Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
What is used to identify spurious DHCP servers?
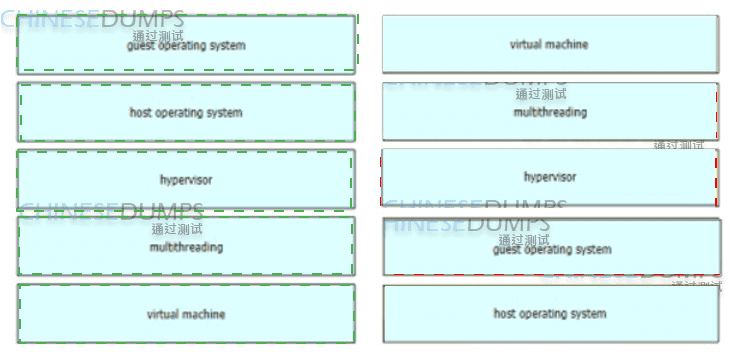
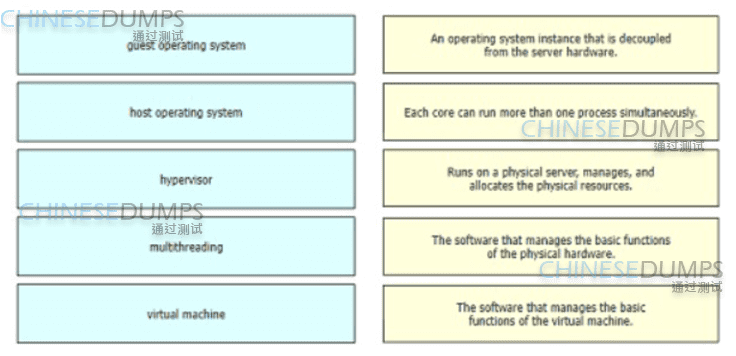
Drag and drop the virtualization concepts from the left onto the matching statements on the right.
Which command do you enter so that a switch configured with Rapid PVST + listens and learns for a specific time period?
What are two features of the DHCP relay agent? (Choose two.)
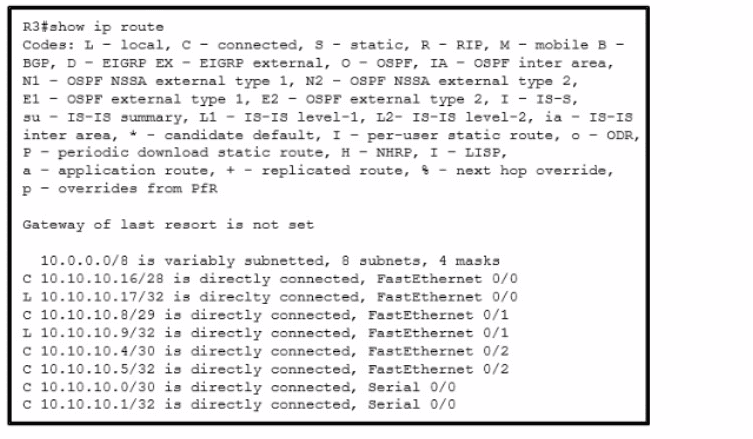
Refer to the exhibit. Which interface does a packet take to reach the destination address of 10.10.10.147?
In which circumstance would a network architect decide to implement a global unicast subnet instead of a unique local unicast subnet?
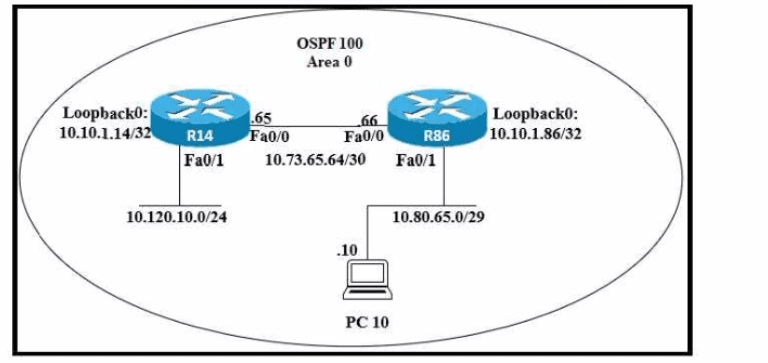
Refer to the exhibit. An engineer just installed network 10.120.10.0/24. Which configuration must be applied to the R14 router to add the new network to its OSPF routing table?
Refer to the exhibit.
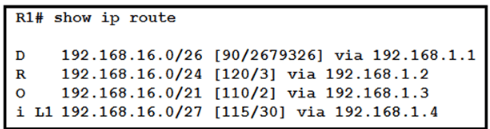
Which route does R1 select for traffic that is destined to 192.168.16.2?
Refer to the exhibit.
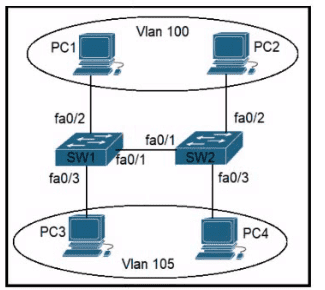
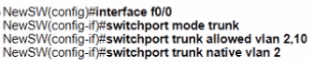
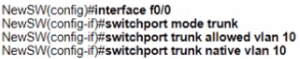
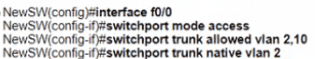
An engineer configures interface fa0/1 on SW1 and SW2 to pass traffic from two different VLANs. For security reasons, company policy requires the native VLAN to be set to a nondefault value. Which configuration meets this requirement?
A)

B)

C)

D)

A)
B)
C)
D)
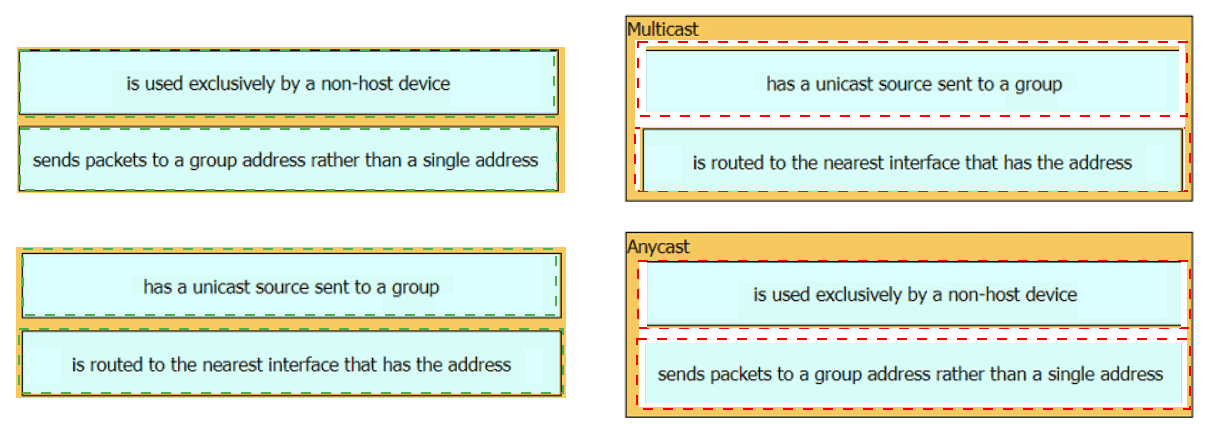
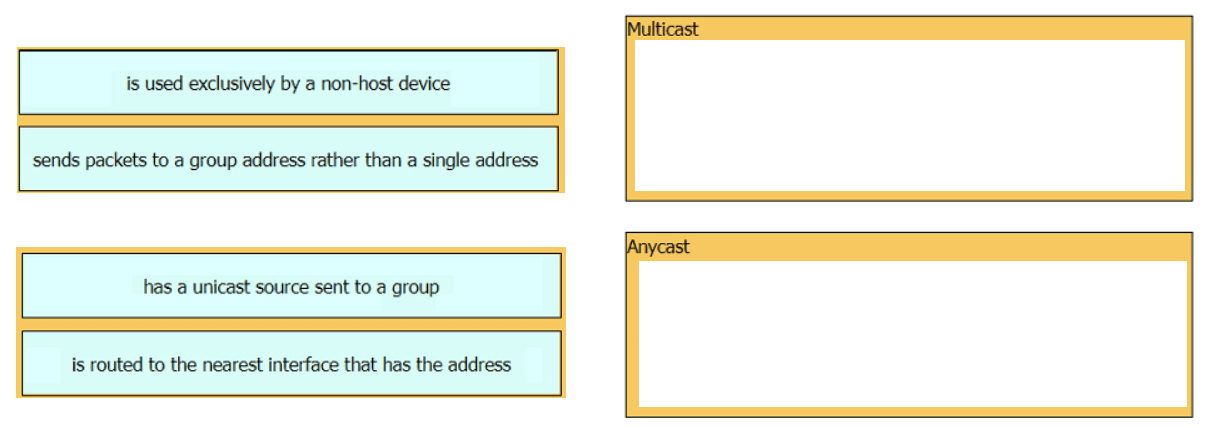
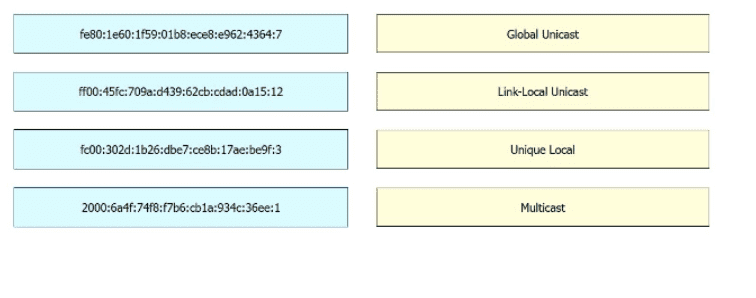
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Why is TCP desired over UDP for application that require extensive error checking, such as HTTPS?
What is a feature of WPA?
Refer to the exhibit.
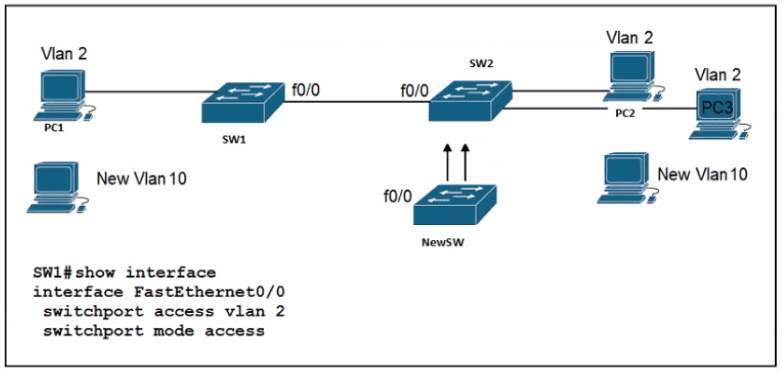
An engineer is configuring a new Cisco switch NewSW, to replace SW2 The details have been provided
• Switches SW1 and SW2 are third-party devices without support for trunk ports
• The existing connections must be maintained between PC1 PC2 and PC3
• Allow the switch to pass traffic from future VLAN 10. Which configuration must be applied?
A)
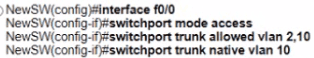
B)
C)
D)
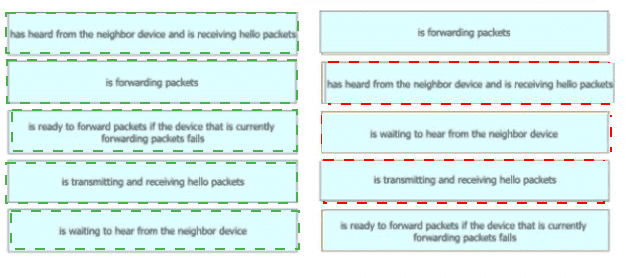
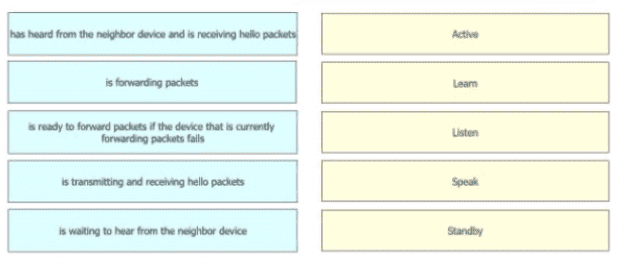
Drag and drop the device behaviors from the left onto the matching HSRP slate on the right.
Refer to the exhibit.
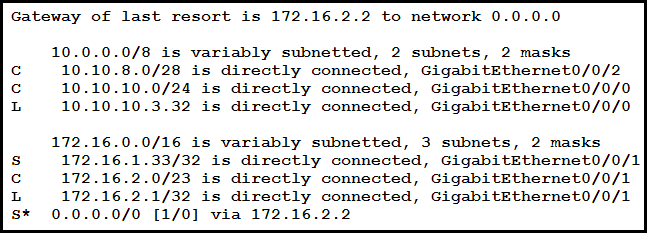
A packet sourced from 10.10.10.1 is destined for 10.10.8.14. What is the subnet mask of the destination route?
Which EtherChannel mode must be configured when using LAG on a WLC?
Which command creates a static NAT binding for a PC address of 10.1.1.1 to the public routable address 209.165.200.225 assigned to the PC?
What are two disadvantages of a full-mesh topology? (Choose two.)
An engineer must configure a core router with a floating static default route to the backup router at 10.200.0.2. Which command meets the requirements?
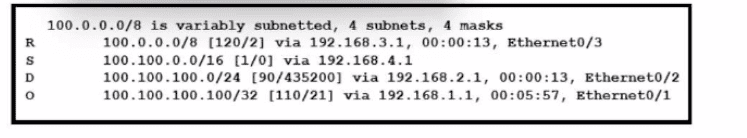
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
Which part of the HTTP request is used in REST API basic authentication to carry credentials?
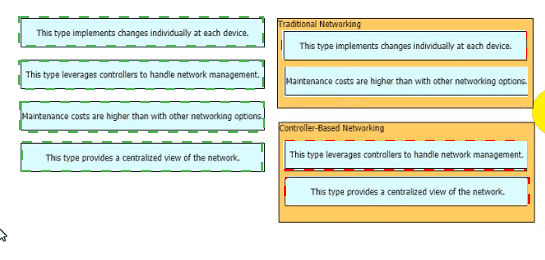
Drag and drop the statements about networking from the left onto the corresponding networking types on the right
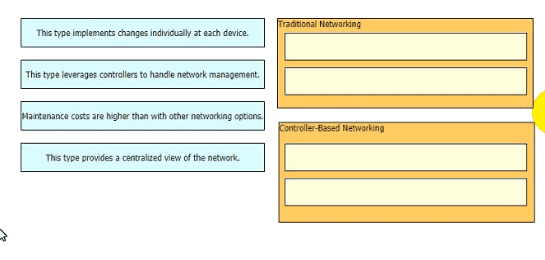
Refer to the exhibit.
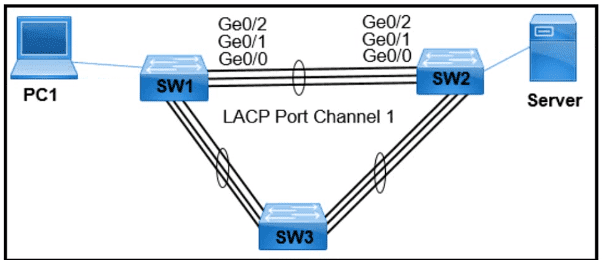
PC1 regularly sends 1800 Mbps of traffic to the server. A network engineer needs to configure the EtherChannel to disable Port Channel 1 between SW1 and SW2 when the Ge0/0 and Ge0/1 ports on SW2 go down. Which configuration must the engineer apply to the switch?
A)

B)

C)

D)

Two switches have been implemented and all interfaces are at the default configuration level. A trunk link must be implemented between two switches with these requirements:
• using an industry-standard trunking protocol
• permitting VLANs 1 -10 and denying other VLANs
How must the interconnecting ports be configured?
A)

B)

C)

D)

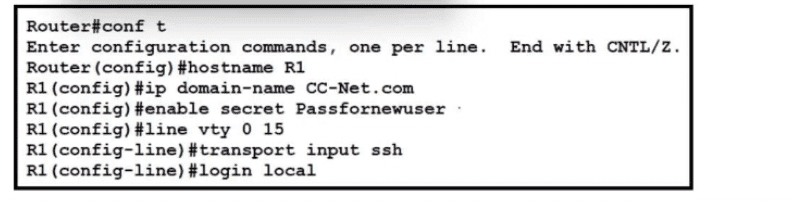
Refer to the exhibit. A network administrator is configuring a router for user access via SSH. The service-password encryption command has been issued. The configuration must meet these requirements:
• Create the username as CCUser.
• Create the password as NA!2Scc.
• Encrypt the user password.
What must be configured to meet the requirements?
Refer to the exhibit.

Host A switch interface is configured in VLAN 2. Host D sends a unicast packet destined for the IP address of host A.
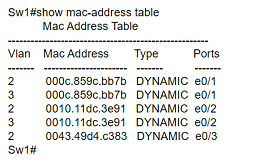
What does the switch do when it receives the frame from host D?
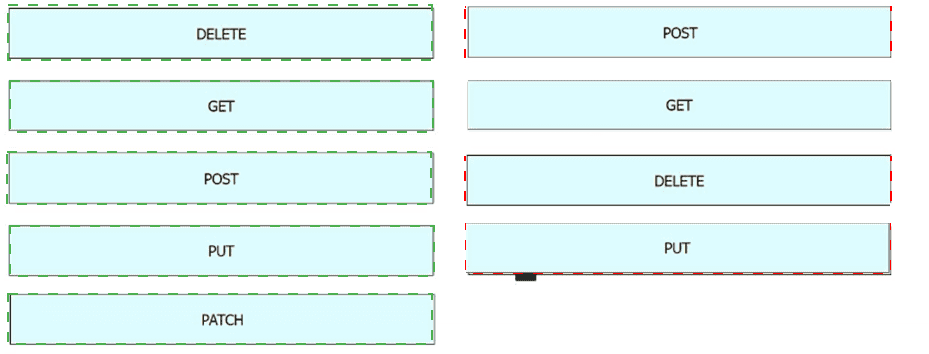
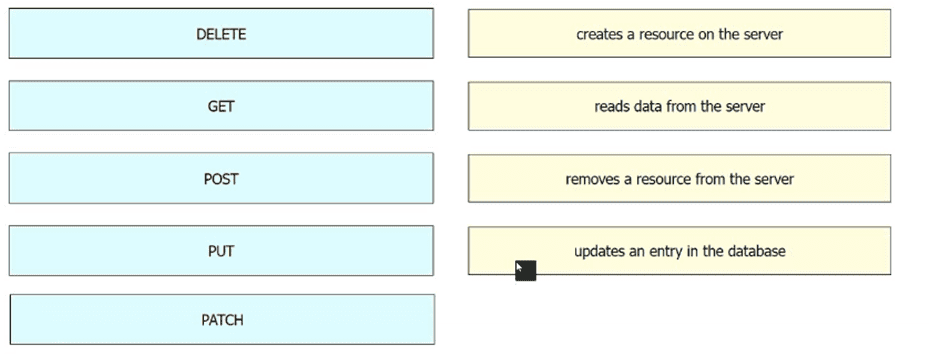
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.
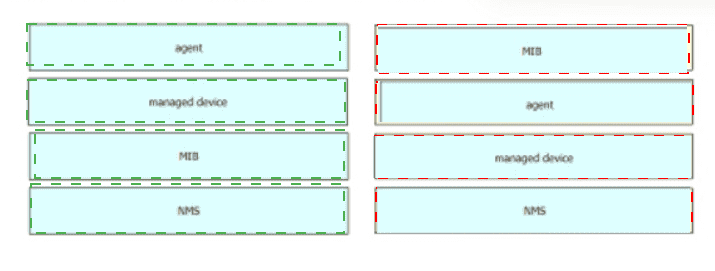
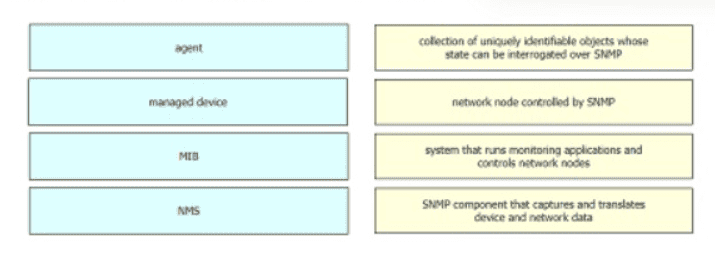
Drag and drop the SNMP components from the left onto the description on the right.
Which mechanism carries multicast traffic between remote sites and supports encryption?
Which (unction generally performed by a traditional network device is replaced by a software-defined controller?
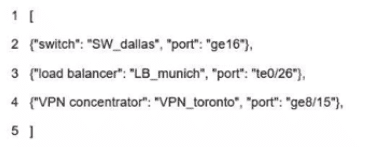
What is represented in line 3 within this JSON schema?
How does automation leverage data models to reduce the operational complexity of a managed network?
Why are API keys used to enforce rate limiting?
Refer to the exhibit.

A network engineer is configuring a WLAN to connect with the 172.16.10.0/24 network on VLAN 20. The engineer wants to limit the number of devices that connect to the WLAN on the USERWL SSID to 125. Which configuration must the engineer perform on the WLC?
Which header must be included in a REST request from an application that requires JSON-formatted content?
What is the difference between the TCP and UDP protocols?
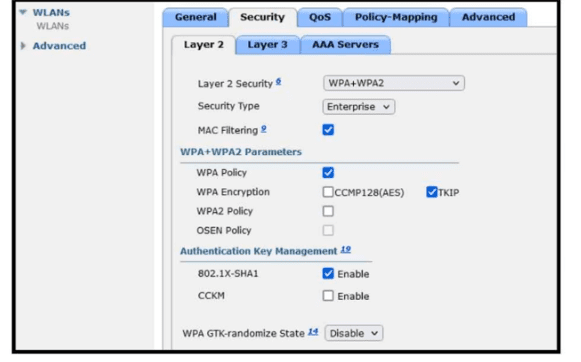
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
What is a characteristic of private IPv4 addressing?
Which interface is used to send traffic to the destination network?
10.174.208.210/28 [110/2708] via G0/21
10.174.208.210/28 [110/25445] via G0/20
10.174.208.210/28 [120/1] via G0/12
10.174.208.210/28 [120/4] via G0/16
What is the maximum length of characters used in an SSID?
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
How does automation affect network management processes?
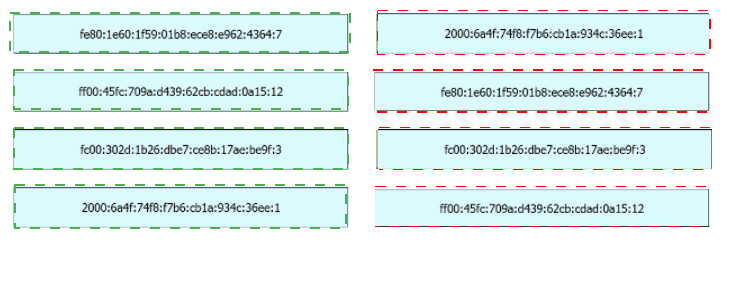
Drag and drop the IPv6 address from the left onto the type on the right.
Configure IPv4 and IPv6 connectivity between two routers. For IPv4, use a /28 network from the 192.168.1.0/24 private range. For IPv6, use the first /64 subnet from the 2001:0db8:aaaa::/48 subnet.
1. Using Ethernet0/1 on routers R1 and R2, configure the next usable/28 from the 192.168.1.0/24 range. The network 192.168.1.0/28 is unavailable.
2. For the IPv4 /28 subnet, router R1 must be configured with the first usable host address.
3. For the IPv4 /28 subnet, router R2 must be configured with the last usable host address.
4. For the IPv6 /64 subnet, configure the routers with the IP addressing provided from the topology.
5. A ping must work between the routers on the IPv4 and IPv6 address ranges.

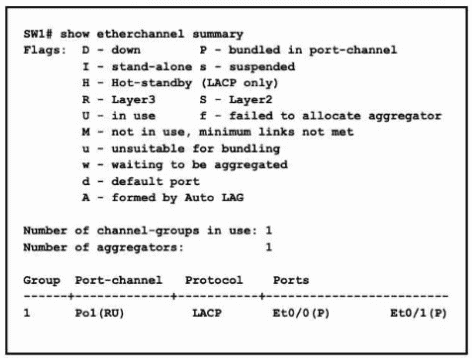
Refer to the exhibit. A network engineer is adding another physical interface as a new member to the existing Port-Channel1 bundle.
Which command set must be configured on the new interface to complete the process?
How is Al used to identify issues within network traffic?
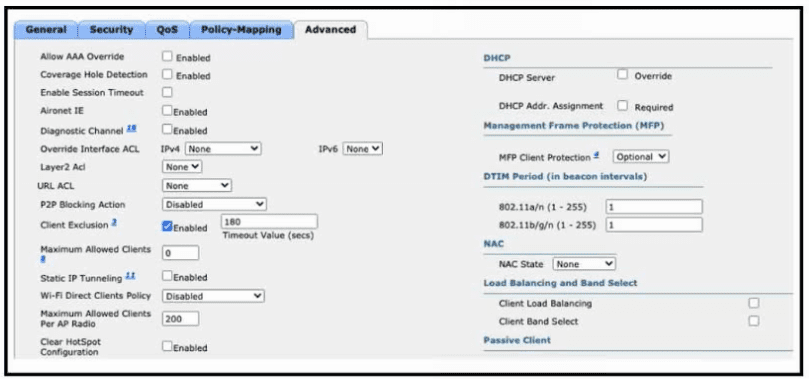
Refer to the exhibit. An administrator is configuring a new WLAN for a wireless network that has these requirements:
Dual-band clients that connect to the WLAN must be directed to the 5-GHz spectrum.
Wireless clients on this WLAN must be able to apply VLAN settings from RADIUS attributes.
Which two actions meet these requirements? (Choose two.)
Which two principles must be considered when using per-hop behavior in QoS? (Choose two.)

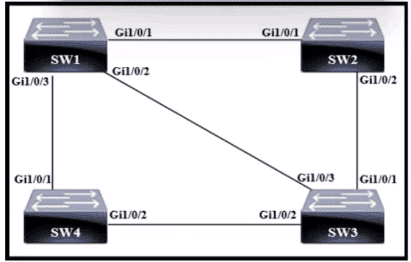
Refer to the exhibit. An LACP EtherChannel between two directly connected switches is in the configuration process.
Which command must be configured on switch SW2’s Gi0/1-2 interfaces to establish the channel to SW1?