Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Which type of IPv6 address is publicly routable in the same way as IPv4 public address?
Refer to the exhibit.
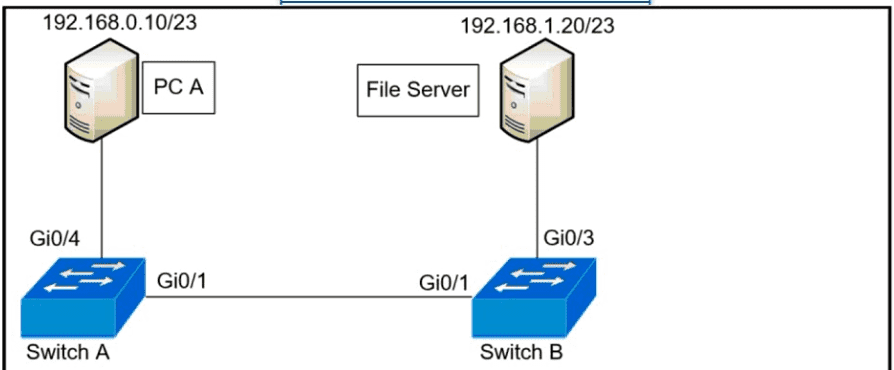
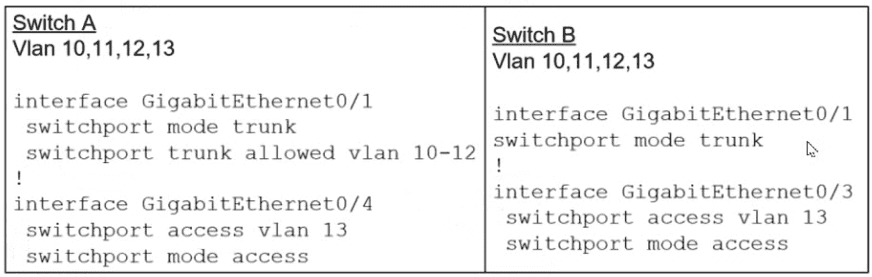
A network administrator assumes a task to complete the connectivity between PC A and the File Server. Switch A and Switch B have been partially configured with VLAN 10, 11, 12, and 13. What is the next step in the configuration?
Which statement describes virtual machines?
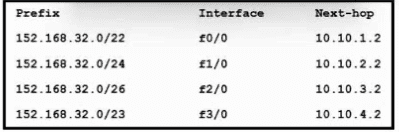
Refer to the exhibit. Which next hop is used to route packets to the application server at 152.168.32.85?
Refer to the exhibit.

The LACP EtherChannel is configured, and the last change is to modify the interfaces on SwitchA to respond to packets received, but not to initiate negotiation. The interface range gigabitethernet0/0-15 command is entered. What must be configured next?
How does a network administrator securely manage an AP in lightweight mode?
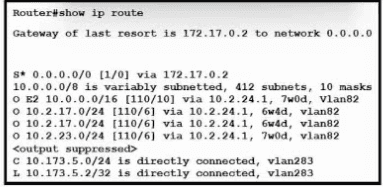
Refer to the exhibit. What is the value of the administrative distance for the default gateway?
What are two differences between optical-fiber cabling and copper cabling? (Choose two)
The SW1 interface g0/1 is in the down/down state. Which two configurations are valid reasons for the interface conditions?(choose two)
Which function does an SNMP agent perform?
What are two characteristics of a public cloud Implementation? (Choose two.)
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
Which plane is centralized by an SDN controller?
Which action does the router take as rt forwards a packet through the network?
Which technology must be implemented to configure network device monitoring with the highest security?
An organization secures its network with multi-factor authentication using an authenticator app on employee smartphone. How is the application secured in the case of a user’s smartphone being lost or stolen?
An office has 8 floors with approximately 30-40 users per floor What command must be configured on the router Switched Virtual Interface to use address space efficiently?
Where does wireless authentication happen?
What are two characteristics of a controller-based network? (Choose two)
What is the benefit of configuring PortFast on an interface?
Which QoS tool is used to optimize voice traffic on a network that is primarily intended for data traffic?
Refer to the exhibit.
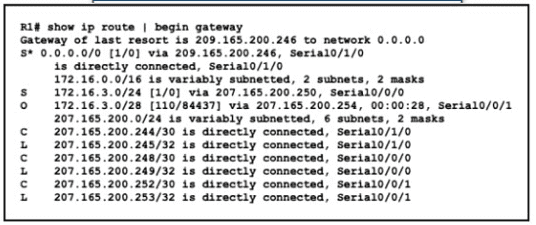
A packet is being sent across router R1 to host 172.163.3.14. To which destination does the router send the packet?
What is a function of TFTP in network operations?
Refer to the exhibit.
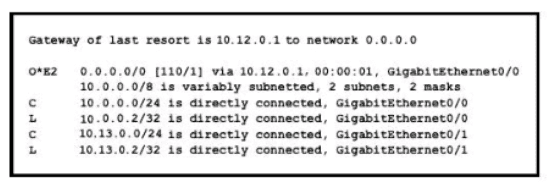
If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command how does the router respond?
An engineer must configure an OSPF neighbor relationship between router R1 and R3 The authentication configuration has been configured and the connecting interfaces are in the same 192.168 1.0/30 sublet. What are the next two steps to complete the configuration? (Choose two.)
Refer to the exhibit.
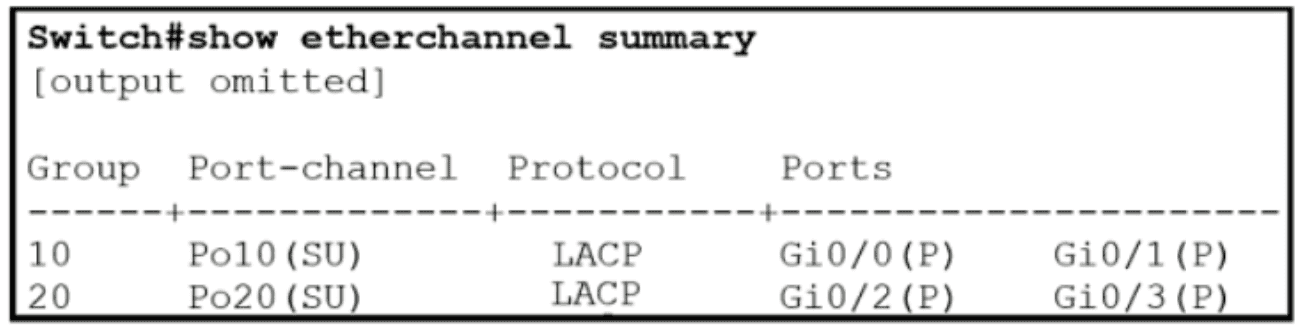
Which two commands were used to create port channel 10? (Choose two )

Where does a switch maintain DHCP snooping information?
Which result occurs when PortFast is enabled on an interface that is connected to another switch?
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
A network administrator needs to aggregate 4 ports into a single logical link which must negotiate layer 2 connectivity to ports on another switch. What must be configured when using active mode on both sides of the connection?
A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
Refer to the exhibit.
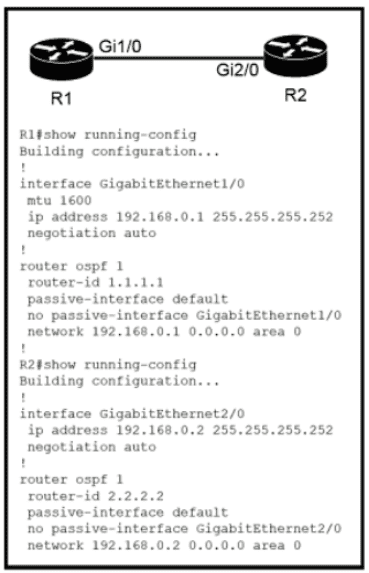
Which configuration issue is preventing the OSPF neighbor relationship from being established between the two routers?
Refer to the exhibit.
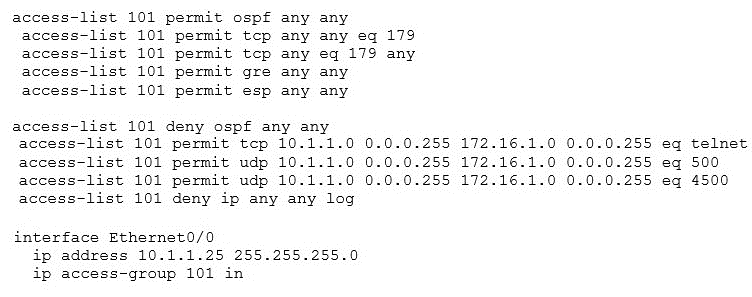
A network administrator has been tasked with securing VTY access to a router. Which access-list entry accomplishes this task?
Which configuration is needed to generate an RSA key for SSH on a router?
Refer to the exhibit.
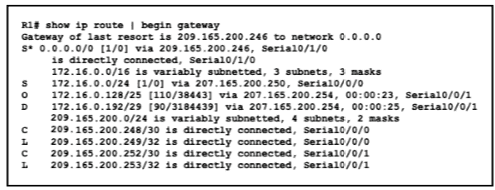
With which metric was the route to host 172.16.0.202 learned?
When OSPF learns multiple paths to a network, how does it select a route?
What is a capability of FTP in network management operations?
Which port type supports the spanning-tree portfast command without additional configuration?
Refer to the exhibit.
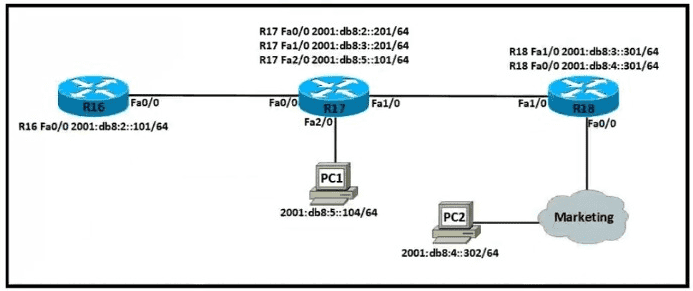
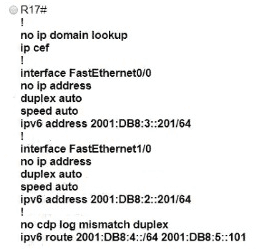
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A)
B)
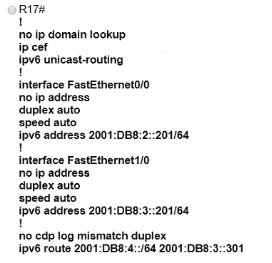
C)
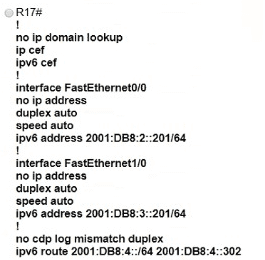
D)
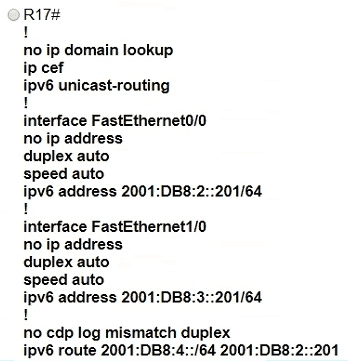
An engineer configured an OSPF neighbor as a designated router. Which state verifies the designated router is in the proper mode?
What is the same for both copper and fiber interfaces when using SFP modules?
Refer to the exhibit.

What is the effect of this configuration?
Drag and drop the Rapid PVST+ forwarding slate actions from the loft to the right. Not all actions are used.
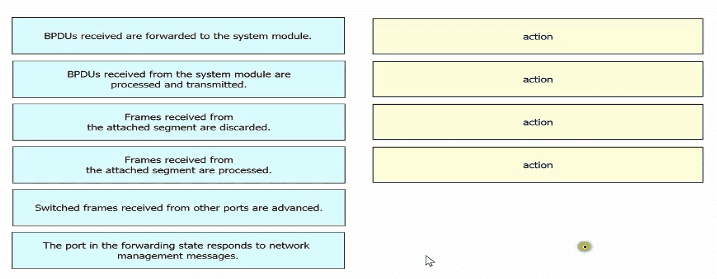
Refer to the exhibit.
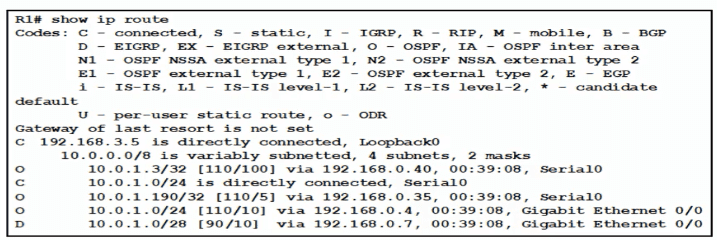
Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
What is the difference between IPv6 unicast and anycast addressing?
Refer to the exhibit.
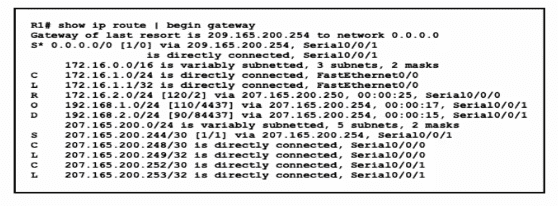
Which network prefix was learned via EIGRP?
What is a requirement when configuring or removing LAG on a WLC?
Which characteristic differentiates the concept of authentication from authorization and accounting?
An engineer requires a scratch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
OSPF must be configured between routers R1 and R2. Which OSPF configuration must be applied to router R1 to avoid a DR/BDR election?




