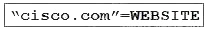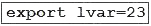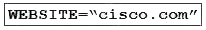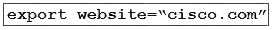Cisco 200-901 - DevNet Associate (DEVASC)
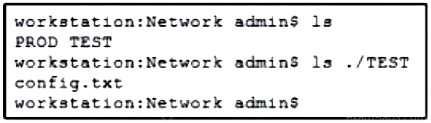
Refer to the exhibit. A network engineer must copy the “config.txt†file from directory TEST to directory PROD. The copied file must also be renamed into “current.txtâ€. Which command must be used to accomplish these tasks?
Refer to the exhibit.
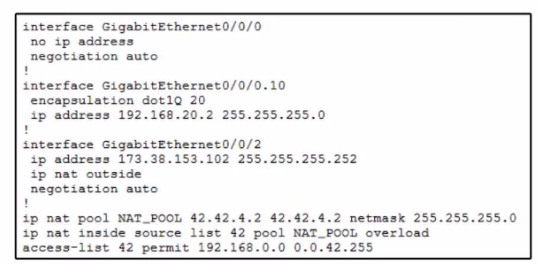
A company recently acquired new IP-based security cameras. After discussion with the engineering team, they decide to segment the security camera traffic m the rest…The engineer assigns the new VLAN 10 for the security camera traffic. After all the devices are configured, it seems as if the cameras cannot access the Internet, .. a few minutes of debugging, the engineer restricts the problem to the router configuration. What is the cause of the issue?

Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the ..call?
A)

B)

C)

D)

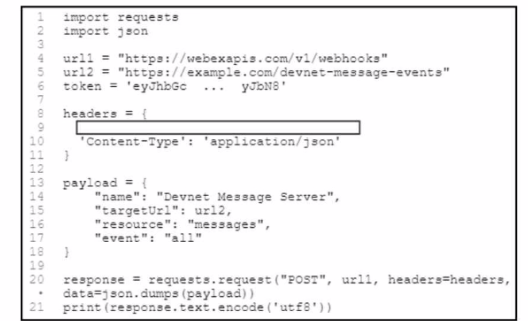
Refer to the exhibit. A developer needs to create a webhook to send all Cisco Webex messages to a third-party tool by using the Cisco Webex API. The developer must Auhenticate with the API before any API calls can be made. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code?
A)

B)

C)

D)

What is a characteristic of the Cisco Finesse platform?
Refer to the exhibit.
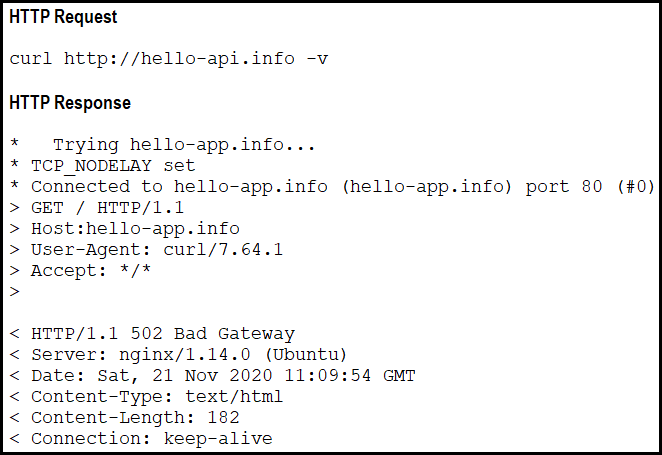
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
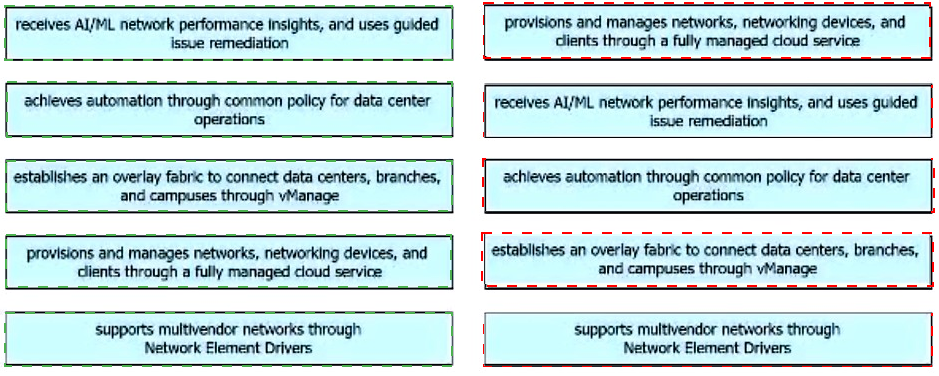
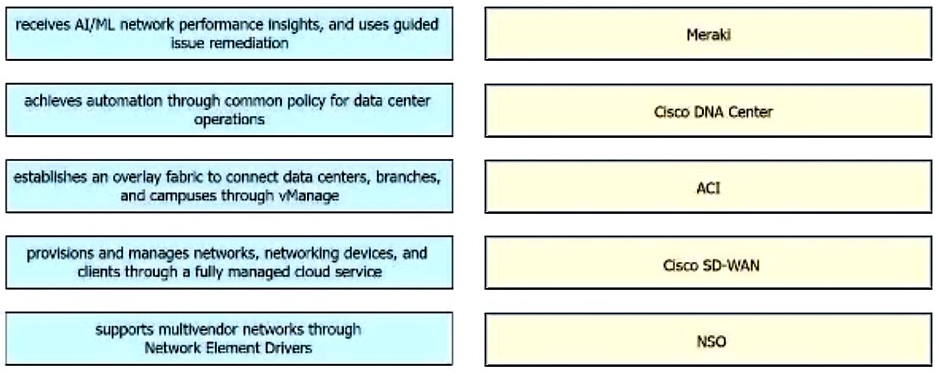
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
A developer is running an application that connects to the Cisco website and collects data. The application will be hosted in a local data center and the data will need to be collected on a frequent basis. The application client requires certain environmental variables to be set before the run. Which Bash command sets the environmental variables for a Linux system?
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
Which protocol is used for clock synchronization between network devices?