Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
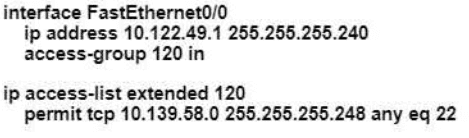
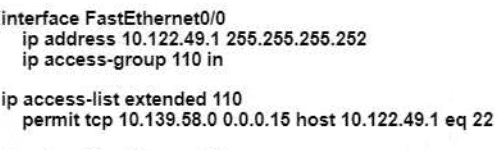
An engineer is configuring remote access to a router from IP subnet 10.139.58.0/28. The domain name, crypto keys, and SSH have been configured. Which configuration enables the traffic on the destination router?
A)
B)
C)
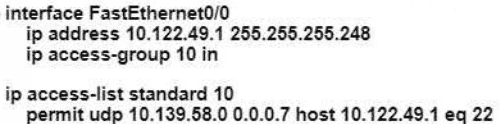
D)
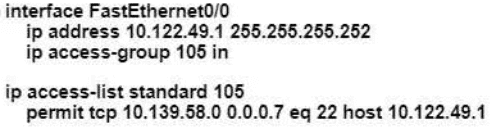
Refer to the exhibit.
All VLANs are present in the VLAN database. Which command sequence must be applied to complete the configuration?
Refer to the exhibit.
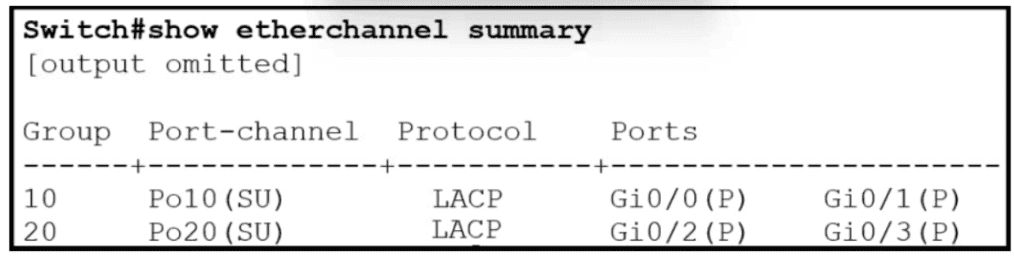
Which two commands when used together create port channel 10? (Choose two.)
Refer to the exhibit.
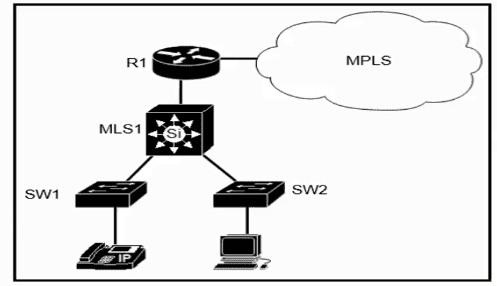
Which plan must be Implemented to ensure optimal QoS marking practices on this network?
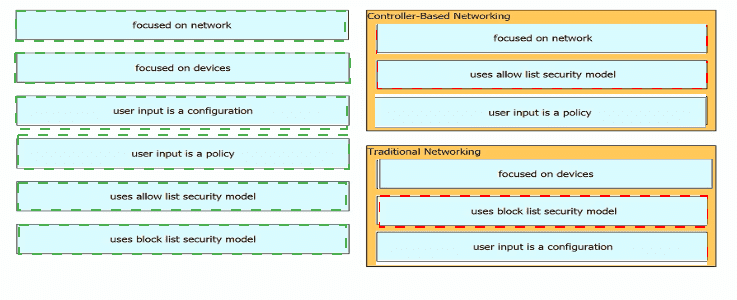
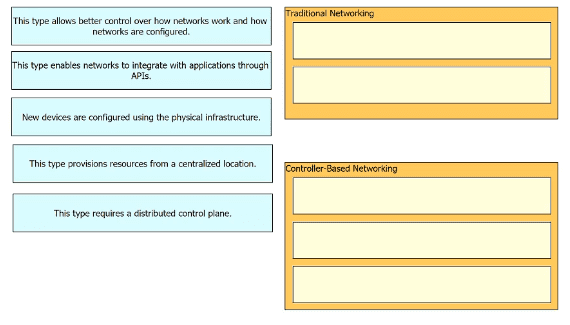
Drag and drop the characteristics of networking from the left onto the networking types on the right.
What is a function of an endpoint on a network?
Which two components comprise part of a PKI? (Choose two.)
Which action is taken by the data plane within a network device?
Refer to the exhibit.
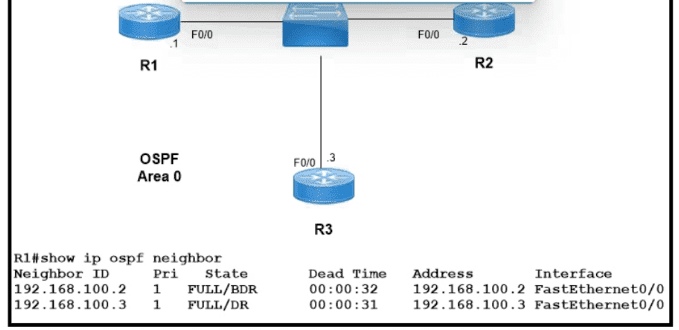
Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.)
A)

B)

C)

D)
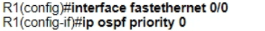
E)

Refer to the exhibit.
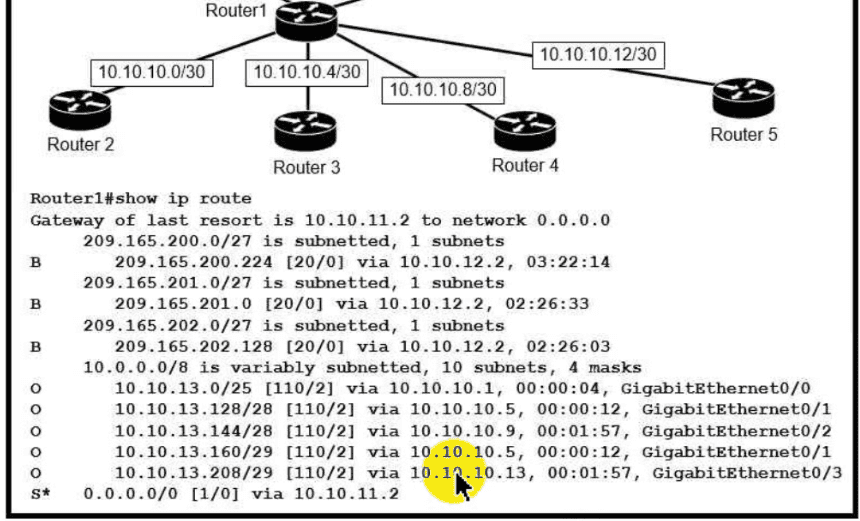
Which next-hop IP address does Routed use for packets destined to host 10 10.13.158?
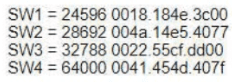
Refer to the exhibit.
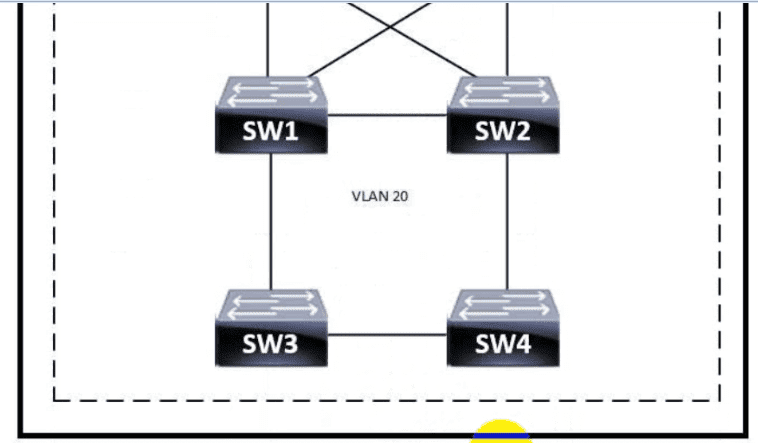
Which switch becomes the root of a spanning tree for VLAN 20 if all li links are of equal speed?
Refer to the exhibit.
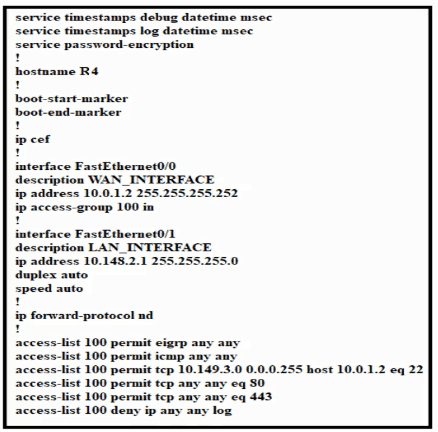
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
A Cisco engineer must configure a single switch interface to meet these requirements
• accept untagged frames and place them in VLAN 20
• accept tagged frames in VLAN 30 when CDP detects a Cisco IP phone
Which command set must the engineer apply?
A)

B)

C)

D)

What causes a port to be placed in the err-disabled state?
Which action implements physical access control as part of the security program of an organization?
Refer to the exhibit.
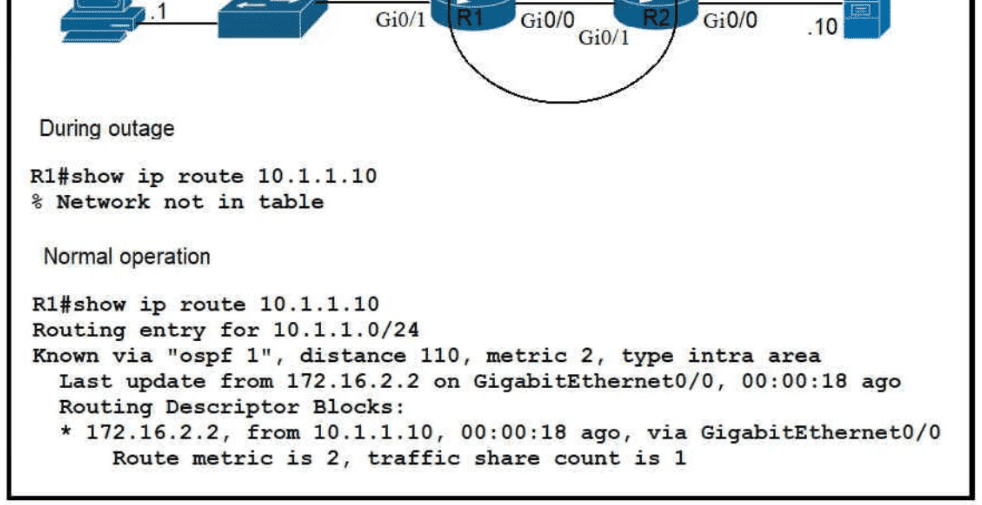
Which route must be configured on R1 so that OSPF routing is used when OSPF is up. but the server is still reachable when OSPF goes down?
Refer to the exhibit.
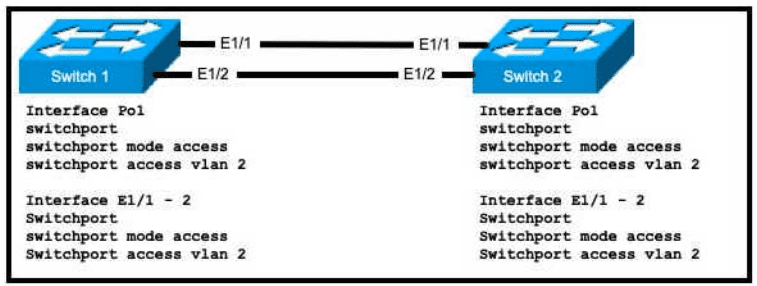
An engineer is configuring an EtherChannel using LACP between Switches 1 and 2 Which configuration must be applied so that only Switch 1 sends LACP initiation packets?
Refer to the exhibit.
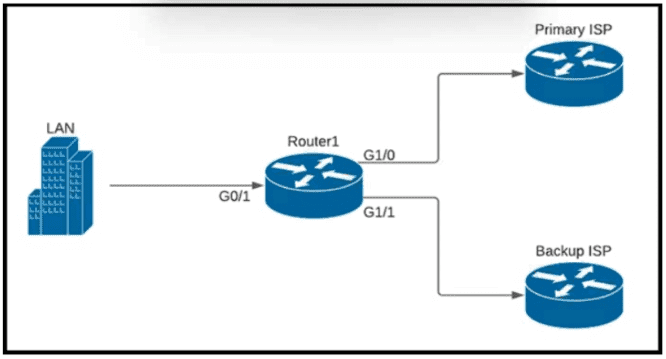
A company is configuring a failover plan and must implement the default routes in such a way that a floating static route will assume traffic forwarding when the primary link goes down. Which primary route configuration must be used?
Which WLC management connection type is vulnerable to man-in-the-middle attacks?
What is the function of the controller in a software-defined network?
A network engineer must configure two new subnets using the address block 10 70 128 0/19 to meet these requirements:
• The first subnet must support 24 hosts
• The second subnet must support 472 hosts
• Both subnets must use the longest subnet mask possible from the address block
Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two )
Which protocol uses the SSL?
Which QoS traffic handling technique retains excess packets in a queue and reschedules these packets for later transmission when the configured maximum bandwidth has been surpassed?
What are two benefits of FHRPs? (Choose two.)
Refer to the exhibit.
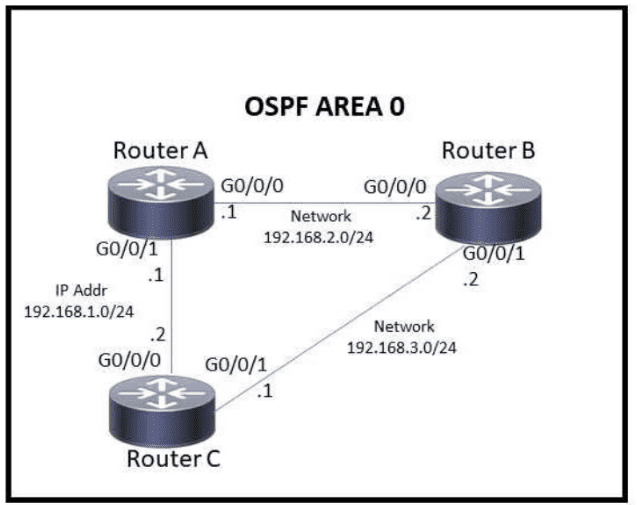
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Which two spanning-tree states are bypassed on an interface running PortFast? (Choose two.)
Refer to the exhibit.
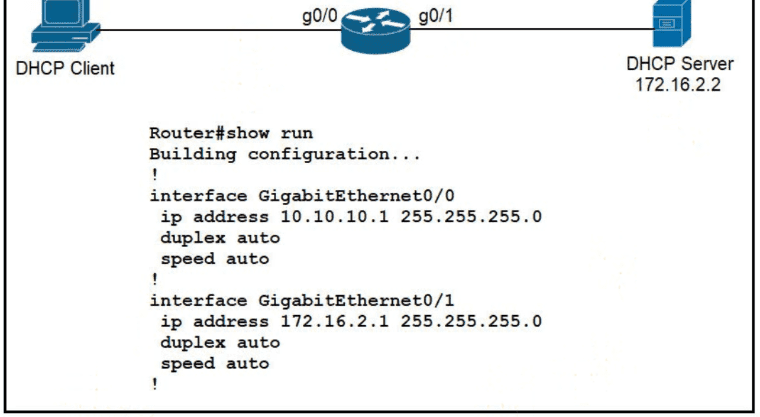
An engineer is configuring a new router on the network and applied this configuration. Which additional configuration allows the PC to obtain its IP address from a DHCP server?
What is an expected outcome when network management automation is deployed?
Refer to the exhibit.
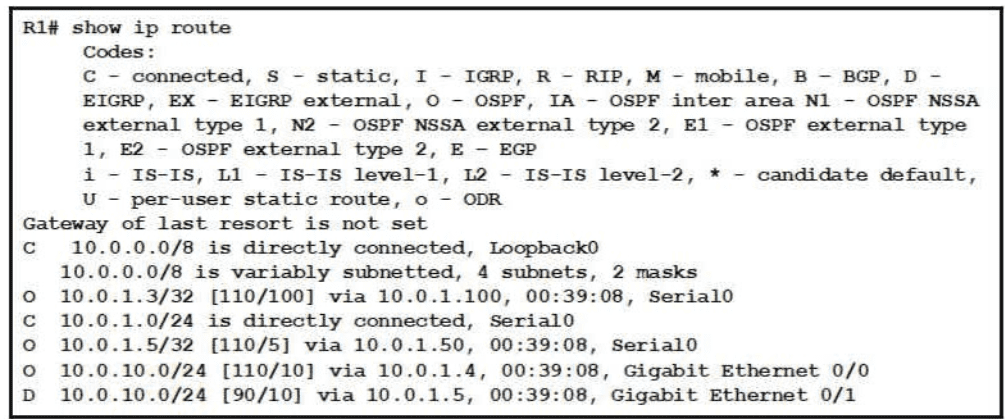
Web traffic is coming in from the WAN interface. Which route takes precedence when the router is processing traffic destined for the LAN network at 10 0.10.0/24?
Refer to the exhibit.
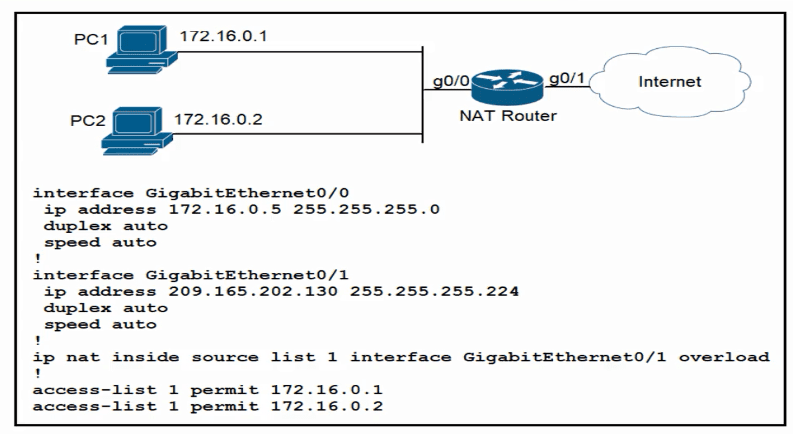
How should the configuration be updated to allow PC1 and PC2 access to the Internet?
Refer to the exhibit.
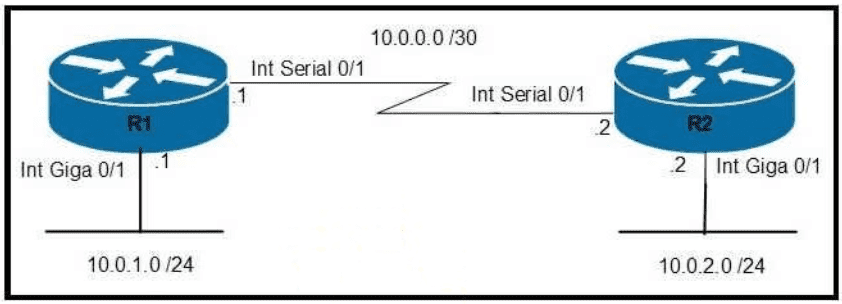
Which command configures OSPF on the point-to-point link between routers R1 and R2?
Which field within the access-request packet is encrypted by RADIUS?
A network engineer must implement an IPv6 configuration on the vlan 2000 interface to create a routable locally-unique unicast address that is blocked from being advertised to the internet. Which configuration must the engineer apply?
Refer to the exhibit.
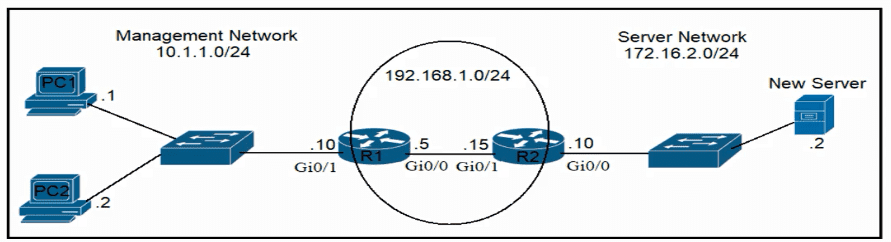
An engineer is updating the R1 configuration to connect a new server to the management network. The PCs on the management network must be blocked from pinging the default gateway of the new server. Which command must be configured on R1 to complete the task?
Refer to the exhibit.
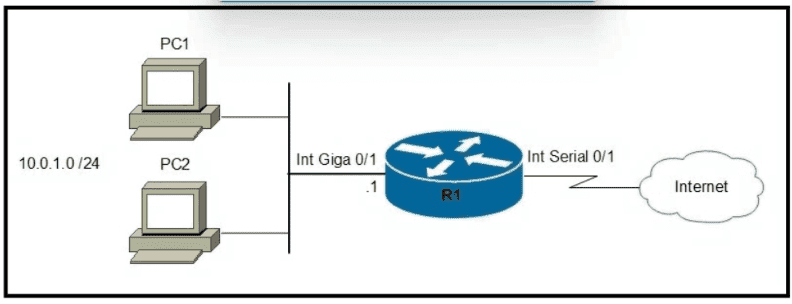
Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two)
Which protocol is used for secure remote CLI access?
Refer to the exhibit.
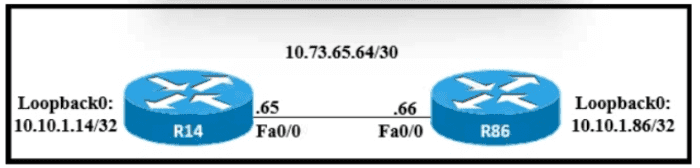
A static route must be configured on R14 to forward traffic for the 172 21 34 0/25 network that resides on R86 Which command must be used to fulfill the request?
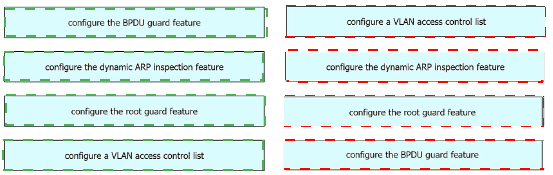
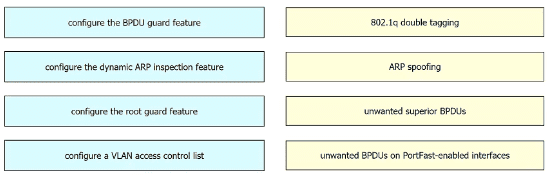
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
Refer to the exhibit.
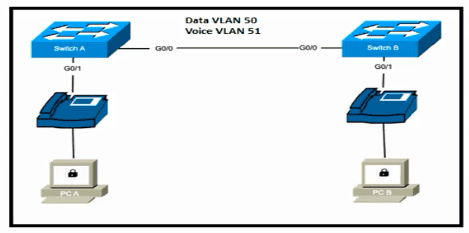
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)

B)

C)

D)

Which QoS per-hop behavior changes the value of the ToS field in the IPv4 packet header?
Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
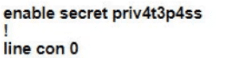
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
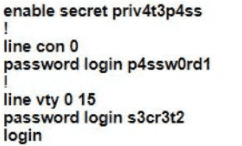
B)
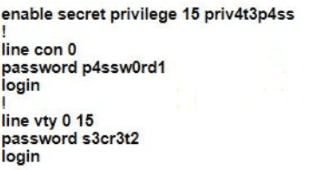
C)
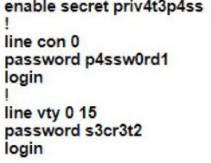
D)
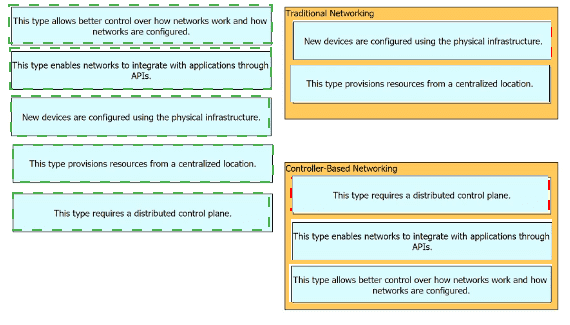
Drag and drop the statements about networking from the left onto the corresponding networking types on the right.
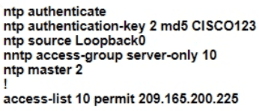
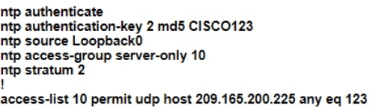
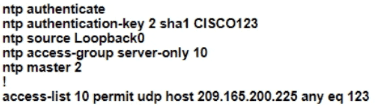
R1 as an NTP server must have:
• NTP authentication enabled
• NTP packets sourced from Interface loopback 0
• NTP stratum 2
• NTP packets only permitted to client IP 209.165 200 225
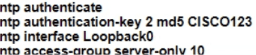
How should R1 be configured?
A)
B)
C)
D)
Refer to the exhibit.
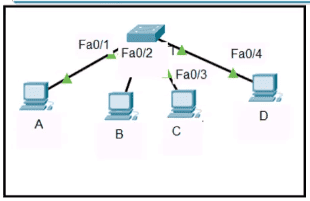
Host A sent a data frame destined for host D
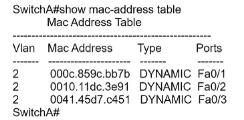
What does the switch do when it receives the frame from host A?
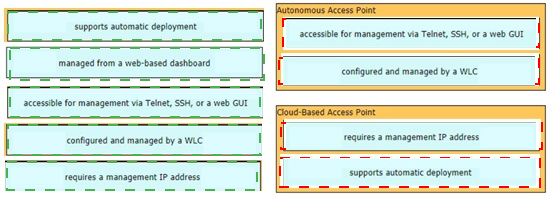
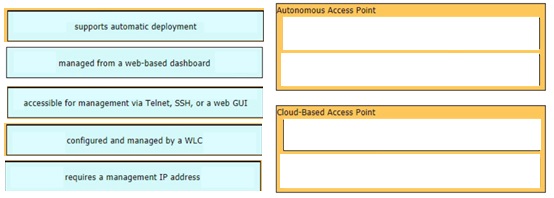
Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used.
Refer to the exhibit.
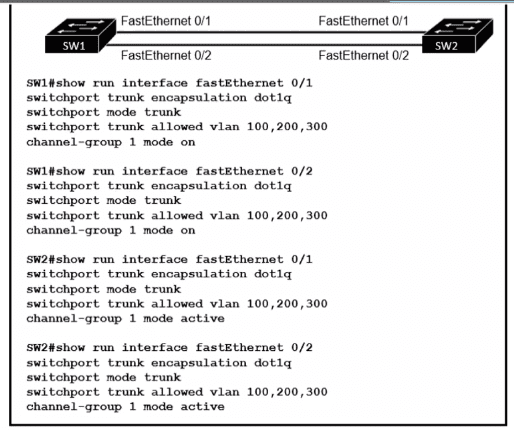
An engineer built a new L2 LACP EtherChannel between SW1 and SW2 and executed these show commands to verify the work. Which additional task allows the two switches to establish an LACP port channel?
Refer to the exhibit.
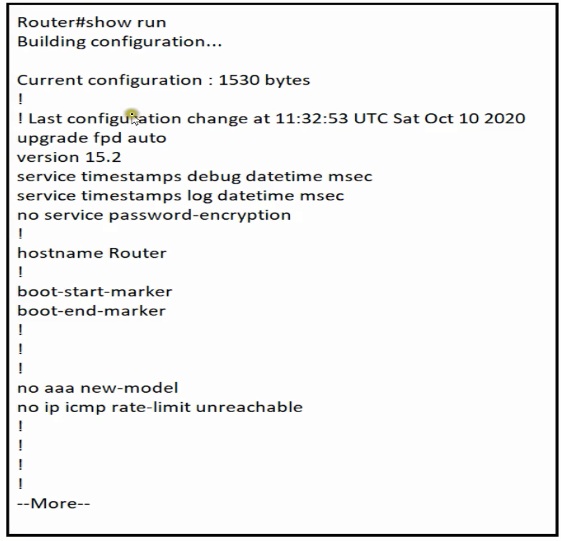
Which minimum configuration items are needed to enable Secure Shell version 2 access to R15?
A)

B)
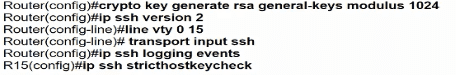
C)

D)

Which two practices are recommended for an acceptable security posture in a network? (Choose two)
Refer to the exhibit.
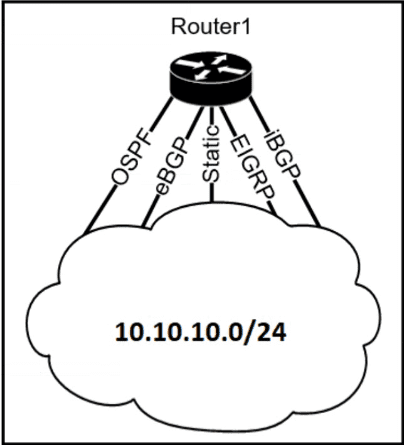
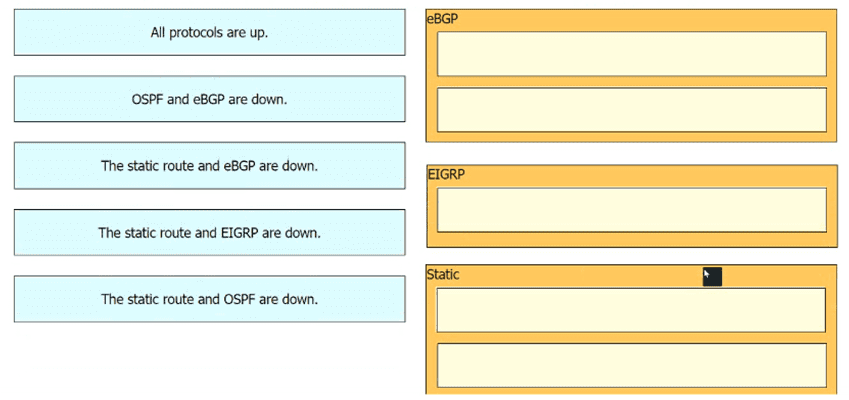
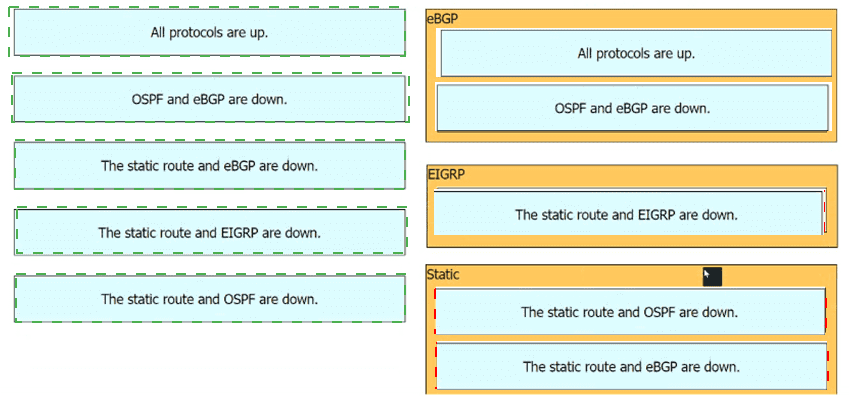
The Router1 routing table has multiple methods to reach 10.10.10.0/24 as shown. The default Administrative Distance is used. Drag and drop the network conditions from the left onto the routing methods that Router1 uses on the right.