Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Which AP mode wirelessly connects two separate network segments each set up within a different campus building?
How does MAC learning function?
Which QoS feature drops traffic that exceeds the committed access rate?
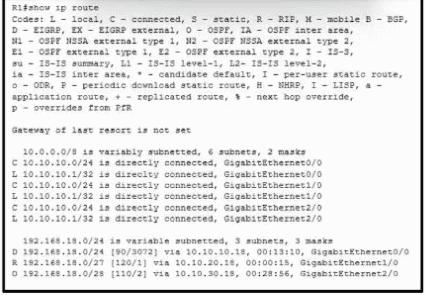
Refer to the exhibit. Which interface does a packet take to reach the host address of 192.168.18.16?
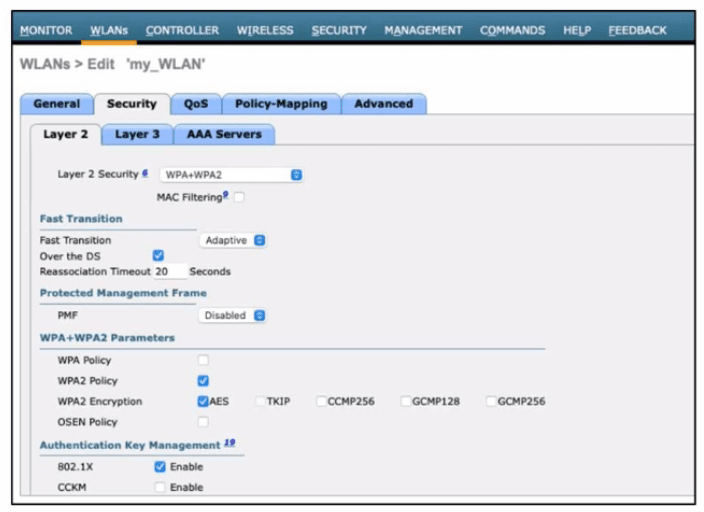
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
Which switch port configuration must be configured when connected to an AP running in FlexConnect mode, and the WLANs use flex local switching?
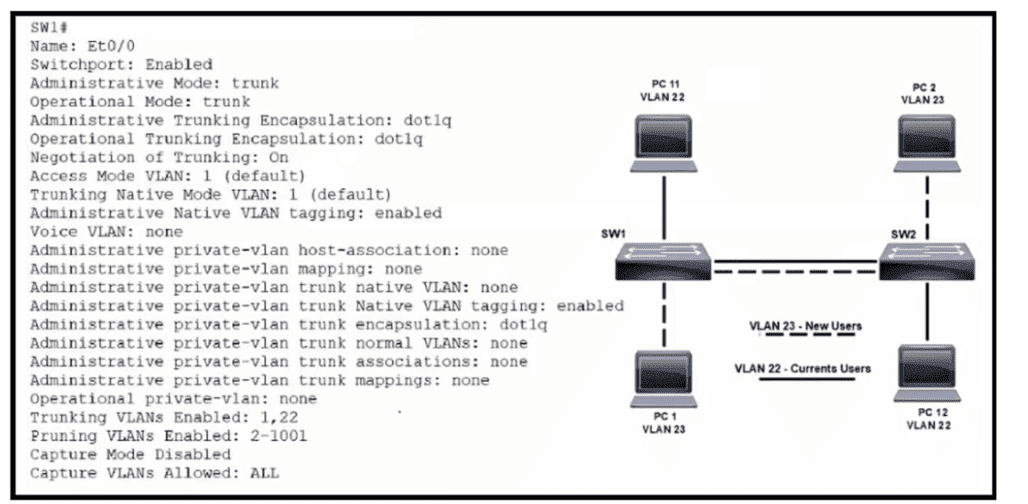
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
How does MAC learning function?
Refer to the exhibit.
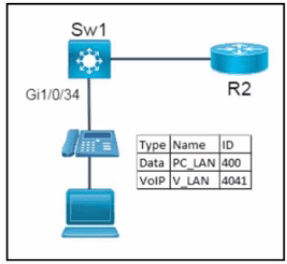
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
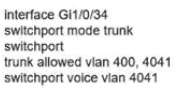
B)
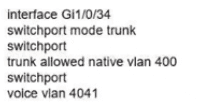
C)
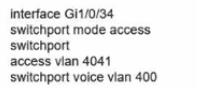
D)
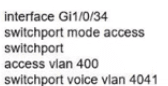
Which two QoS tools provide congestion management? (Choose two.)
What differentiates the TCP and UDP protocols?
What is the function of generative AI in network operations?
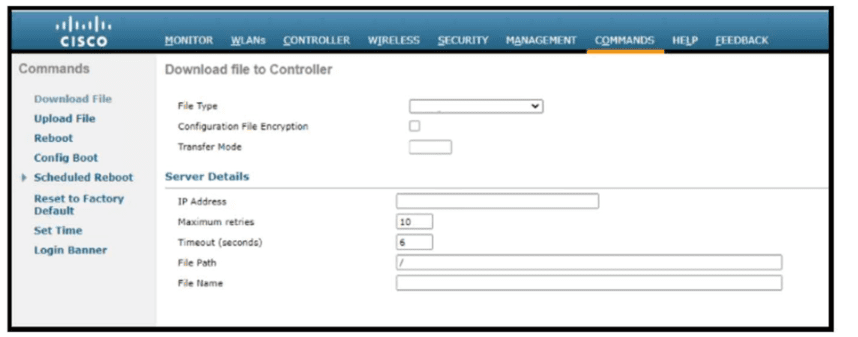
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
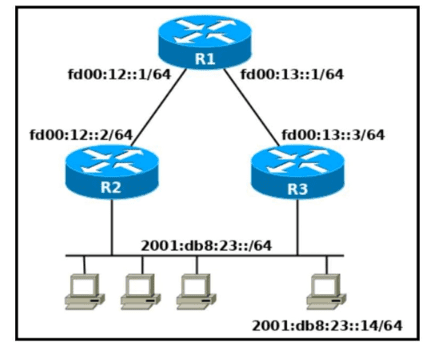
Refer to the exhibit. Which two commands, when configured on router R1. fulfill these requirements? (Choose two.) ' Packets toward the entire network 2001:db8:23: :/64 must be forwarded through router R2. ' Packets toward host 2001: db8:23::14 preferably must be forwarded through R3.
Refer to the exhibit.
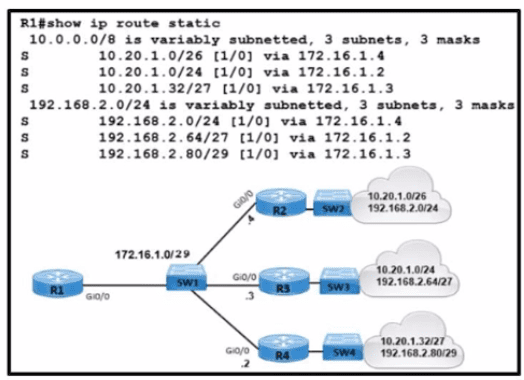
What is the correct next hop for router R1 to reach IP addresses 192.168.2.86 and 10.20.1.50?
Why does an administrator choose to implement a remote access IPsec VPN?
What is the main purpose of SSH management access?
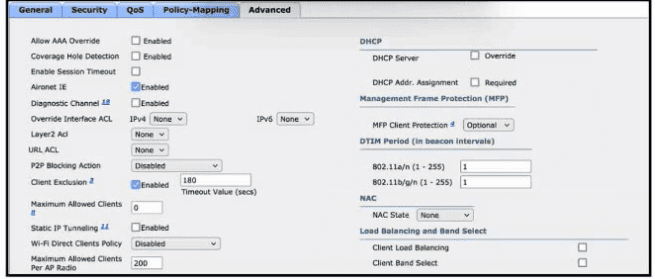
Refer to the exhibit. After a recent internal security audit, the network administrator decided to block all P2P-capable devices from the selected SSID. Which configuration setting must the administrator apply?
Which statement describes virtualization on containers?
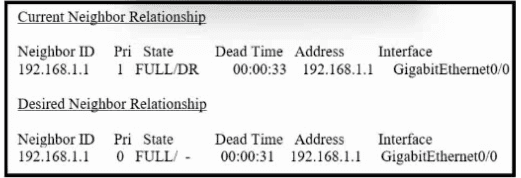
Refer to the exhibit. How must OSPF be configured on the GigabitEthernet0/0 interface of the neighbor device to achieve the desired neighbor relationship?
Which technology allows for logical Layer 3 separation on physical network equipment?
What are two behaviors of a point-to-point WAN topology? (Choose two.)
Which role do predictive Al models play in network load balancing?
A network security team noticed that an increasing number of employees are becoming victims of phishing attacks. Which security program should be implemented to mitigate the problem?
What is a characteristic of an SSID in wireless networks?
Which security element uses a combination of one-time passwords, a login name, and a personal smartphone?
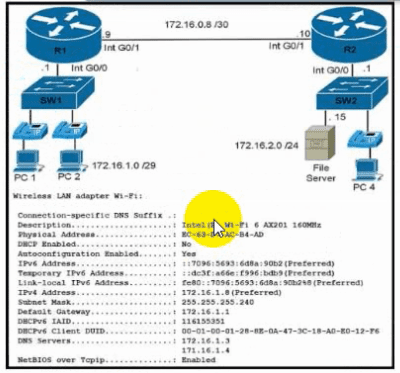
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?
Which two features are provided by Ansible in network automation? (Choose two.)
What is the purpose of the service-set identifier?
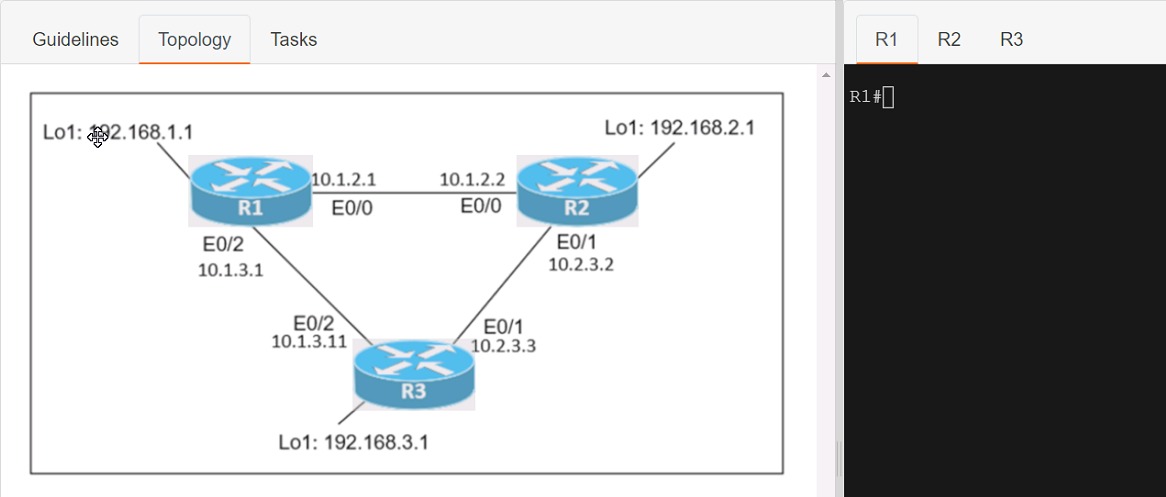
Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
What is an advantage of using SDN versus traditional networking when it comes to security?
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
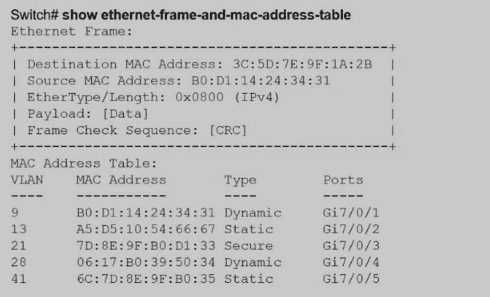
How does the switch handle the frame?
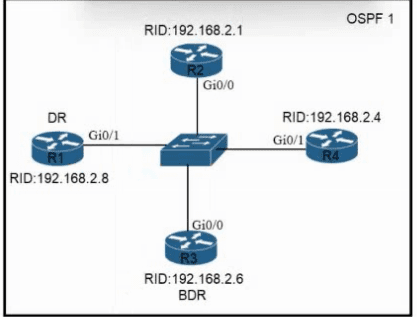
Refer to the exhibit. All routers In the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?

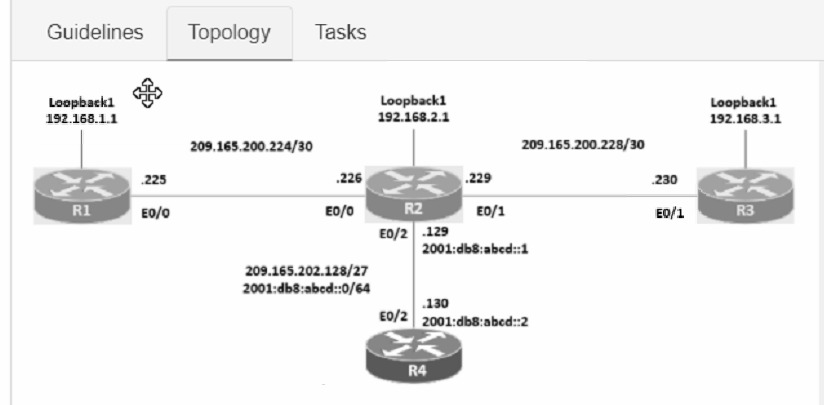
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
Which combination of methods satisfies the minimum security requirements when a new multifactor authentication solution is deployed?
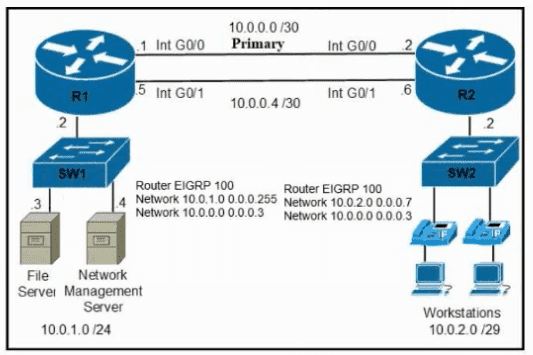
Refer to the exhibit. A secondary route is required on router R1 to pass traffic to the LAN network on R2 if the primary link fails. Which command must be entered to configure the router?
Which feature Is mandatory when configuring a new SSID for a wireless network running WPA3-Personal mode?
What is a characteristic of private IPv4 addressing?
What is a similarity between global and unique local IPv6 addresses?
Which role does AI play in monitoring network data flow?
Which two northbound APIs are found in a software-defined network? (Choose two.)
How does MAC learning function?
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
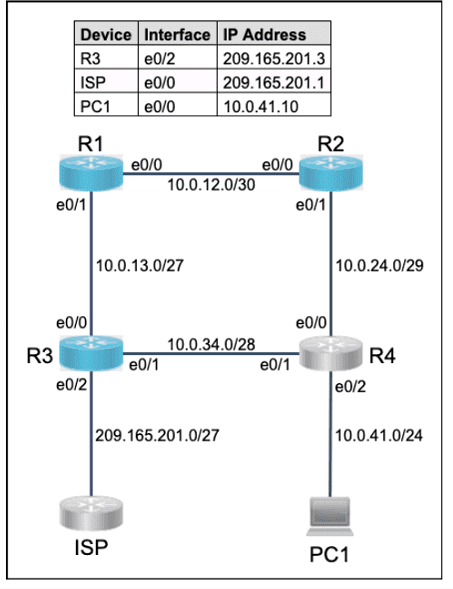
What is a characteristic of encryption in wireless networks?
Why would a network administrator choose to implement RFC 1918 address space?
Which type of protocol is VRRP?
Refer to the exhibit.
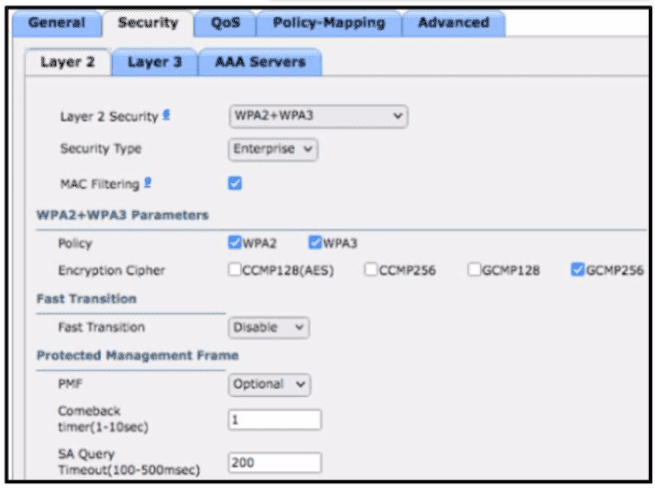
An engineer must document all Wi-Fi services on a new wireless LAN controller. The Wi-Fi SSID "Office_WLan" has Layer 2 Security. What is determined by this configuration?
What is the main capability of multifactor authentication?
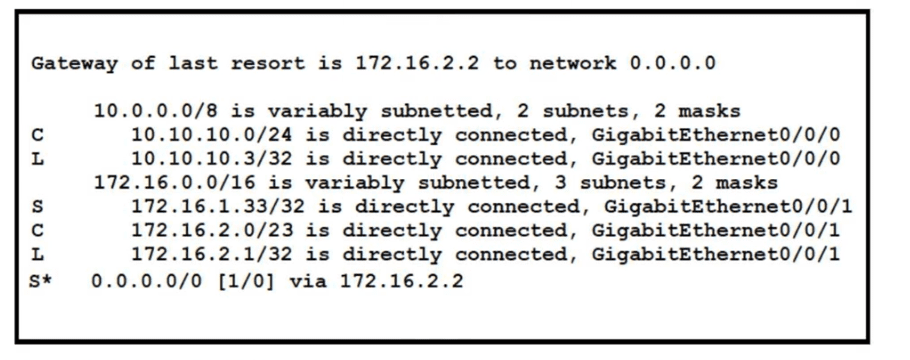
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
Refer to the exhibit.

Which two prefixes are included in this routing table entry? (Choose two.)



