Cisco 200-301 - Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1
Which JSON data type is an unordered set of attribute- value pairs?
What prevents a workstation from receiving a DHCP address?
Refer to the exhibit.
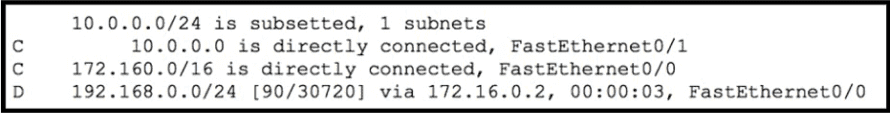
Which route type does the routing protocol Code D represent in the output?
Refer to the exhibit.
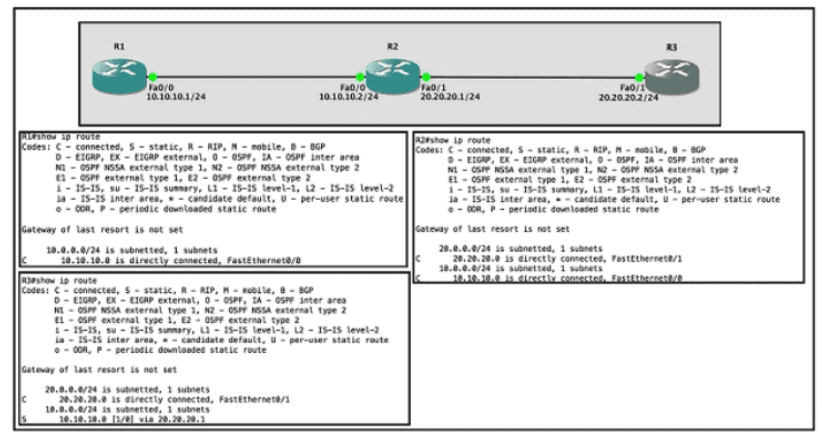
Router R1 Fa0/0 is unable ping router R3 Fa0/1.
Which action must be taken in router R1 to help resolve the configuration issue?
Which type of organization should use a collapsed-core architecture?
Which mode must be set for APs to communicate to a Wireless LAN Controller using the Control and Provisioning of Wireless Access Points (CAPWAP) protocol?
Which command must be entered when a device is configured as an NTP server?
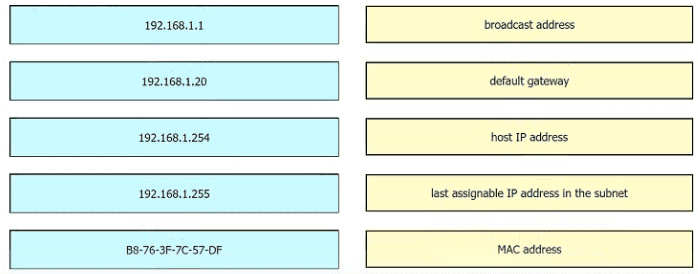
Refer to the exhibit.

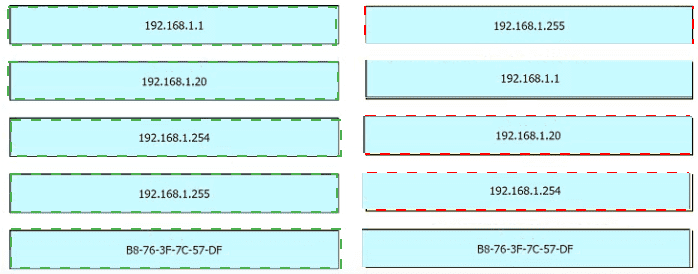
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.
How does a Cisco Unified Wireless network respond to Wi-Fi channel overlap?
R1 has learned route 10.10.10.0/24 via numerous routing protocols. Which route is installed?
What are two benefits of FHRPs? (Choose two.)
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closer? (Choose two.)
Which communication interaction takes place when a southbound API Is used?
Refer to the exhibit.

An engineer deploys a topology in which R1 obtains its IP configuration from DHCP. If
the switch and DHCP server configurations are complete and correct. Which two sets of commands must be configured on R1 and R2 to complete the task? (Choose two)
Refer to the exhibit.
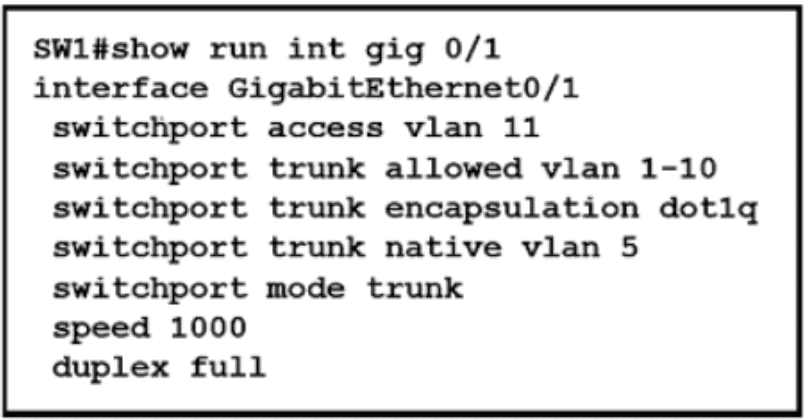
Which action is expected from SW1 when the untagged frame is received on the GigabitEthernet0/1 interface?
Which two primary drivers support the need for network automation? (Choose two.)
Refer to the exhibit.
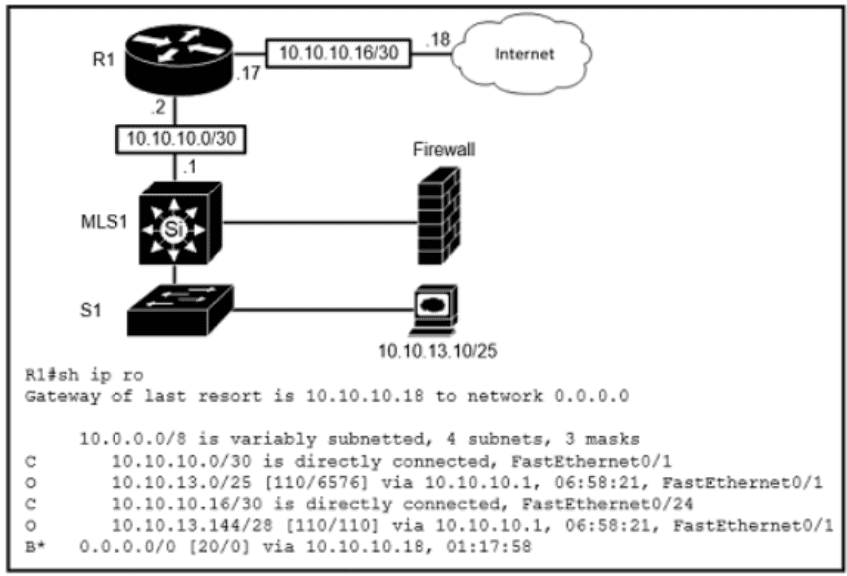
Which route type is configured to reach the internet?
Refer to the exhibit.

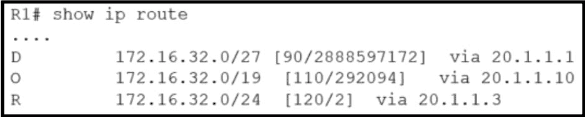
Router R1 is running three different routing protocols. Which route characteristic is used by the router to forward the packet that it receives for destination IP 172.16.32.1?
A wireless administrator has configured a WLAN; however, the clients need access to a less congested 5-GHz network for their voice quality. What action must be taken to meet the requirement?
Which 802.11 frame type is indicated by a probe response after a client sends a probe request?
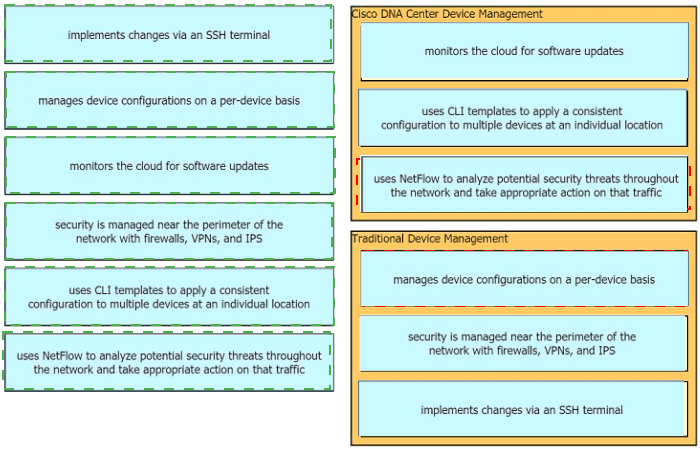
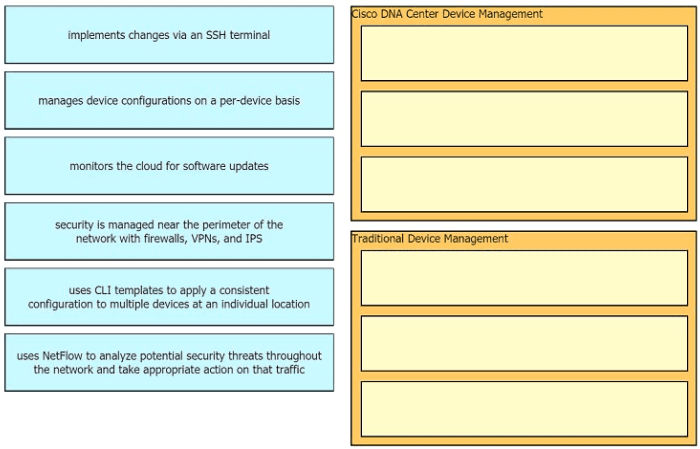
Drag the descriptions of device management from the left onto the types of device management on the right.
Which device separates networks by security domains?
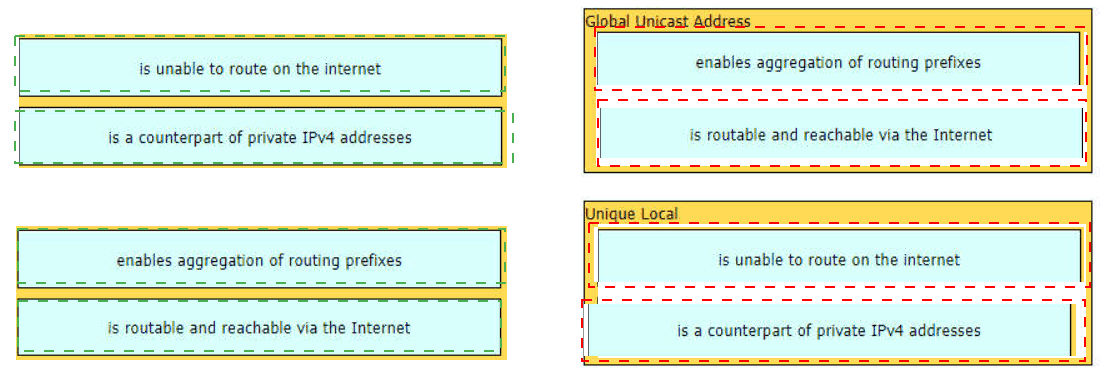
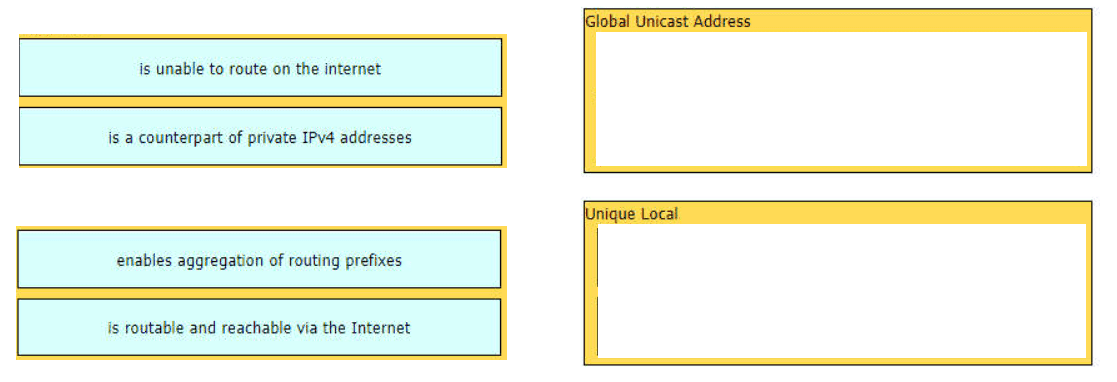
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
What is a specification for SSIDS?
Company has decided to require multifactor authentication for all systems. Which set of parameters meets the requirement?
What is the difference between an IPv6 link-local address and a unique local address?
What does the implementation of a first-hop redundancy protocol protect against on a network?
A network engineer must configure an interface with IP address 10.10.10.145 and a subnet mask equivalent to 11111111.11111111.11111111.11111000. Which subnet mask must the engineer use?
How does MAC learning function on a switch?
Refer to the exhibit.

Clients on the WLAN are required to use 802.11r. What action must be taken to meet the requirement?
Which Rapid PVST+ feature should be configured on a switch port to immediately send traffic to a connected server as soon as it is active?
Which type of port is used to connect lo the wired network when an autonomous AP maps two VLANs to its WLANs?
What are two reasons lo configure PortFast on a switch port attached to an end host? (Choose two.)
What are two benefits of network automation? (Choose two.)
Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?
Refer to the exhibit.
An engineer executed the script and added commands that were not necessary for SSH and now must remove the commands.
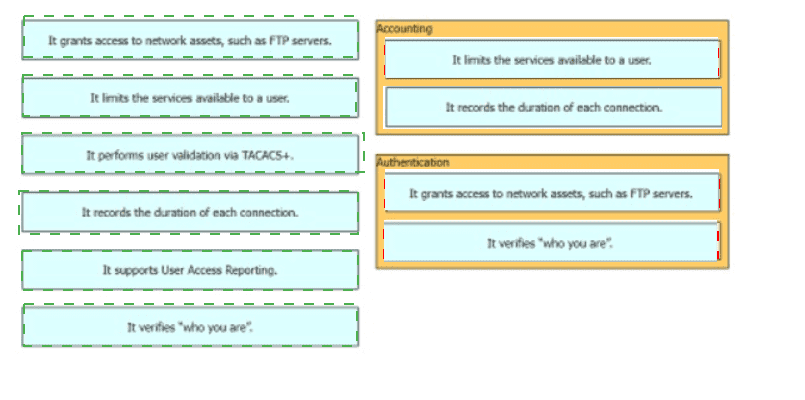
Which two statements distinguish authentication from accounting? (Choose two.)
Refer to the exhibit.

An engineer is configuring a Layer 3 port-channel interface with LACP. The configuration on the first device is complete, and it is verified that both interfaces have registered the neighbor device in the CDP table. Which task on the neighbor device enables the new port channel to come up without negotiating the channel?
An engineer is configuring a switch port that is connected to a VoIP handset. Which command must the engineer configure to enable port security with a manually assigned MAC address of abod-bod on voice VLAN 4?
What is the purpose of configuring different levels of syslog for different devices on the network?
Refer to the exhibit.
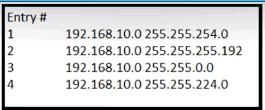
Which entry is the longest prefix match for host IP address 192.168.10.5?
Refer to the exhibit.
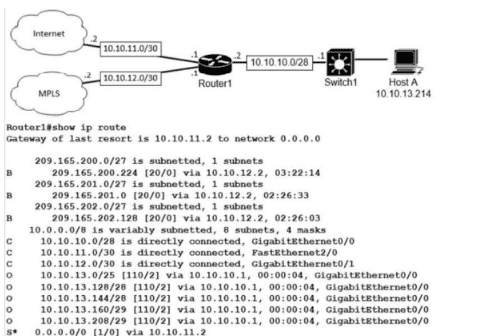
What is the prefix length for the route that Router1 will use to reach Host A?
Drag and drop the statements about AAA services firm the left onto the corresponding AAA services on the right Not all options are used.
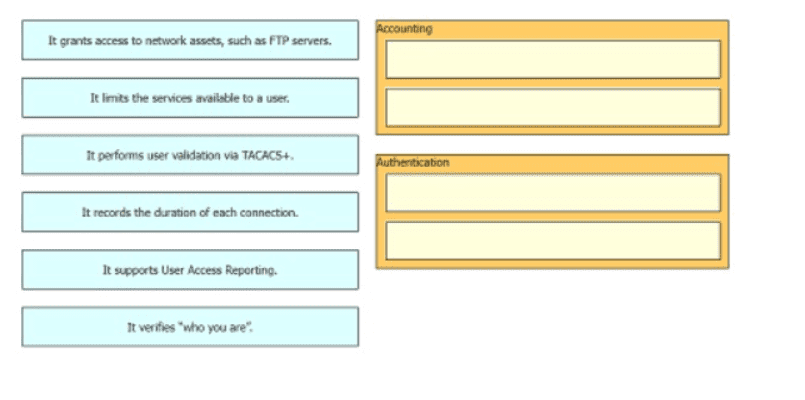
Refer to the exhibit.

An engineer must configure a floating static route on an external EIGRP network. The destination subnet is the /29 on the LAN Interface of R86. Which command must be executed on R14?
What is a reason to implement LAG on a Cisco WLC?
Which event has occurred if a router sends a notice level message to a syslog server?
Which device segregates a network into separate zones that have their own security policies?
What is a benefit of a point-to-point leased line?
A network architect planning a new Wi-Fi network must decide between autonomous, cloud-based, and split MAC architectures. Which two facts should the architect consider? (Choose two.)
Which IPsec mode encapsulates the entire IP packet?