ECCouncil 212-82 - Certified Cybersecurity Technician (CCT)
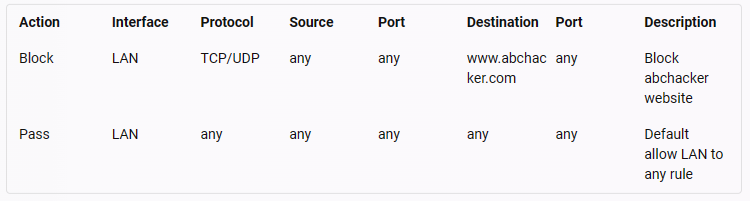
A pfSense firewall has been configured to block a web application www.abchacker.com. Perform an analysis on the rules set by the admin and select the protocol which has been used to apply the rule.
Hint: Firewall login credentials are given below:
Username: admin
Password: admin@l23
As a cybersecurity technician, you were assigned to analyze the file system of a Linux image captured from a device that has been attacked recently. Study the forensic image'Evidenced.img" in the Documents folder of the "Attacker Machine-1" and identify a user from the image file. (Practical Question)
A software company is developing a new software product by following the best practices for secure application development. Dawson, a software analyst, is checkingthe performance of the application on the client's network to determine whether end users are facing any issues in accessing the application.
Which of the following tiers of a secure application development lifecycle involves checking the performance of the application?
Hotel Grande offers luxury accommodations and emphasizes top-notch service for its guests. One such service is secure, high-speed Wi-FI access In every room. The hotel wishes to deploy an authentication method that would give individual guests a seamless experience without compromising security. This method should ideally provide a balance between convenience and strong security. Which of the following should Hotel Grande use?
in a security incident, the forensic investigation has isolated a suspicious file named "security_update.exe". You are asked to analyze the file in the Documents folder of the"Attacker Machine-1" to determine whether it is malicious. Analyze the suspicious file and identify the malware signature. (Practical Question)
Giovanni, a system administrator, was tasked with configuring permissions for employees working on a new project. Hit organization used active directories (ADs) to grant/deny permissions to resources Giovanni created a folder for AD users with the required permissions and added all employees working on the new project in it. Identify the type of account created by Giovanni in this scenario.
As the director of cybersecurity for a prominent financial Institution, you oversee the security protocols for a vast array of digital operations. The institution recently transitioned to a new core banking platform that integrates an artificial intelligence (Al)-based fraud detection system. This system monitors real-time transactions, leveraging pattern recognition and behavioral analytics.
A week post-transition, you are alerted to abnormal behavior patterns in the Al system. On closer examination, the system is mistakenly flagging genuine transactions as fraudulent, causing a surge in false positives. This not only disrupts the customers' banking experience but also strains the manual review team. Preliminary investigations suggest subtle data poisoning attacks aiming to compromise the Al's training data, skewing its decision-making ability. To safeguard the Al-based fraud detection system and maintain the integrity of your financial data, which of the following steps should be your primary focus?
A global financial Institution experienced a sophisticated cyber-attack where attackers gained access to the internal network and exfiltrated sensitive data over several months. The attack was complex, involving a mix of phishing, malware, and exploitation of system vulnerabilities. Once discovered, the institution initiated its incident response process. Considering the nature and severity of the incident, what should be the primary focus of the incident response team's initial efforts?
An employee was fired from his security analyst job due to misconduct. While leaving, he installed a Trojan server on his workstation at 172.30.20.75. As an ethical hacker, you are asked to identify and connect to the Trojan server and explore available files. Enter the name of the VBScript file located in the Pictures folder of the workstation. Hint: You can use one of the Ttojan client applications available at "Z:\CCT-Tools\CCT Module 01 Information SecurityThreats and Vulnerabilities\Remote Access Ttojans (RAT)" of Attacker Machine-1. (Practical Question)
Gideon, a forensic officer, was examining a victim's Linux system suspected to be involved in online criminal activities. Gideon navigated to a directory containing a log file that recorded information related to user login/logout. This information helped Gideon to determine the current login state of cyber criminals in the victim system, identify the Linux log file accessed by Gideon in this scenario.