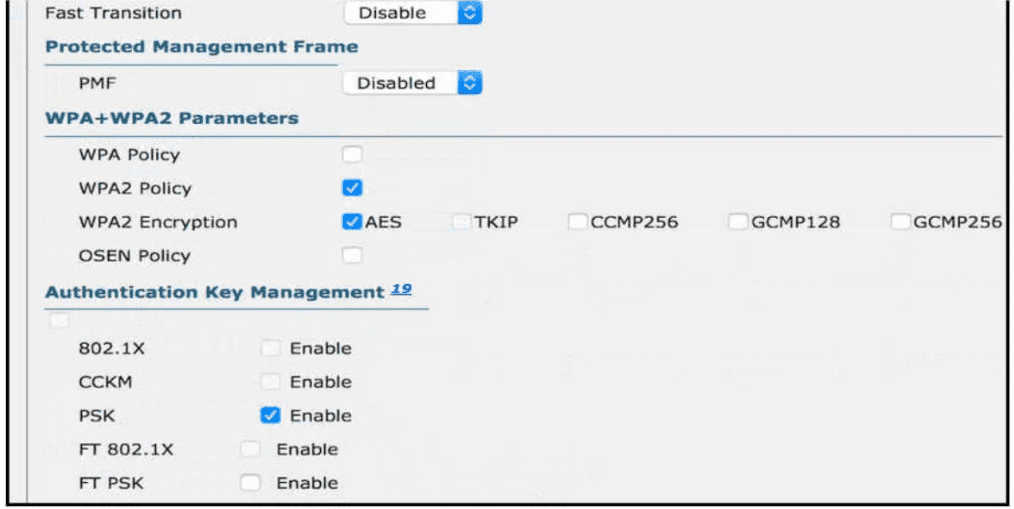
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Refer to the exhibit.
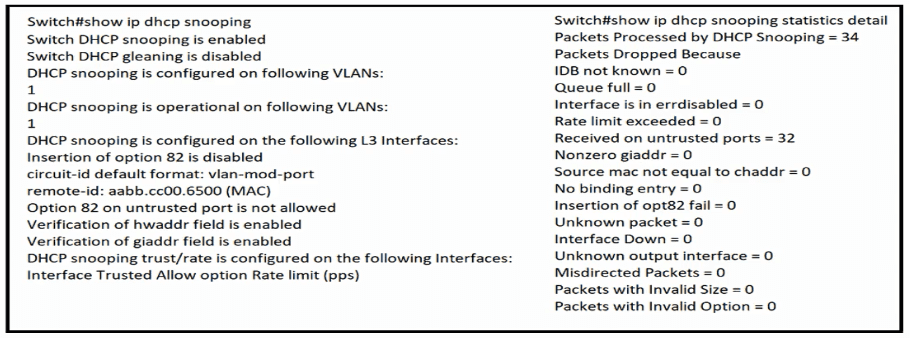
The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on VLAN 1 to receive addresses from the DHCP server?
Refer to the exhibit.

Packets received by the router from BGP enter via a serial interface at 209 165 201 1 Each route is present within the routing table Which interface is used to forward traffic with a destination IP of 10.1.1.19?
Refer to the exhibit.
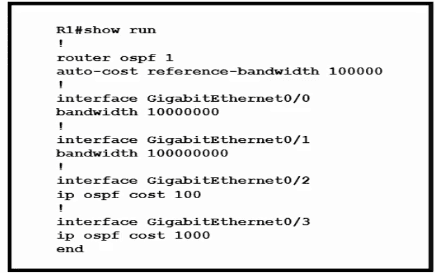
Router R1 resides in OSPF Area 0. After updating the R1 configuration to influence the paths that it will use to direct traffic, an engineer verified that each of the four Gigabit interfaces has the same route to 10.10.0.0/16. Which interface will R1 choose to send traffic to reach the route?
A network administrator is setting up a new IPv6 network using the 64-bit address 2001 0EB8 00C1 2200:0001 0000 0000 0331/64 To simplify the configuration the administrator has decided to compress the address Which IP address must the administrator configure?
An engineer must configure R1 for a new user account. The account must meet these requirements:
* It must be configured in the local database.
* The username is engineer.
* It must use the strongest password configurable. Which command must the engineer configure on the router?
What are two functions of a server on a network? (Choose two)
Refer to the exhibit.
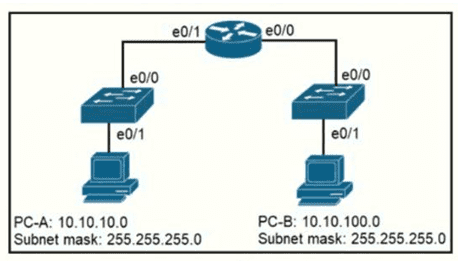
When PC-A sends traffic to PC-B, which network component is in charge of receiving the packet from PC-A verifying the IP addresses, and forwarding the packet to PC-B?
Refer to the exhibit.
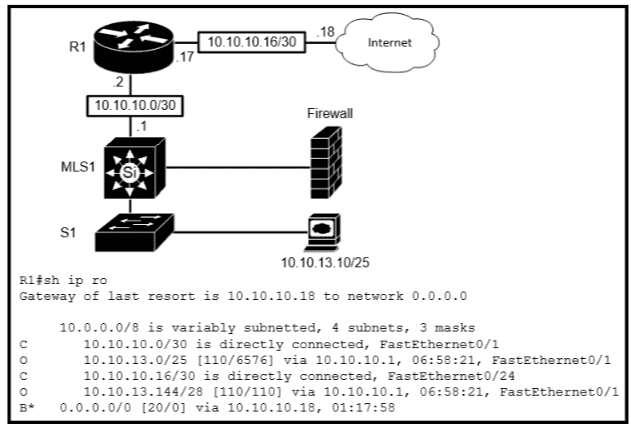
Which type of route does R1 use to reach host 10.10.13.10/32?
Which two actions are performed by the Weighted Random Early Detection mechanism? (Choose two)
Refer to the exhibit.
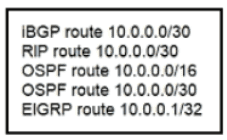
A router reserved these five routes from different routing information sources.
Which two routes does the router install in its routing table? (Choose two)
Refer to the exhibit.

What is the result if Gig1/11 receives an STP BPDU?
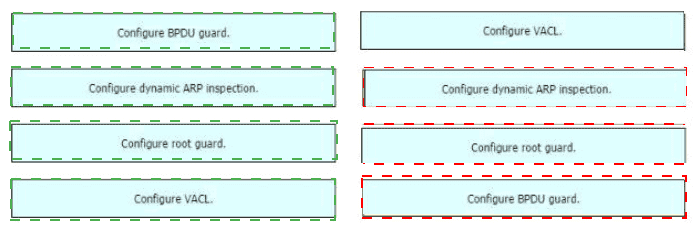
How are VLAN hopping attacks mitigated?
What is the purpose of traffic shaping?
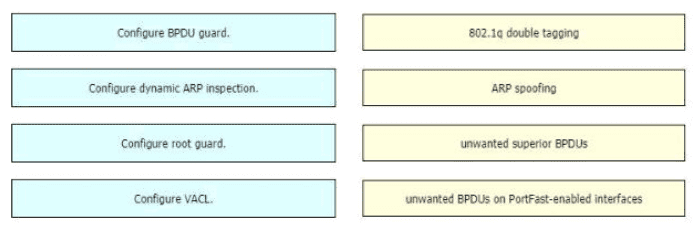
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
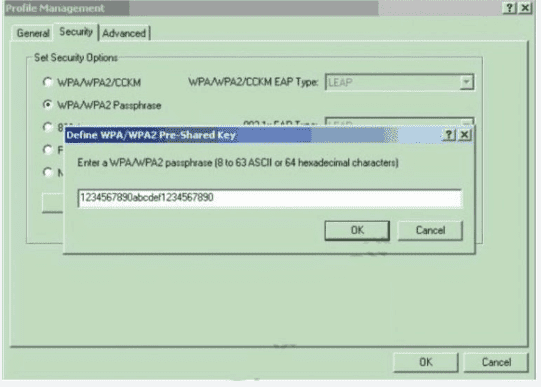
Which type of wireless encryption is used for WPA2 in preshared key mode?
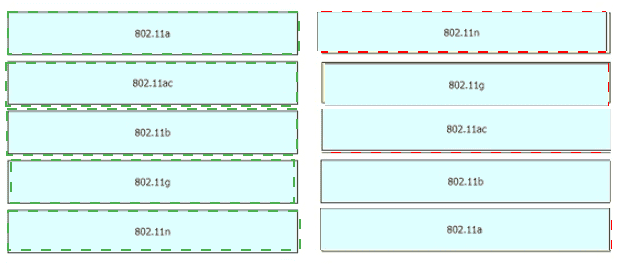
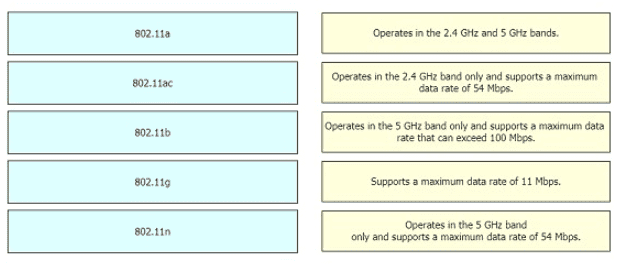
Drag and drop the 802.11 wireless standards from the left onto the matching statements on the right
What is the difference regarding reliability and communication type between TCP and UDP?
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two. )



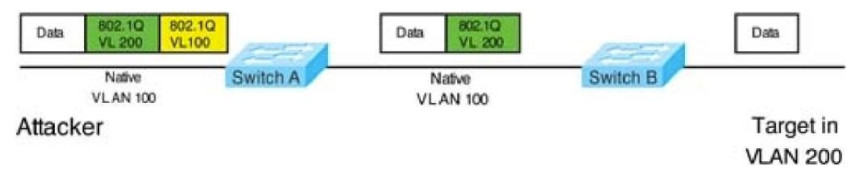 In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).